Method for analysis of source texts
A source code and code development technology, applied in the field of data processing devices and data carriers, can solve problems such as time-consuming and expensive development cycles, and achieve the effect of sensitization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
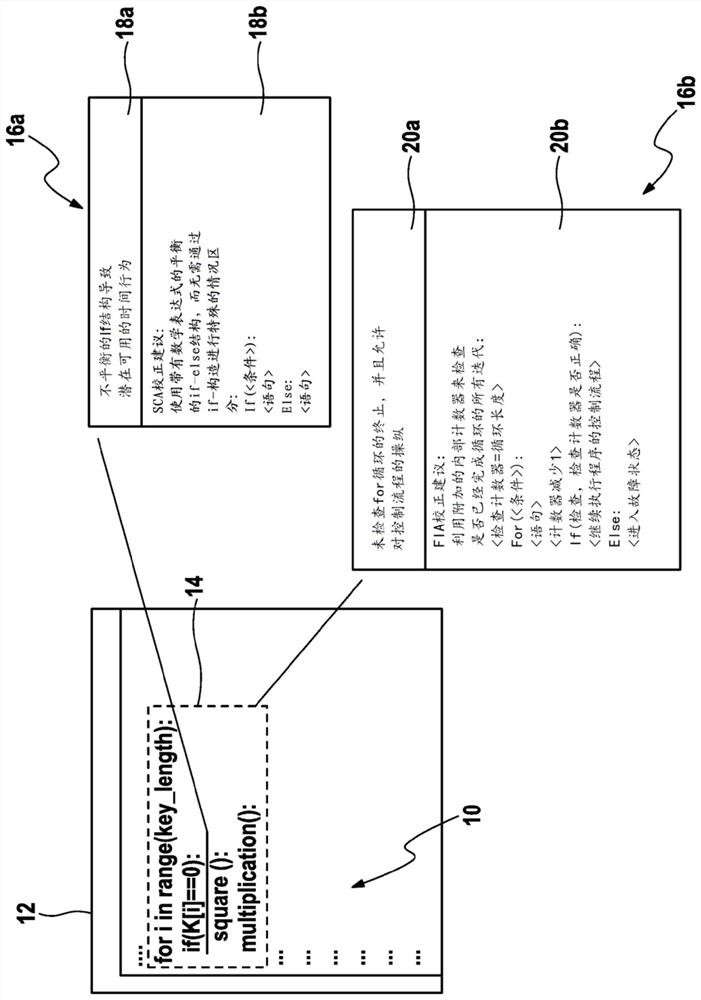
[0024] exist figure 1 The integrated development environment shown in FIG. 2 schematically illustrates an embodiment of the method for analyzing source code 10 according to the present invention.
[0025] The method is performed by a data processing device comprising a processor configured to perform the method described below. The method is based on a computer program product comprising commands which, when executed by the computer, cause the program to carry out the method accordingly.
[0026] During execution of the method, a source code vulnerability 14 is identified in the source code 10 entered by the source code developer. The source code developer enters the source code 10 into the editor 12 via an input device designed as a keyboard. During active source code development, source code vulnerabilities14 are identified in real time without compiling the program.
[0027] Within the scope of the method, source code vulnerabilities 14 that are susceptible to implementa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com