Method for improving SSH protocol security based on SM2 and SM4 cryptographic algorithms
A protocol security and national secret algorithm technology, which is applied in the field of improving SSH protocol security based on SM2 and SM4 national secret algorithms, can solve problems such as unreliable passwords, and achieve good support, good maintainability and high performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021]DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS The following examples are intended to illustrate the invention, but are not intended to limit the scope of the invention.
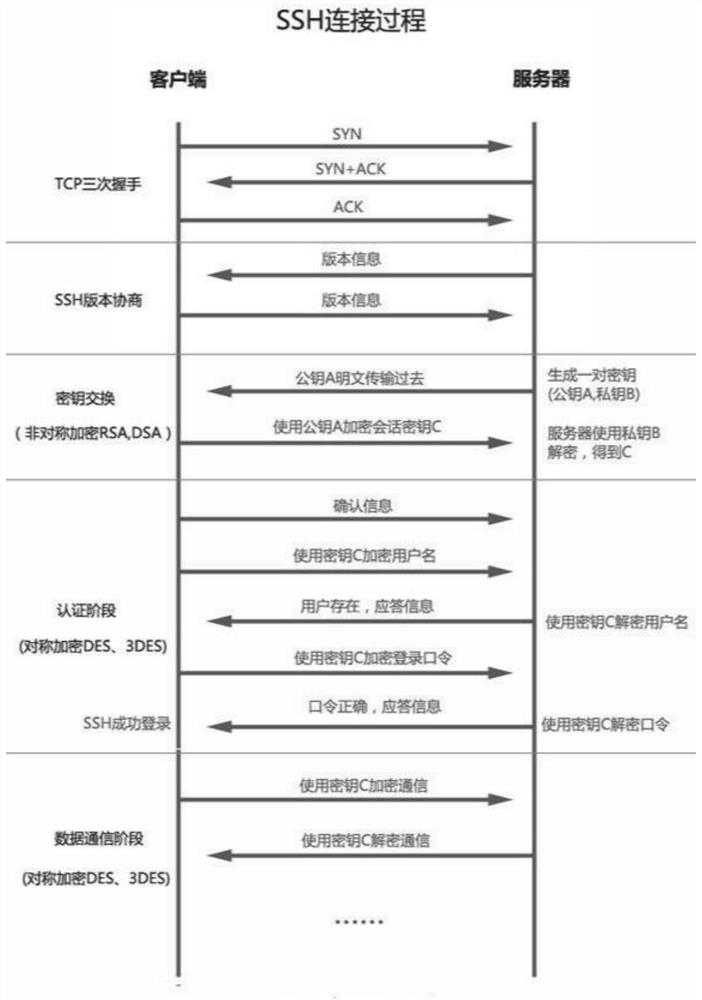
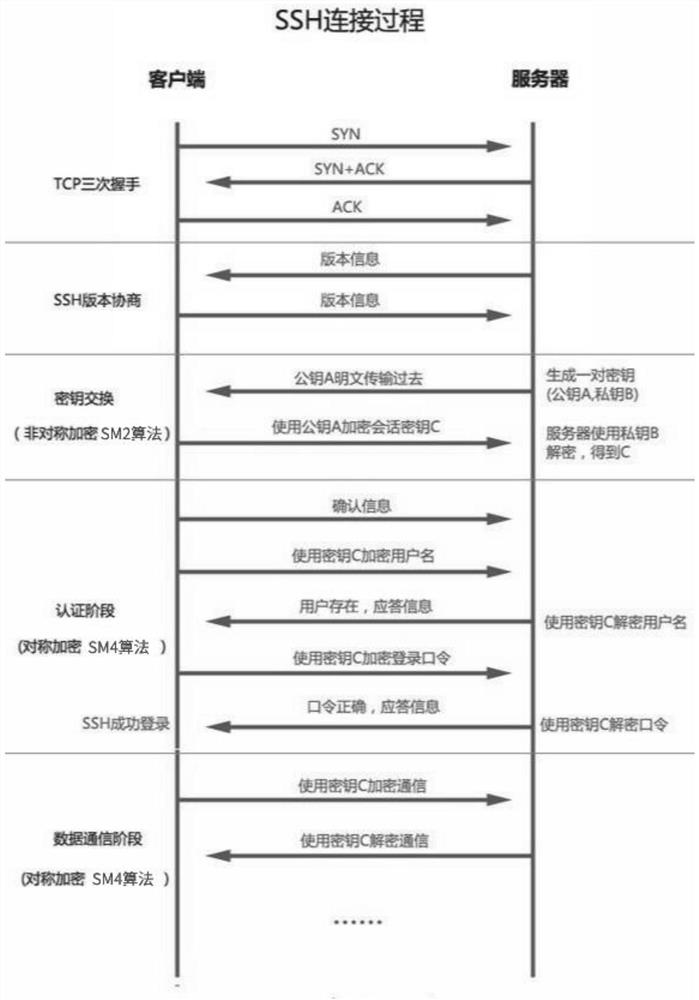
[0022]A method of improving SSH protocol security based on SM2, SM4 national algorithm, including the following steps: replacing the algorithm of key authentication with the SM2 national algorithm during the SSH connection, in the client-server communication phase The symmetric encryption algorithm is replaced with the SM4 national algorithm, and the SSH protocol that supports the National Class Algorithm is implemented.
[0023]A method of improving SSH protocol security based on SM2, SM4 national algorithm, the specific steps are as follows:
[0024]S1, use Golang official code (https: / / github.com / golang / crypto) as a project root directory;
[0025]S2, in the project root directory new folder SM2 and SM4, then copy the contents of the SM2 and SM4 folders in the code base (https: / / github.com / tjfoc / gmsm) to the new f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com