Method for discovering memory destruction vulnerability based on natural language understanding function prototype
A natural language understanding and function technology, applied in the fields of electrical digital data processing, instrumentation, calculation, etc., can solve the problem of false negatives, and achieve the effect of reducing false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
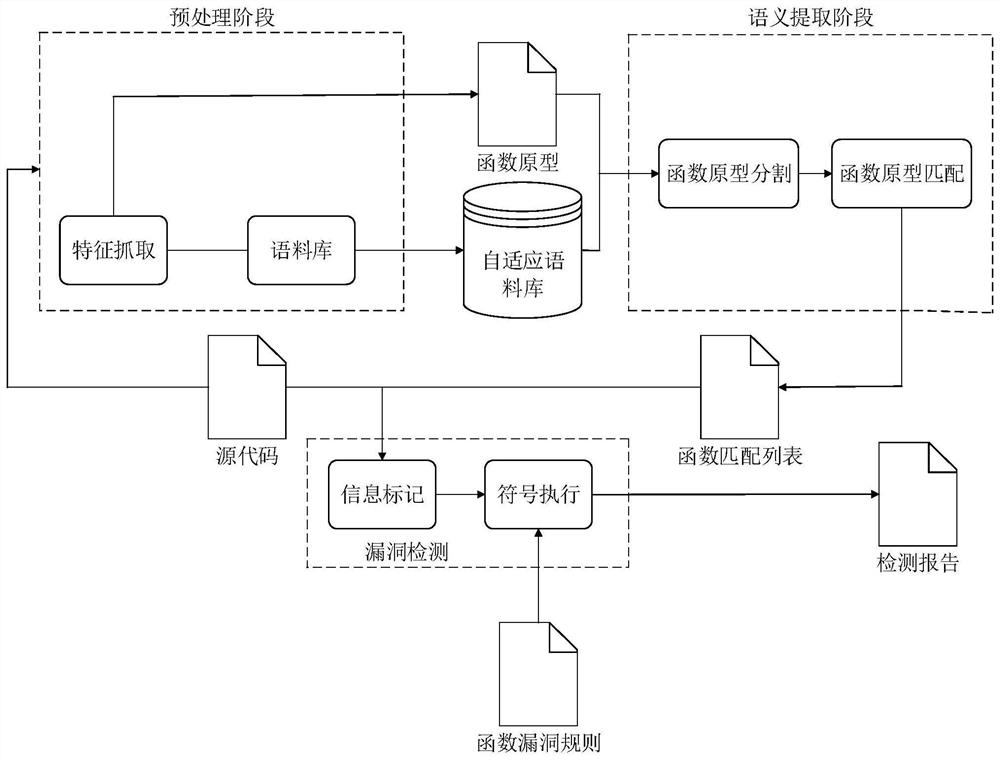
Image
Examples
Embodiment 1
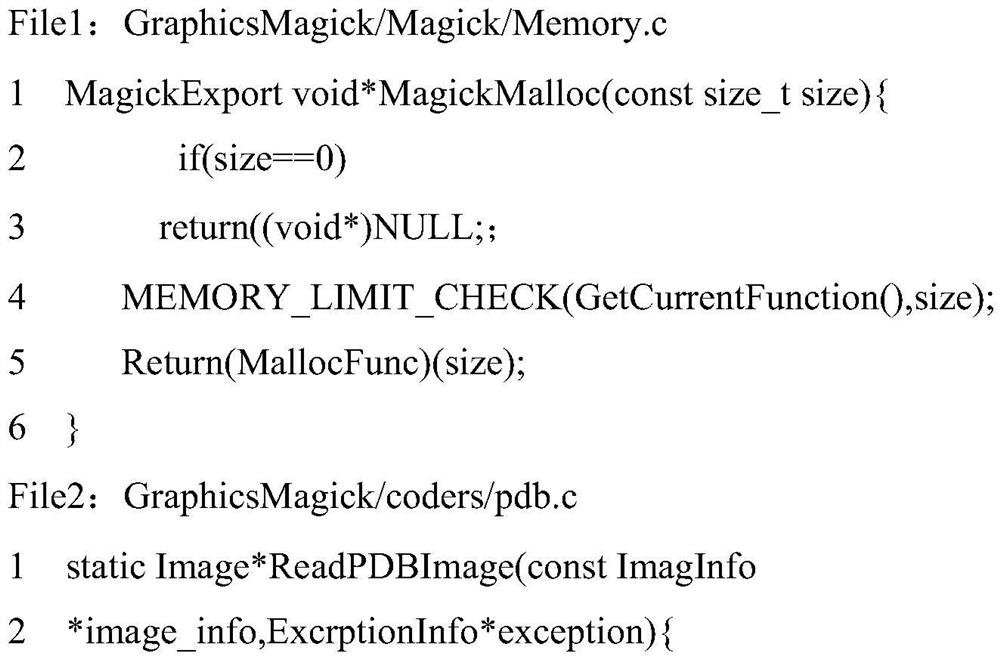
[0029] The source code is an example of a null pointer reference vulnerability in GraphicsMagick's picture management library code, that is, a memory corruption vulnerability. The following is the source code:
[0030]
[0031]
[0032] Among them, MagickAllocateMemory is a function used to allocate dynamic memory in the GraphicsMagick library, and the function prototype of MagickAllocateMemory is defined in File1;
[0033] The memory allocated by MagickAllocateMemory is assigned to the variable comment in the fourth line of File2; if the memory allocation fails, a null pointer is returned; then in the sixth line of File2, when the variable comment is not judged to be a null pointer, it is directly accessed. The memory pointed to by this pointer, resulting in a null pointer dereference vulnerability.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com