Server security event auditing method based on flow data analysis
A technology for server security and traffic data, applied in the field of server security event auditing based on traffic data analysis, it can solve the problems of low security event audit efficiency and reduce server security performance, so as to improve security performance, avoid security risks, and strengthen server systems Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] A server security event auditing method based on traffic data analysis proposed by the present invention, the method steps are as follows:
[0034] S1. Establish a third-party server security event audit system;
[0035] S2. Synchronously mirror the real-time traffic data of the server to the third-party server security event audit system, and back it up;
[0036] S3. Collect, classify and analyze the characteristic data flow of the traffic data, and generate corresponding monitoring nodes for each group of characteristic data;
[0037] S4. The monitoring node monitors and observes the flow trajectory of the characteristic data stream in the whole process, and locates and tracks it with the cooperation of the packet capture tool when a suspicious process and connection occur;
[0038] S5. The third-party server security event audit system analyzes the suspicious behavior, quantifies its impact, predicts the security risk of the suspicious data flow, and then classifies...
Embodiment 2
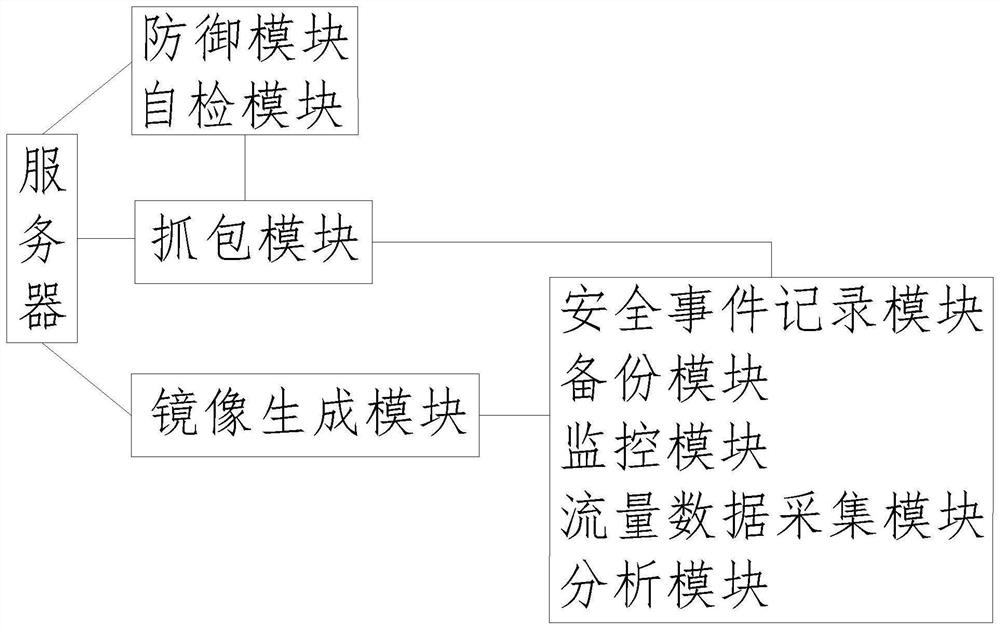
[0045] like figure 1 As shown, the present invention further proposes a third-party server security event audit system, the system includes a security event recording module, a backup module, an image generation module, a monitoring module, a traffic data collection module, a packet capture module, an analysis module, a defense module and an automatic Check module.
[0046] In an optional embodiment, the image generation module, the packet capture module, the defense module, and the self-checking module are connected to the server through a network; the backup module, the monitoring module, the traffic data collection module, and the analysis module are all connected to the image generation module through the network. ; The analysis module is connected to the network of the packet capture module at the same time; the packet capture module is also connected to the network of the defense module and the self-checking module.
[0047] In an optional embodiment, the analysis modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com