A method for displaying it asset risk situational awareness
A situational awareness and asset technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve the problem of not being able to display network attack behaviors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The specific implementation manner of the present invention will be described in detail below in conjunction with the accompanying drawings.
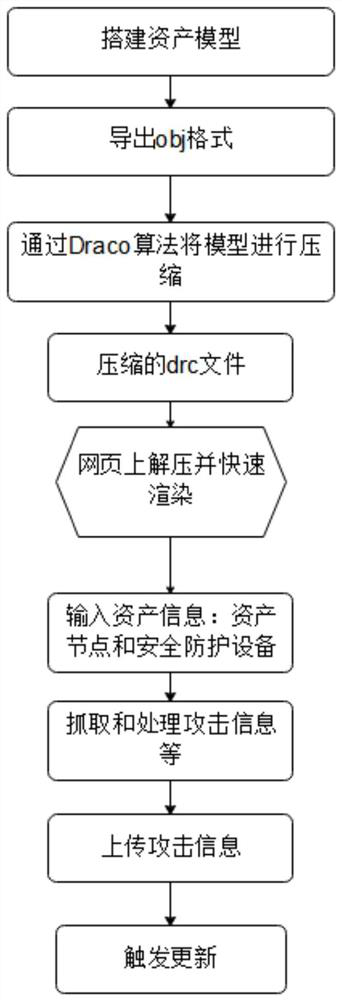
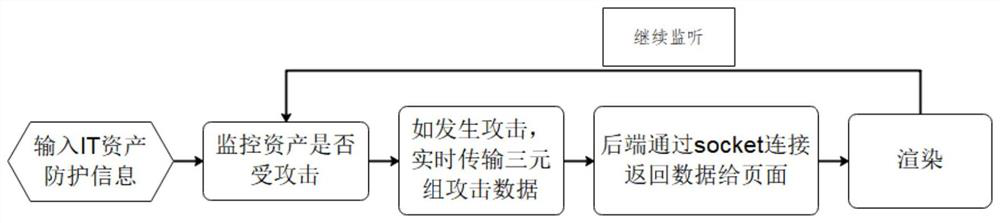
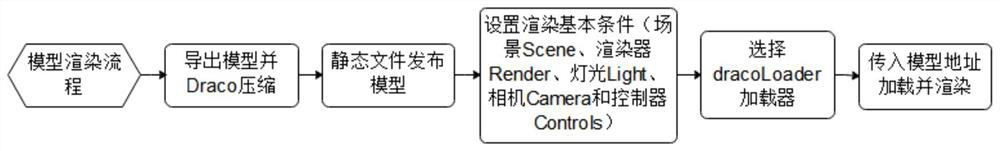
[0029] Such as Figure 1-3 As shown, this example is a method for displaying IT asset risk situation awareness, and its processing flow is as follows figure 1 As shown, the specific implementation steps are as follows:
[0030] S1: According to the basic information established by the input asset model, build the asset model; specifically, first draw the model through 3D drawing software such as 3dMax or c4d according to the basic information, and the LOD needs to be able to distinguish the approximate outline of the server equipment. Element nodes can be reduced to a sphere for illustration.
[0031] Among them, the basic information provided by the present invention includes all computing resources such as IT assets, servers, and personal PCs owned by the enterprise. For each IT asset, it is necessary to record basic informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com