Communication method, system and device based on security gateway
A technology of a security gateway and a communication method, applied in the field of communication methods, systems and equipment based on a security gateway, can solve the problems of transmission security attacks, poor communication service quality, communication data leakage, etc., and achieve enhanced security and accurate transmission. , the effect of reducing business pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment example
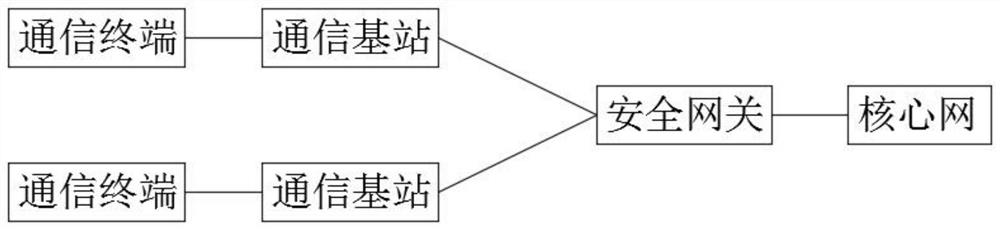
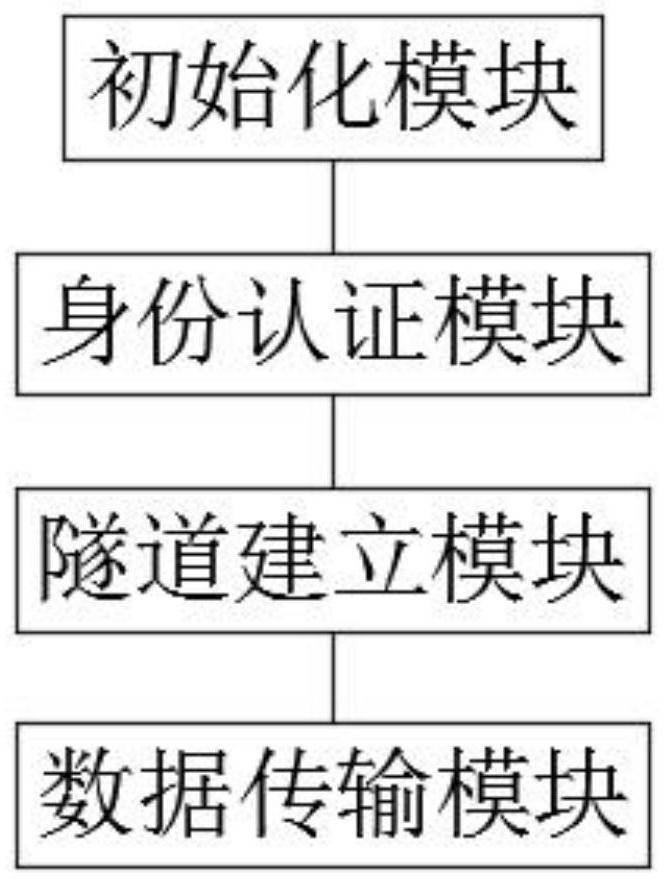
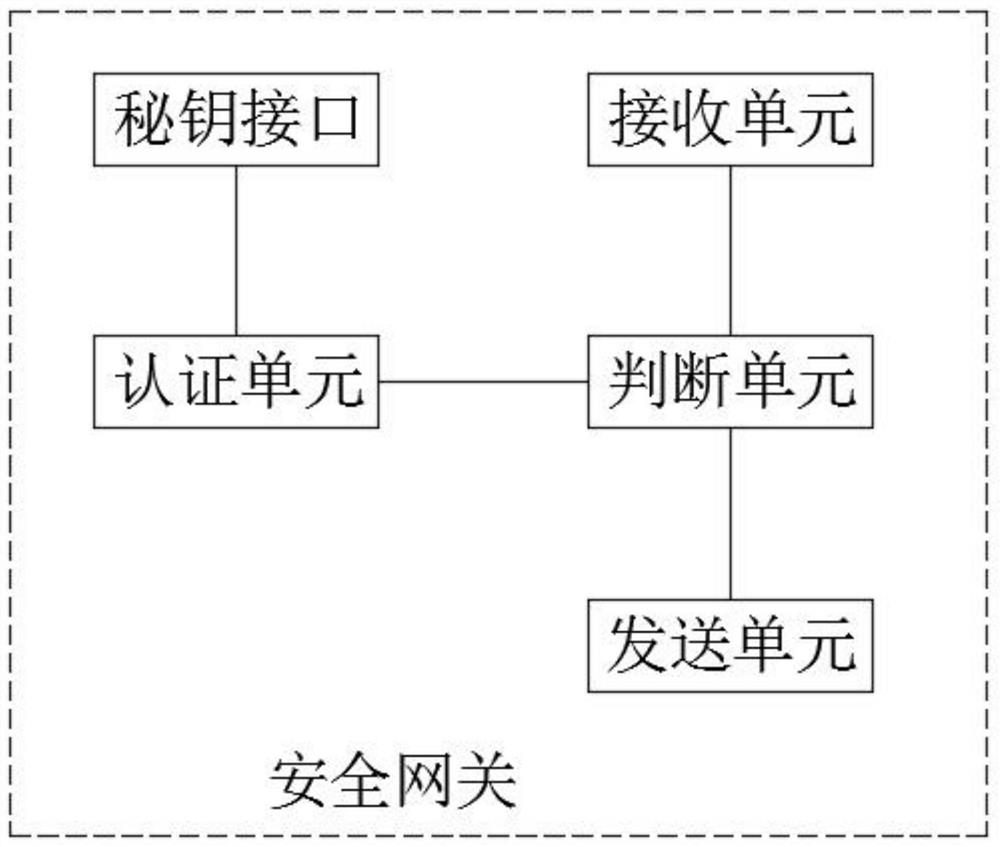
[0047] In a preferred implementation case, a security gateway forms a corresponding encryption key and a digital certificate with at least two communication terminals, so as to realize secure communication between the two communication terminals.
[0048]In a preferred implementation case, in step S2, the secure tunnel is to perform one-way identity authentication or two-way identity authentication based on the SSL protocol through a preset digital certificate between the communication terminal and the security gateway, and establish a VPN encrypted secure tunnel, and the established secure tunnel Only access to specified services and specific operations is allowed, and the broadband standard of the security gateway is the same as that of the communication terminal that has established a secure tunnel with the security gateway.
[0049] In a preferred implementation case, in step S4, the method for judging the security tunnel between the security gateway and the communication t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com