Geographic coordinate shape-preserving encryption method
A technology of geographic coordinates and encryption methods, applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
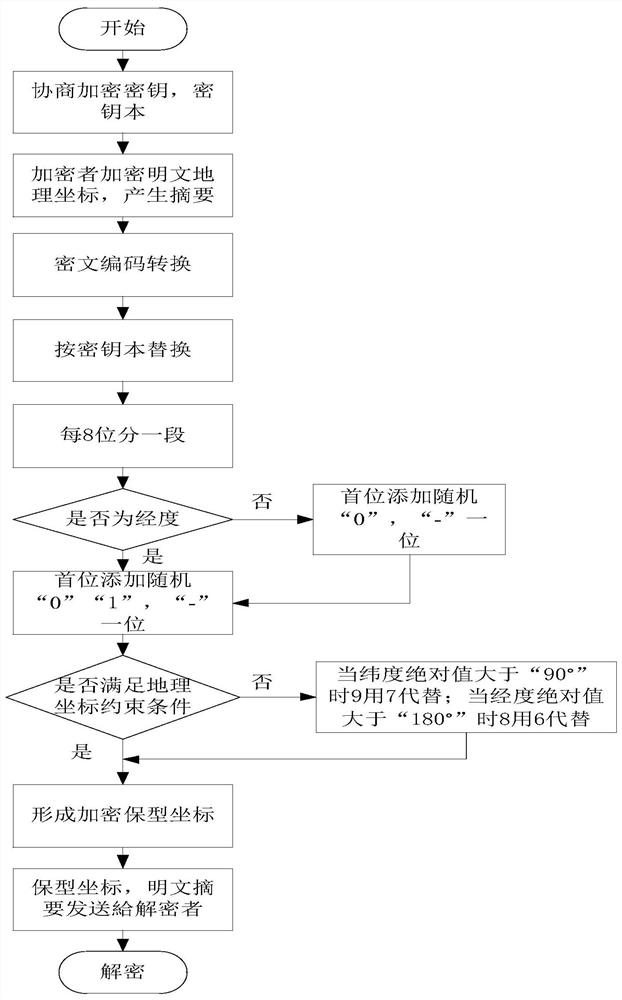
[0040] The present invention will be further described with national standards SM2 and SM4 below, but they are not intended to limit the present invention.
[0041] Initialization: Determine the encryption algorithm and system key parameters.
[0042] The preferred encryption algorithm is the national standard SM2, SM4. SM2 is used for encrypted transmission of encryption key and key book. SM4 is used to encrypt geographic coordinates.
[0043] Design keybook: Design the keybook to ensure that the numbers of geographic coordinates (0-9) are evenly distributed. Considering the constraints of the size range of geographic coordinates, it is preferable not to appear the numbers "6" and "7" when designing the keybook. When the absolute value of latitude is greater than "90°", 9 is replaced by 7; when the absolute value of longitude is greater than "180°", 8 is replaced by 6.
[0044] ciphertext binary replace 0000 20 0001 31 0010 42 0011 53 0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com