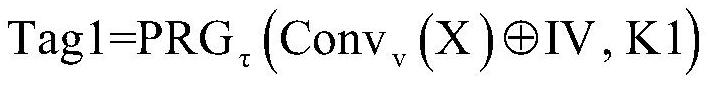Authentication encryption method, verification decryption method and communication method
A technology of authentication encryption and message authentication code, which is applied to key distribution, can solve problems such as poor robustness, inability to provide confidentiality protection and integrity protection of data, and achieve high security, improve communication efficiency, and simple scheme
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
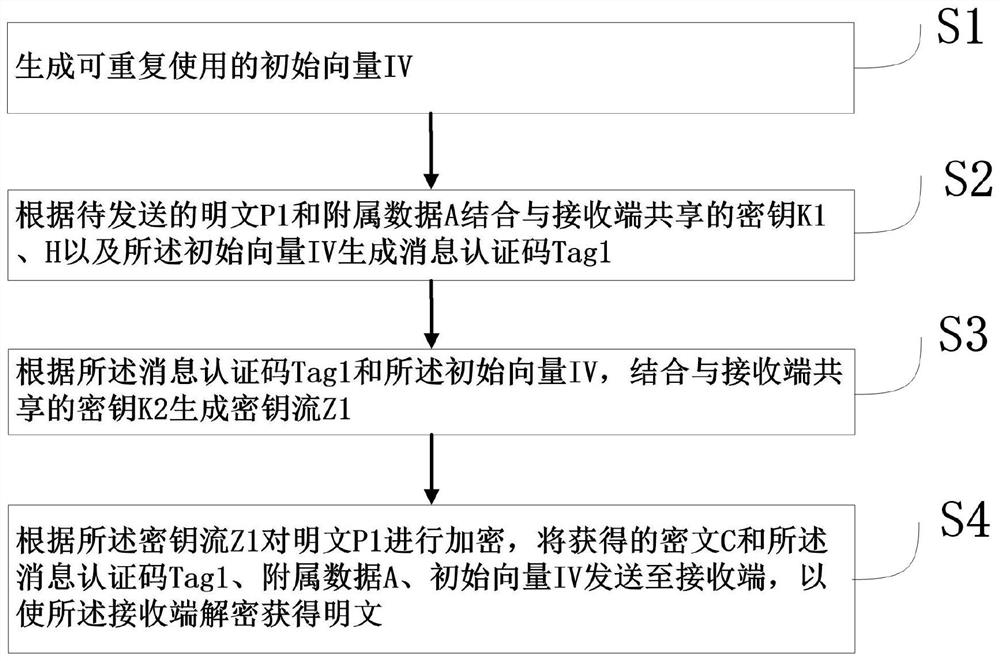
[0077] A specific embodiment of the present invention discloses an authentication and encryption method applied to the sending end, such as figure 1 shown, including the following steps:
[0078] S1. Generate a reusable initial vector IV;
[0079] S2. According to the plaintext P1 to be sent and the attached data A, combine the key K1 and H shared with the receiving end and the initial vector IV to generate a message authentication code Tag1;
[0080] S3. According to the message authentication code Tag1 and the initial vector IV, generate a key stream Z1 in combination with the key K2 shared with the receiving end;
[0081] S4. Encrypt the plaintext P1 according to the key stream Z1, and send the obtained ciphertext C together with the message authentication code Tag1, attached data A, and initial vector IV to the receiving end, so that the receiving end can decrypt it to obtain clear text.
[0082] During implementation, when the sending end and the receiving end conduct ...
Embodiment 2
[0085] Optimizing on the basis of embodiment 1, step S2 further includes:
[0086] S21. Convert the plaintext P1 and the attached data A into N-bit packets respectively, encode the conversion result, and obtain the encoding result Encode(A, P1). Preferably, the Encode (A, P1) is obtained by the following formula
[0087] Encode(A, P1)=Partition(A)||Partition(P1)||L A ||L P1 (1)
[0088] In the formula, L P1 Indicates the 64-bit form of the bit length of the plaintext P1, L A Indicates the 64-bit form of the bit length of the auxiliary data A, and || indicates a splicing operation.
[0089] Exemplarily, N=128.
[0090] Suppose the data string A=1010101010, then the bit length of A is an integer 10, and the 64-bit form of the bit length of A is 0 60 ||1010, L P1 The meaning is similar.
[0091] If the last packet of the plaintext P1 and ancillary data A packets is less than 128 bits, use 0 to fill to 128 bits. For example: if |A|=256, then Partition(A)=A0||A1; if |A|=...
Embodiment 3
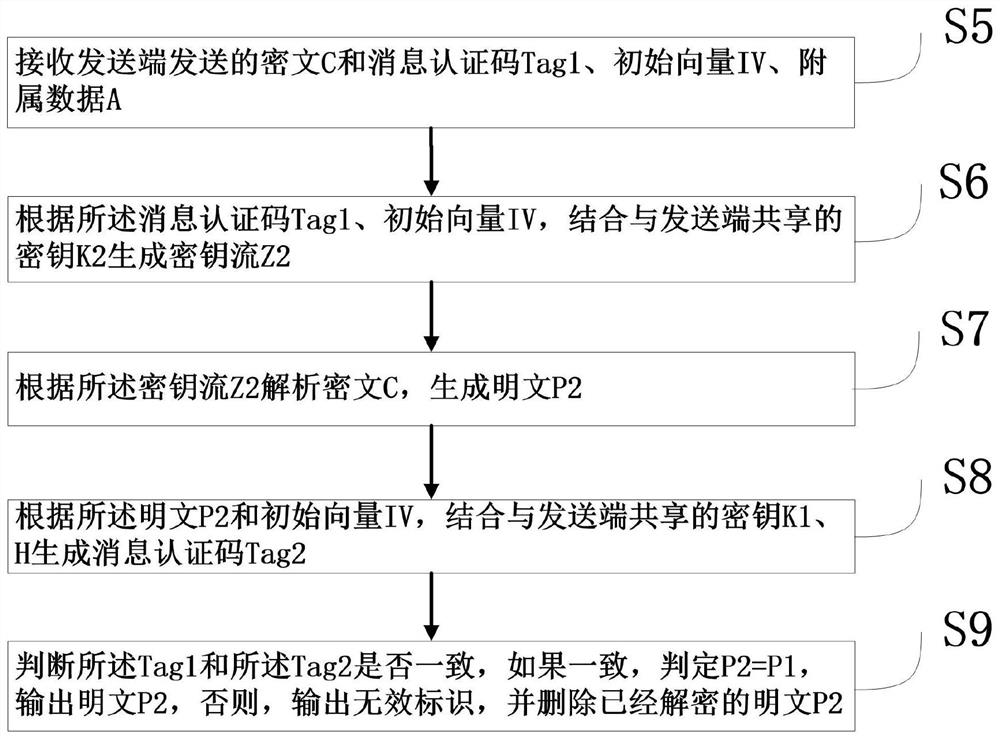
[0117] A specific embodiment of the present invention discloses a verification and decryption method applied to the receiving end corresponding to Embodiment 1, such as figure 2 shown, including the following steps:
[0118] S5. Receive the ciphertext C, message authentication code Tag1, initialization vector IV, and attached data A sent by the sender;
[0119] S6. Generate a key stream Z2 in combination with the key K2 shared with the sender according to the Tag1 and IV;
[0120] S7. Analyzing the ciphertext C according to the Z2 to generate a plaintext P2;
[0121] S8. According to the P2, IV, combined with the key K1, H shared with the sender to generate an authentication code Tag2;
[0122] S9. Determine whether the Tag1 is consistent with the Tag2, and if they are consistent, output plaintext P2 (P2=P1), otherwise, output an invalid identifier, and delete the decrypted plaintext P2.
[0123] It is worth noting that if the received message has not been tampered with, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com