User authority management method, electronic device and storage medium
A technology of user rights and management methods, which is applied in the field of user rights management, can solve the problems of long time and manpower, reduce production efficiency, and low authentication efficiency, and achieve the effect of improving production efficiency, improving authentication efficiency, and realizing automatic authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
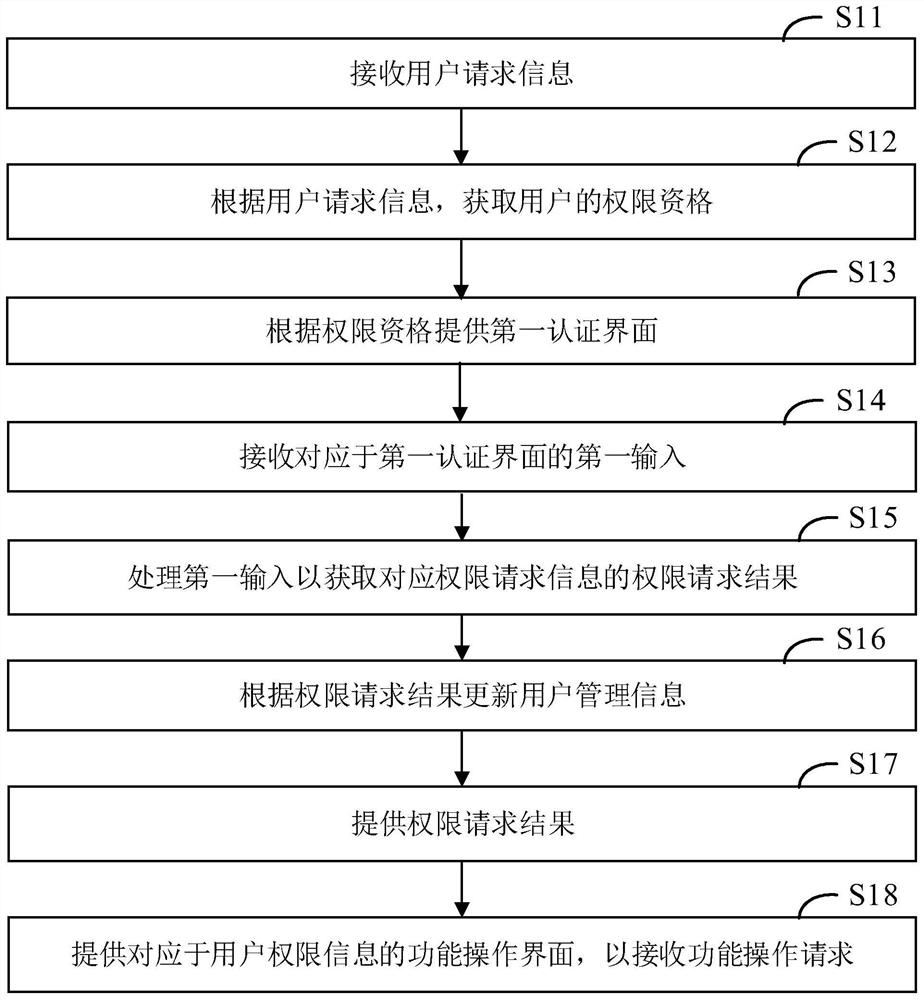
[0096] see figure 2 As shown in FIG. 1 , it is a flowchart of a user rights management method according to an embodiment of the present invention. According to different requirements, the order of the steps in the flowchart can be changed, and some steps can be omitted.
[0097] In one embodiment, the user rights management method is applied in the first electronic device 1 or the second electronic device 2 .
[0098] S11. Receive user request information.
[0099] In one embodiment, the user request information includes at least identity information and permission request information. The identity information may be the user's ID number, employee ID number, or other information sufficient to identify the user. The first electronic device 1 or the second electronic device 2 may receive the user's identity information by receiving a scanned copy of the certificate sent or uploaded by the user, manually inputting a certificate number or other forms.
[0100] In one embodime...
Embodiment 2
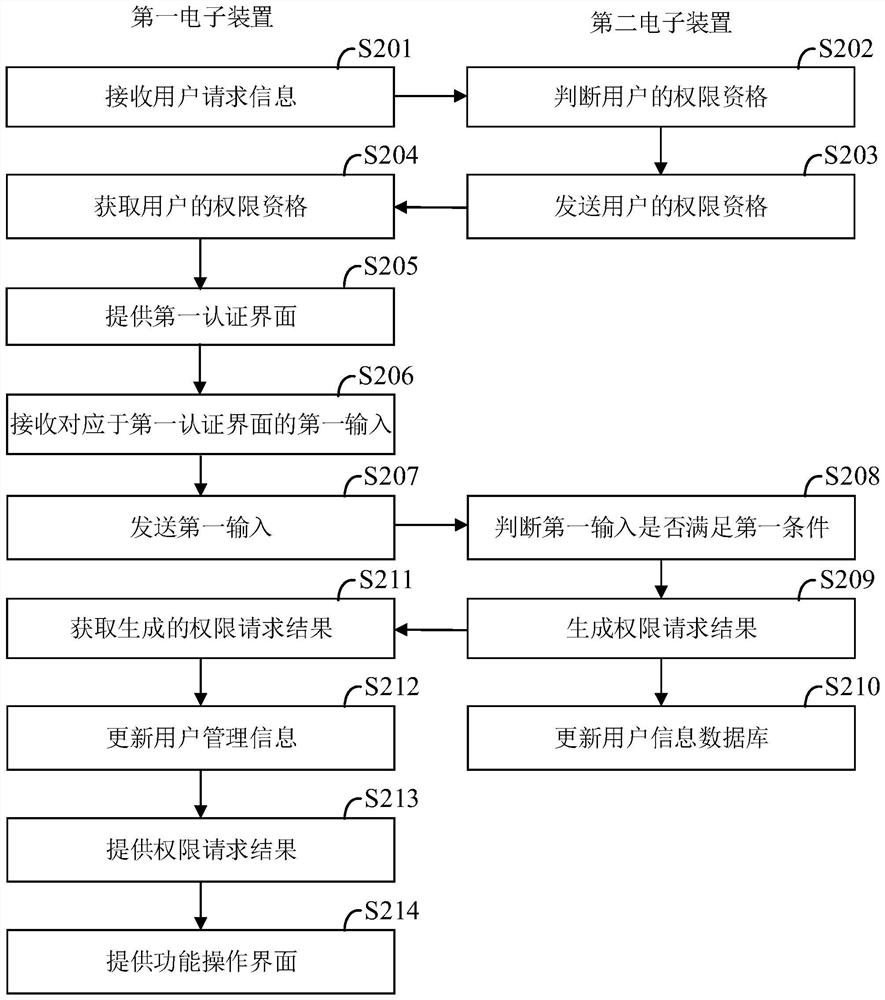
[0129] see image 3 As shown in FIG. 2 , it is a flowchart of a user rights management method provided by an embodiment of the present invention. According to different requirements, the order of the steps in the flowchart can be changed, and some steps can be omitted.
[0130] In one embodiment, the user rights management method is applied in the operating environment formed by the first electronic device 1 and the second electronic device 2 .
[0131] S201. Receive user request information.
[0132] In one embodiment, the user request information includes at least identity information and permission request information. Among them, the identity information is the user's ID number, employee ID number or other information sufficient to identify the user's identity. The first electronic device 1 receives the user's identity information by receiving a scanned document sent or uploaded by the user, manually inputting a document number, or other forms.
[0133] In one embodime...
Embodiment 3
[0177] see Figure 4 As shown in FIG. 2 , it is a flowchart of a user rights management method provided by an embodiment of the present invention. According to different requirements, the order of the steps in the flowchart can be changed, and some steps can be omitted.
[0178] In one embodiment, the user rights management method is applied in the first electronic device 1 .
[0179] S301. Receive user request information.
[0180] In one embodiment, the user request information includes at least identity information and permission request information. Among them, the identity information is the user's ID number, employee ID number or other information sufficient to identify the user's identity. The first electronic device 1 may receive the user's identity information by receiving a scanned document sent or uploaded by the user, manually inputting a document number, or other forms.
[0181] In one embodiment, the permission request information includes at least a permissi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com