Machine software starting method and device and machine equipment
A software and machine technology, applied in the security field, can solve the problem of easy leakage of source code, and achieve the effect of ensuring security and copyright, and not easy to steal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
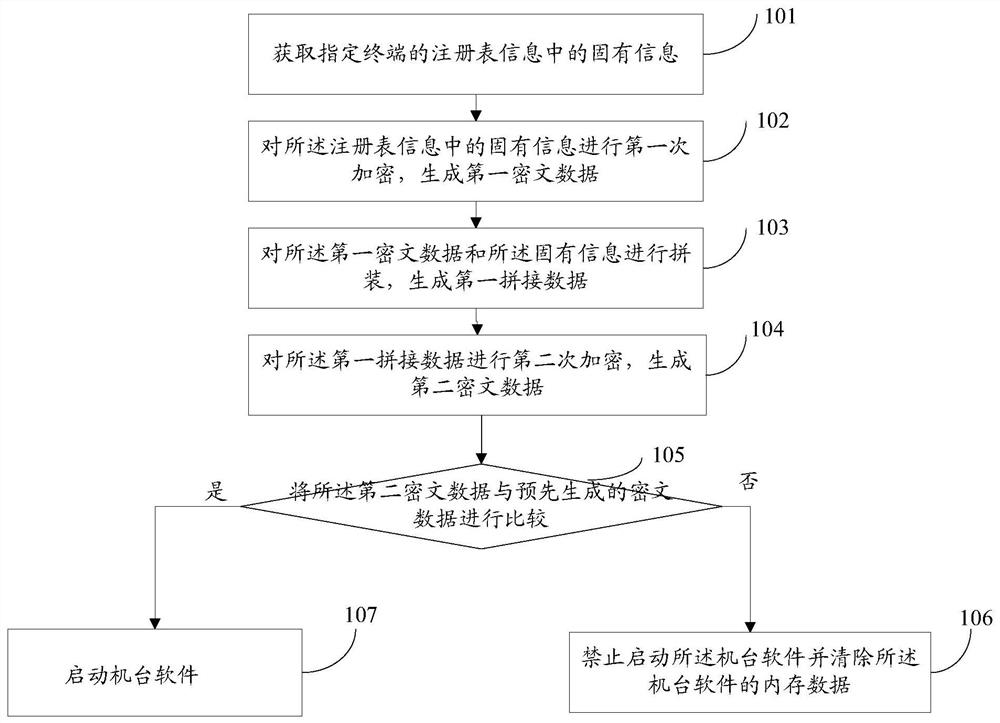
[0043] refer to figure 1 , which shows a flow chart of a machine software startup method described in the embodiment of the present application, specifically including:
[0044] Step 101: Obtain inherent information in registry information of a specified terminal.
[0045] In practical applications, when the executable file of the machine software is deployed on the terminal, the inherent information in the registry information of the specified terminal is obtained, and then the inherent information is encrypted twice, thus ensuring that only one terminal is installed and corresponds to the terminal executable file.
[0046] Inherent information generally refers to information that will not change in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com