A Reliable Network Steganography Method Based on IP Source Address
A technology of IP address and source address, applied in the field of information hiding, can solve the problems of small hidden capacity, low hidden capacity, increased computing cost and network delay, and achieve the effect of improving concealment and reliable communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
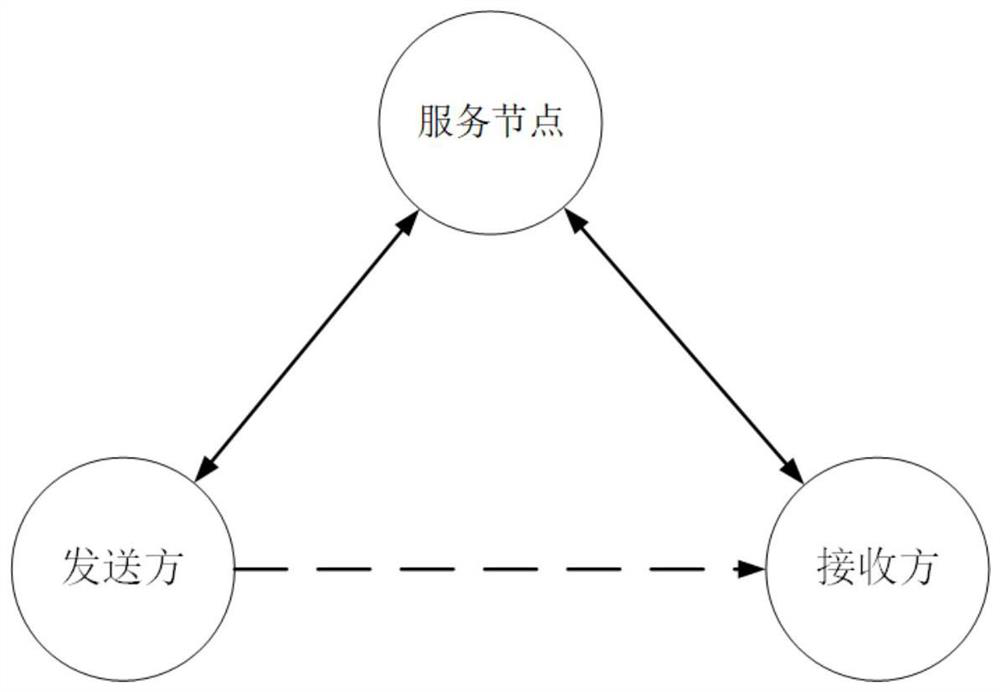
[0049] Such as figure 1 As shown, in order to ensure that the secret message will not be decoded incorrectly due to packet loss, this method establishes a service node. The service node contains at least the following content information: the real IP address of the sender of the secret message, the IP address of the receiver of the secret message, the number of IP data packets used to transmit the secret message, and the communication status of the receiver.
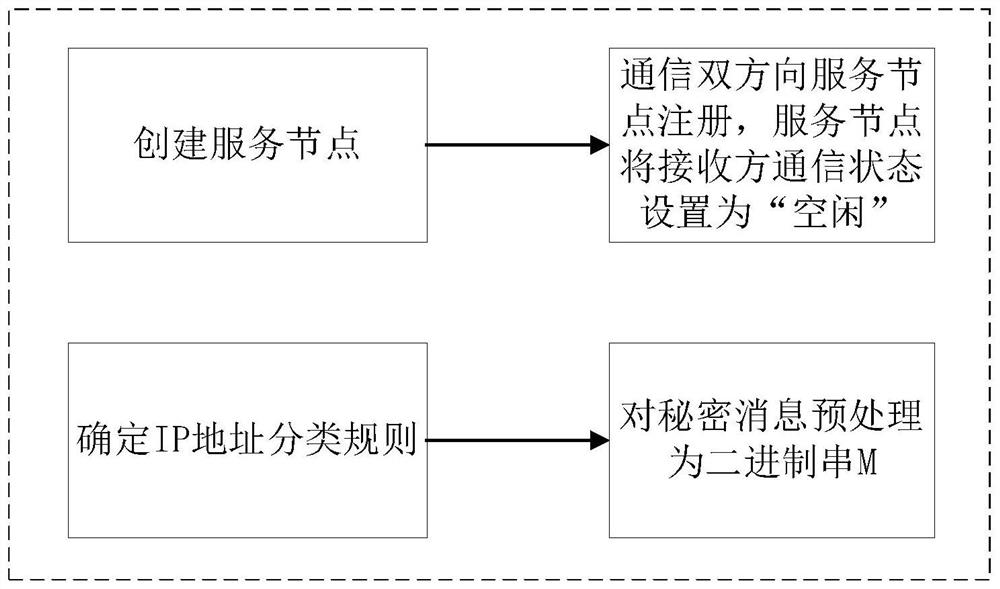
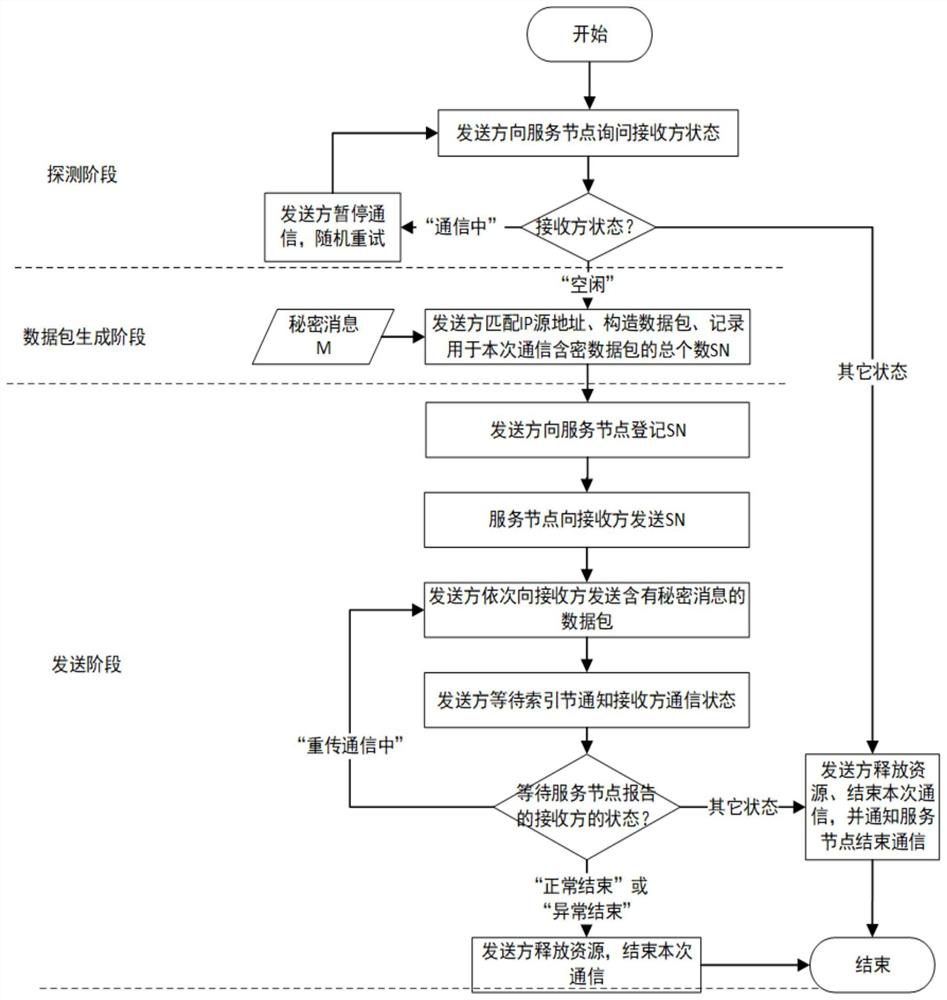
[0050] Such as figure 2 , 3 , 4, this method is divided into three parts: preparation process, embedding process and extraction process. Assuming that the secret message is successfully sent under normal circumstances, the following specific process is given by taking "Time" as an example.
[0051] 1. Preparation process:
[0052]1) Create a service node, which is used to record auxiliary information for sending hidden secret messages. Including: the real IP addresses and communication ports of the sender and recei...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com