Method for screening security subset of security-critical software modeling language
A modeling language, screening method technology, applied in the direction of computer security devices, model-driven code, creation/generation of source code, etc., can solve the problem that the security subset cannot meet the safety-critical software, lack of adequacy, necessity and security , the code has security risks and other issues, to ensure the necessity, good interface, and clear functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
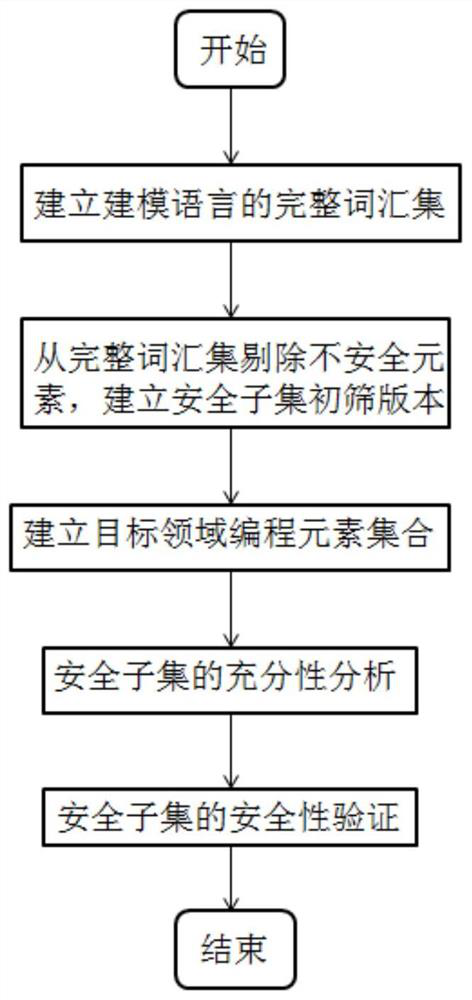
[0023] A method for managing safety-critical software modeling language safety subsets described in the present invention includes: figure 1 The steps shown, specifically:
[0024] (1) Establish a complete vocabulary set of the modeling language according to the instruction manual of the original modeling language;
[0025] (2) Carry out a necessity analysis on the complete vocabulary set of the modeling language, remove unsafe elements from the complete vocabulary set, and establish a preliminary screening version of the safe subset;
[0026] (2.1) Traverse the complete vocabulary set of the modeling language and eliminate elements that cannot generate code;
[0027] (2.2) Traversing the complete vocabulary set of the modeling language, analyzing the icons, input and output interfaces, and usage methods of modeling elements, eliminating ele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com