Firewall protection improvement method and device, equipment and readable storage medium
A firewall and firewall policy technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as heavy regular maintenance pressure, large number of policies, and reduced operating efficiency, so as to improve protection capabilities and solve configuration errors , the effect of improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
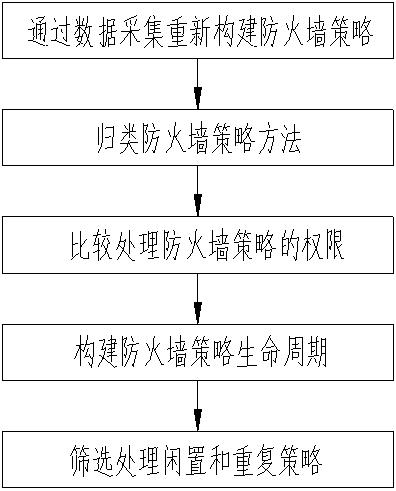
[0027] like figure 1 As shown, the firewall protection enhancement method, which includes:
[0028] Reconstruct firewall policies through data collection;
[0029] Categorize firewall policy methods;
[0030] Compare permissions to process firewall policies;
[0031] Build firewall policy lifecycle;
[0032] Filtering handles idle and duplicate policies.
[0033] Firewall protection lifting device, which includes:
[0034] The reconstruction module is used to reconstruct the firewall policy through data collection, that is, to simulate the management of the firewall through the terminal, and to collect and reconstruct the firewall policy through data decoding;
[0035] The classification module is used to classify the firewall policy method, that is, based on the firewall security protection object, to realize the classification and arrangement of the protection policy method with IP, protocol, application, etc. as the main body;
[0036] The comparison module is used to...
Embodiment 2
[0043] like figure 1 As shown, the firewall protection enhancement method, which includes:
[0044] Reconstruct firewall policies through data collection;
[0045] Categorize firewall policy methods;
[0046] Compare permissions to process firewall policies;
[0047] Build firewall policy lifecycle;
[0048] Filtering handles idle and duplicate policies.
[0049] The method of reconstructing the firewall policy through data collection includes: simulating the management of the firewall through the terminal, and collecting and reconstructing the firewall policy by means of data decoding.
[0050] The method for classifying firewall policies includes: based on the security protection objects of the firewall, the classification and sorting of protection policy methods with IP, protocol, application, etc. as the main body are realized.
[0051] The comparing and processing the authority of the firewall policy includes: based on the policy objects such as IP, protocol, port, e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com