Extensible DDoS defense method and system
A defense system and purpose technology, applied in the field of scalable DDoS defense methods and systems, can solve the problems of complex changes, limited cluster size, poor scalability, etc., and achieve the effect of increasing the number of nodes, improving scalability, and reducing repetitive workloads
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
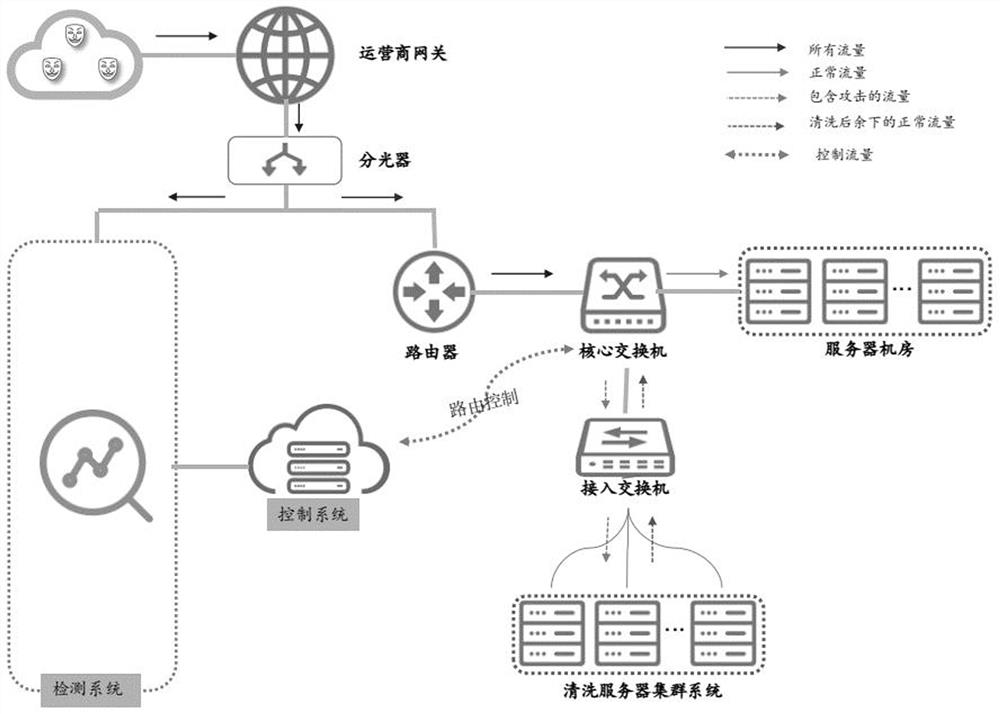
[0038] see image 3 , image 3 It is a schematic flowchart of a method for implementing a scalable DDoS defense disclosed by an embodiment of the present invention. Wherein, the method for implementing scalable DDoS defense can be applied to a DDoS defense system, and the DDoS defense system includes an access switch, a core switch, and a cleaning server controlled by routing. For the specific implementation of the DDoS defense system, the embodiments of the present invention Do limit. Such as image 3 As shown, the method for implementing scalable DDoS defense may include the following operations:
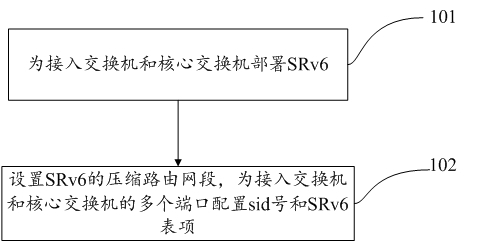
[0039] 101. Deploy SRv6 for access switches and core switches.
[0040] Among them, SR (Segment Routing) is a source routing technology. SRv6 is the application of SR technology on the IPv6 network plane. SRv6 is deployed for access switches and core switches. Network topology information, link state information, and add SRv6 function to it, which can be realized by installin...
Embodiment 2
[0046] see Figure 4 , Figure 4 It is a schematic flowchart of a scalable DDoS defense method disclosed in the embodiment of the present invention. Wherein, the scalable DDoS defense method can be applied in the DDoS defense system, and the DDoS defense system includes an access switch, a core switch and a cleaning server controlled by routing, and the embodiment of the present invention does not limit the specific implementation of the DDoS defense system. Such as Figure 4 As shown, the scalable DDoS defense method can include the following operations:
[0047] Among them, in order to facilitate the description of the specific implementation of this step, combined with Figure 5 The system described is described.
[0048] 201. Detect whether attack traffic currently exists.
[0049] Firstly, it will capture whether there is attack traffic currently, and the detection method can be implemented with reference to the existing technology, which is not the focus of the pres...
Embodiment 3
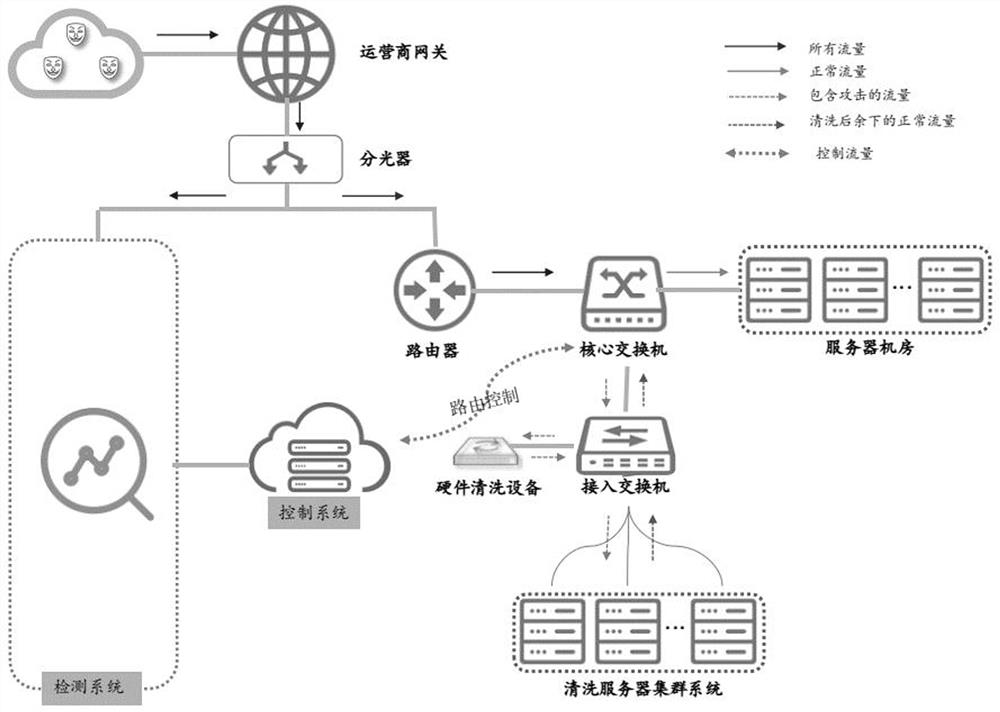
[0063] see Figure 6 , Figure 6 It is a schematic flowchart of a scalable DDoS defense method disclosed in the embodiment of the present invention. Wherein, the scalable DDoS defense method can be applied in the DDoS defense system, and the DDoS defense system includes an access switch, a core switch and a cleaning server controlled by routing, and the embodiment of the present invention does not limit the specific implementation of the DDoS defense system. Such as Figure 6 As shown, the scalable DDoS defense method can include the following operations:
[0064] Among them, in order to facilitate the description of the specific implementation of this step, combined with Figure 7 The system described is described. Among them, the DDoS defense system also includes hardware cleaning machines.
[0065] 301. Detect whether attack traffic currently exists.
[0066]Firstly, it will capture whether there is attack traffic currently, and the detection method can be implemented...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com