Sensitive data synchronization method, device and system, computer equipment and computer readable storage medium
A technology of sensitive data and computer programs, applied in the field of video, can solve problems such as poor user experience, and achieve the effect of ensuring forward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
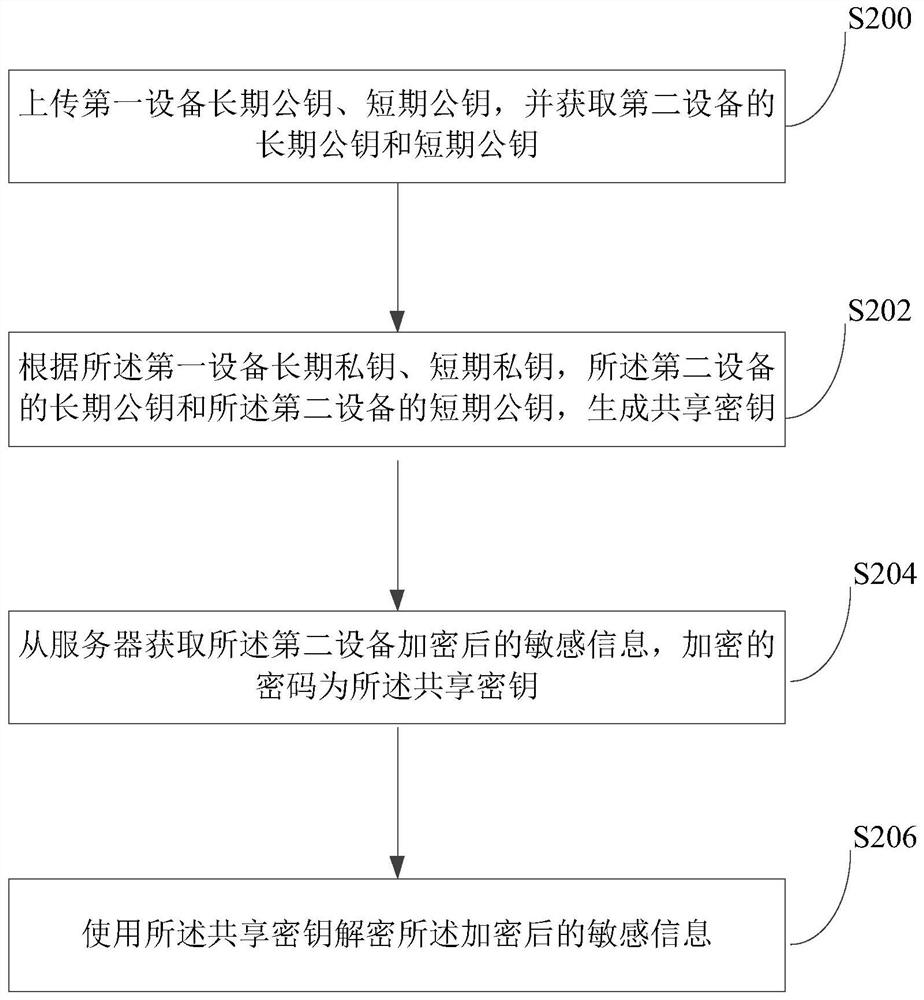
[0055] figure 2 A flowchart of a method for synchronizing sensitive data according to Embodiment 1 of the present application is schematically shown. It can be understood that this method embodiment can be executed in the mobile terminal 13, and the flowchart of this method embodiment is not used to limit the sequence of execution steps.
[0056] Such as figure 2 As shown, the method for synchronizing sensitive data may include steps S200-S206, wherein:
[0057] Step S200, uploading the long-term public key and short-term public key of the first device, and obtaining the long-term public key and short-term public key of the second device;
[0058] Step S202, generating a shared key according to the long-term private key and short-term private key of the first device, the long-term public key of the second device, and the short-term public key of the second device;
[0059] Step S204, obtaining encrypted sensitive information of the second device from the server, where the...
Embodiment 2
[0098] Figure 4 A flow chart of a method for synchronizing sensitive data according to Embodiment 2 of the present application is schematically shown. It can be understood that this method embodiment can be executed in the mobile terminal 13, and the flowchart of this method embodiment is not used to limit the sequence of execution steps.
[0099] Such as Figure 4 As shown, the method for synchronizing sensitive data may include steps S400-S404, wherein:
[0100] Step S400, after receiving the request for synchronizing sensitive data, upload the long-term public key and short-term public key of the second device, and obtain the long-term public key and short-term public key of the first device;
[0101] Step S402, generating a shared key according to the long-term private key and short-term private key of the second device, the long-term public key of the first device, and the short-term public key of the first device;
[0102] Step S404, encrypting the sensitive data wit...
Embodiment 3
[0138] Figure 5 A flowchart of a method for synchronizing sensitive data according to Embodiment 3 of the present application is schematically shown. It can be understood that this method embodiment can be executed in the server 12, and the flowchart of this method embodiment is not used to limit the sequence of execution steps.
[0139] Step S500, receiving the long-term public key and short-term public key of the first device, and sending the long-term public key and short-term public key of the second device to the first device;
[0140] Step S502, receiving the long-term public key and short-term public key of the second device, and sending the long-term public key and short-term public key of the first device to the second device;
[0141] Step S504, receiving the encrypted sensitive information sent by the second device, and sending the encrypted sensitive information to the first device.
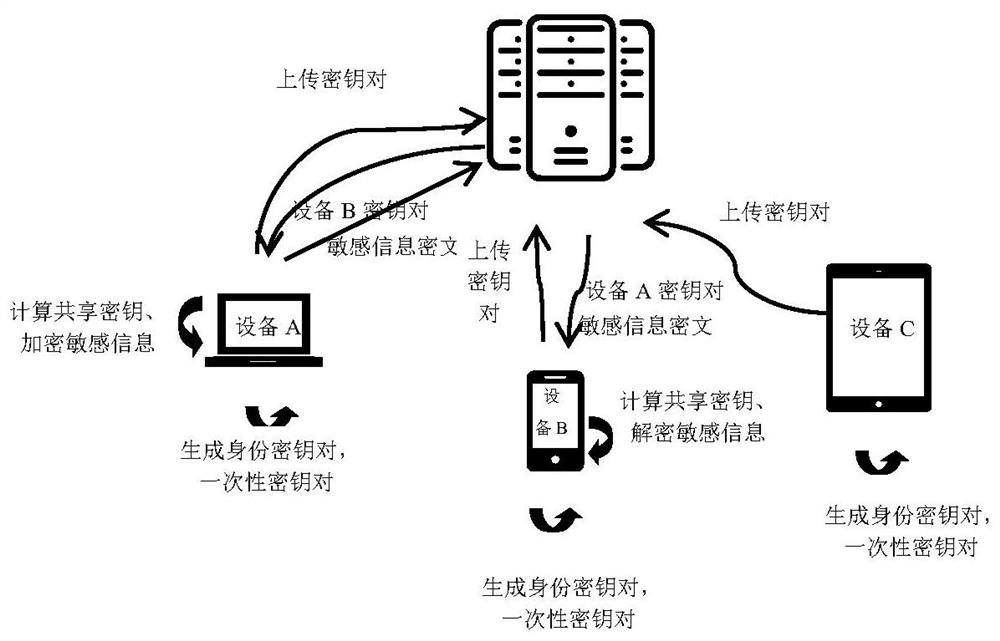
[0142] Specifically, 1. Each device of the user generates an identity key pair...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com