Method and device for ensuring data security communication of application
A data security, data technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
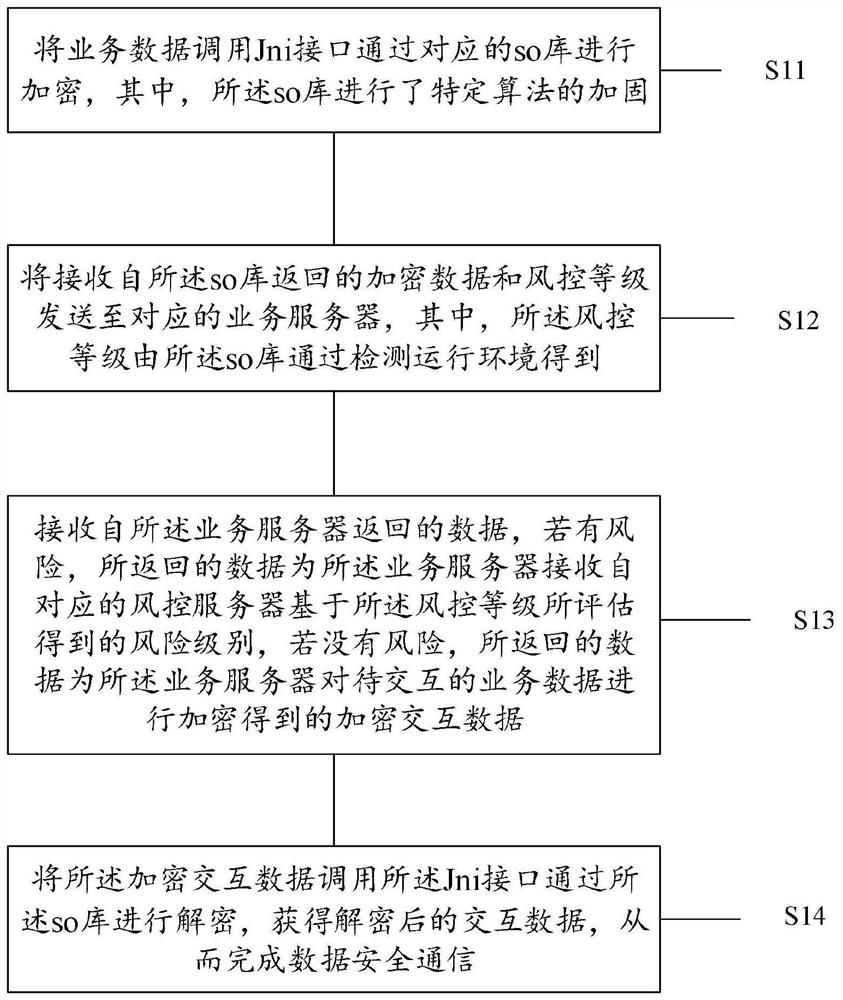
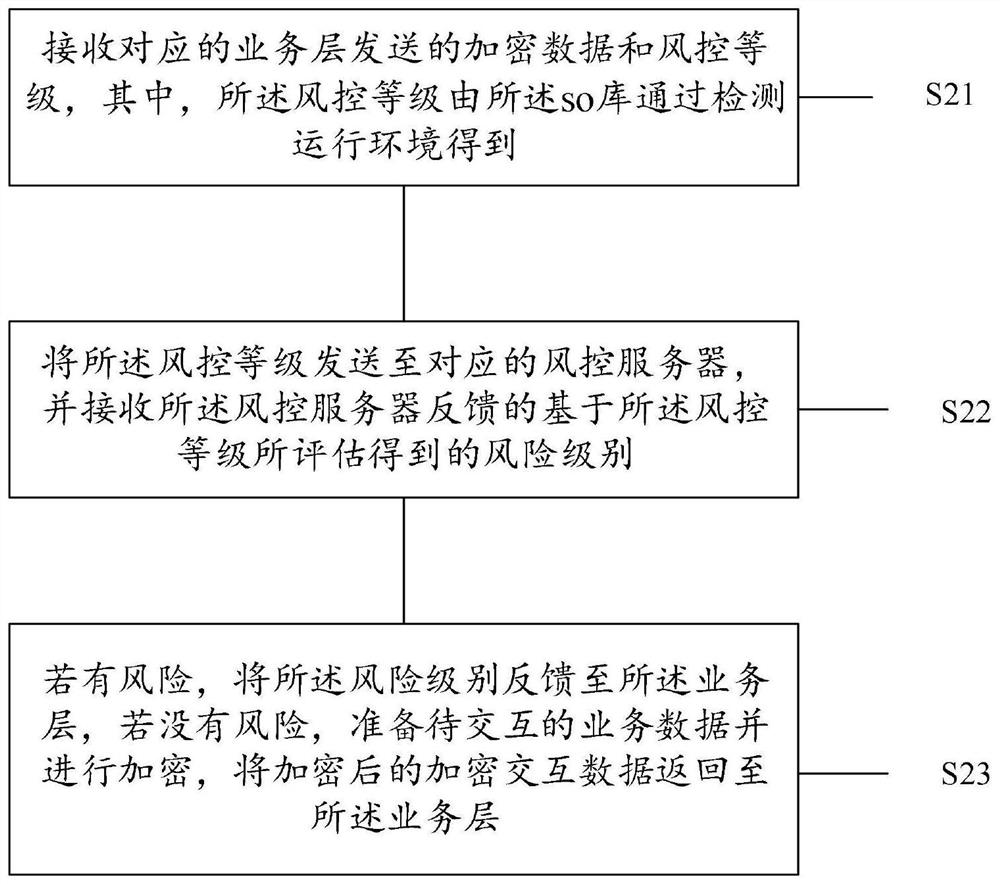
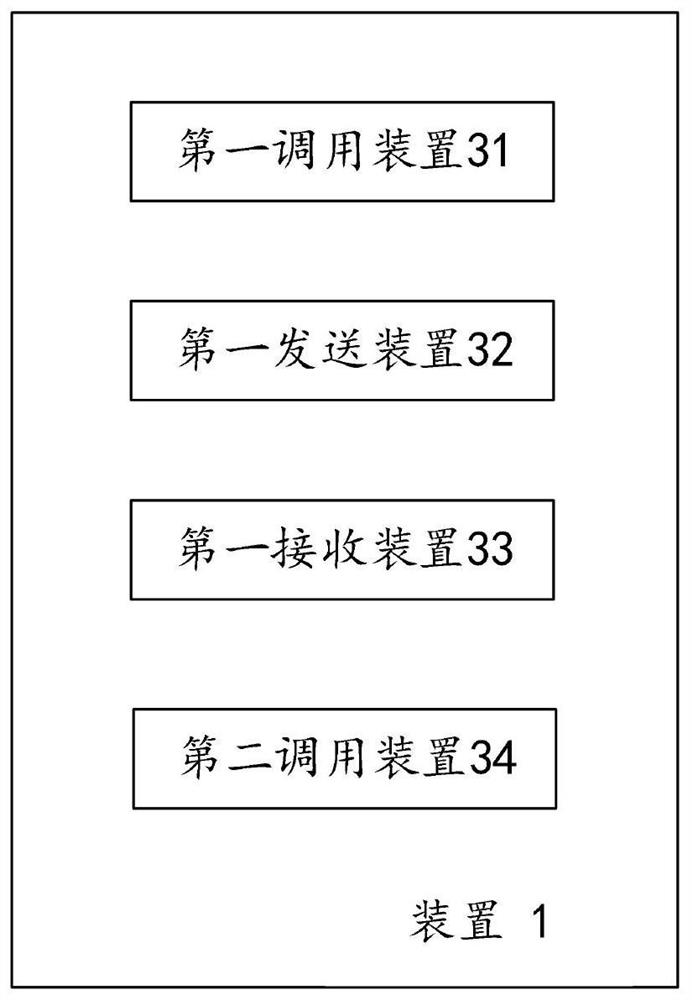
[0037] The application will be described in further detail below in conjunction with the accompanying drawings.
[0038] In a typical configuration of the present application, the terminal, the device serving the network, and the trusted party all include one or more processors (for example, a central processing unit (Central Processing Unit, CPU)), an input / output interface, a network interface and Memory.
[0039] Memory may include non-permanent memory in computer-readable media, random access memory (Random Access Memory, RAM) and / or non-volatile memory, such as read-only memory (Read Only Memory, ROM) or flash memory (Flash Memory). Memory is an example of computer readable media.
[0040] Computer-readable media, including both permanent and non-permanent, removable and non-removable media, can be implemented by any method or technology for storage of information. Information may be computer readable instructions, data structures, modules of a program, or other data. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com