Big data platform defense method for advanced sustainable threat attacks
A big data platform, a technology for defenders, applied in the fields of instruments, character and pattern recognition, electrical components, etc., can solve the problems of concealment, difficulty to find, and APT attack time-consuming
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
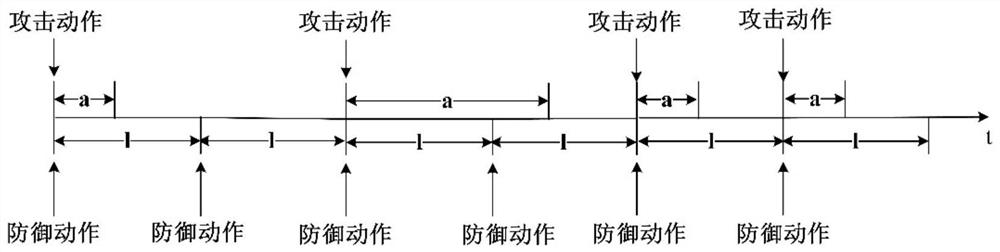
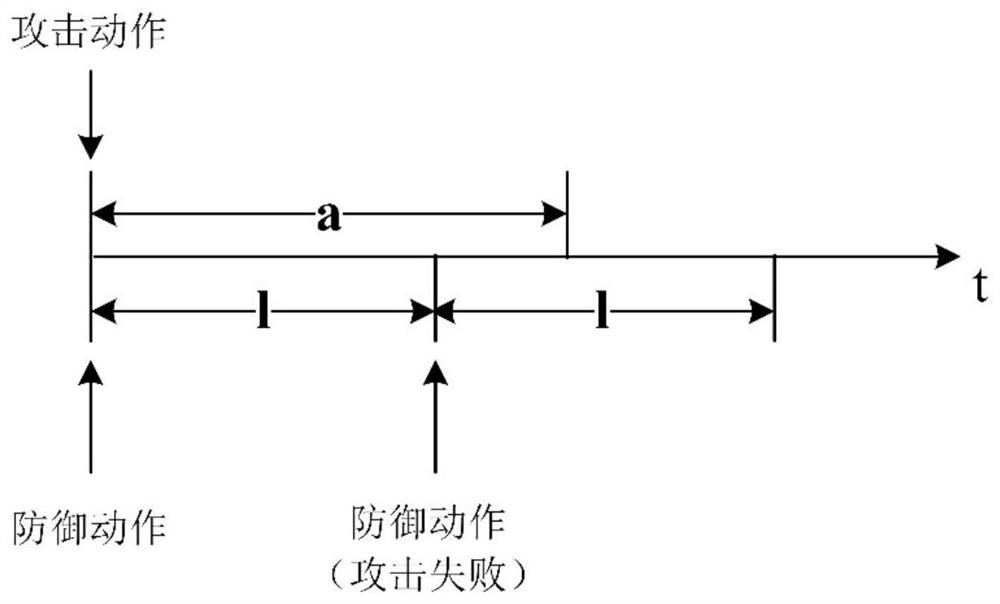
[0046] A big data platform defense method for advanced sustainable threat attacks proposed by the present invention needs to solve the following two problems: 1) Since APT attacks are highly concealed, which method should the defender choose for defense, and how to find hidden APT attack traffic in normal traffic is a problem that must be solved; 2) When an APT attack is detected, what defense strategy the defender should adopt to maximize its own interests is also a problem that must be solved.
[0047] Main realization thought of the present invention is:
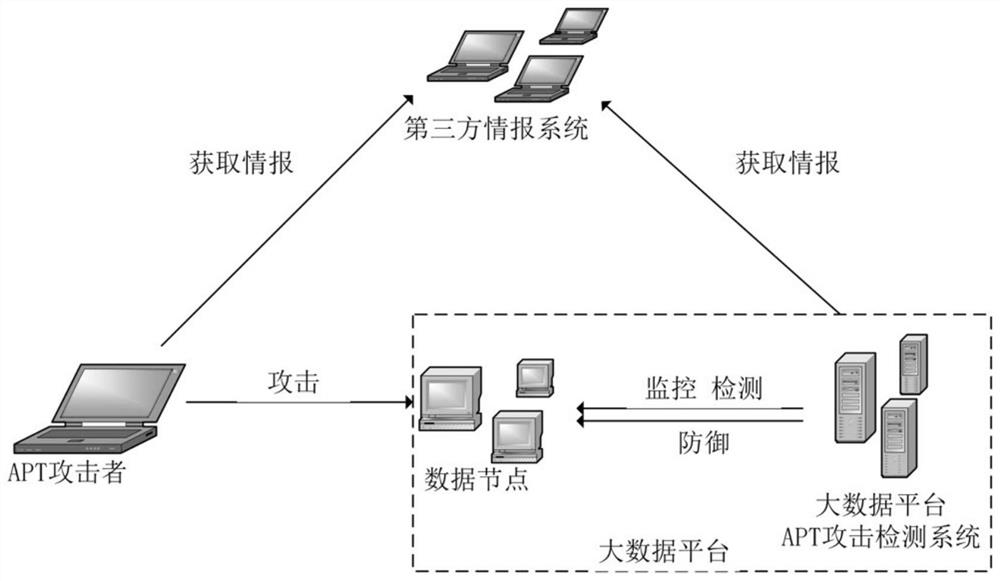
[0048] Such as figure 2 As shown, there are three roles in the model, namely APT attacker, big data platform and third-party intelligence agency. APT attackers will launch attacks on big data platforms, and at the same time obtain intelligence from third-party intelligence agencies to assist attack decisions. The big data platform will use the APT detection and defense system to defend against attacks initiated by attac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com