Auxiliary server-based secure multi-party computing method, device and system
A technology for secure multi-party computing and auxiliary servers, applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
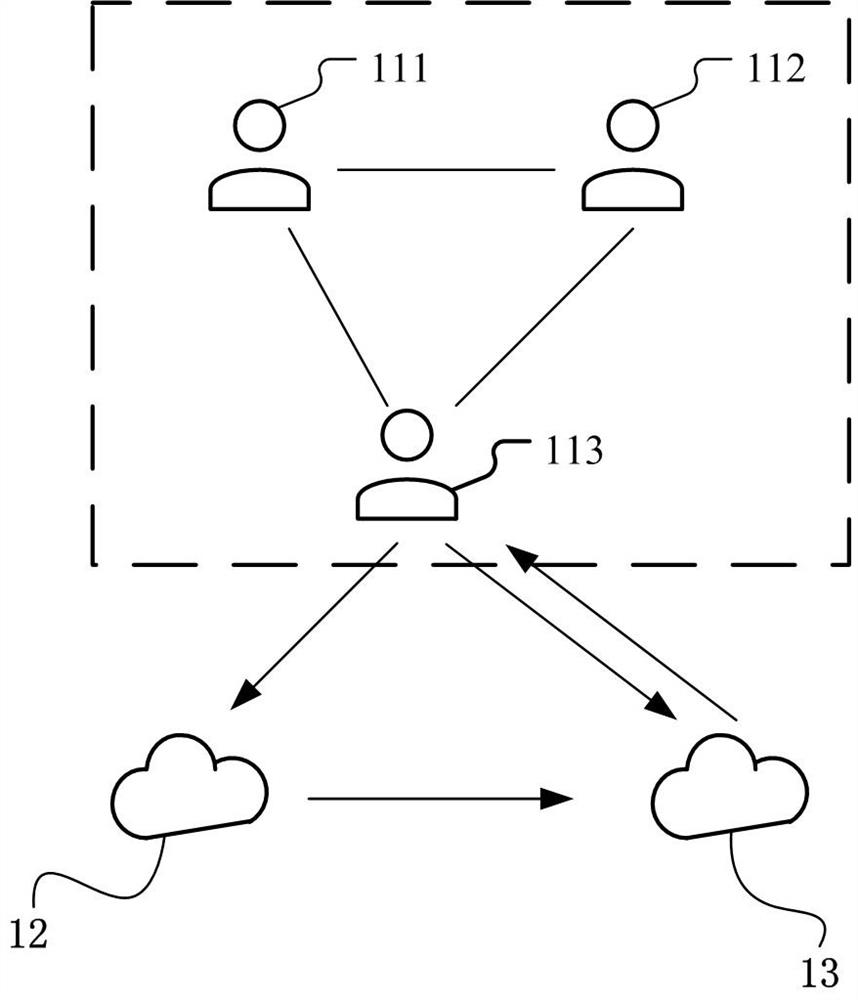
[0058] figure 1 It is a schematic diagram of an implementation scenario of an embodiment disclosed in this specification. This implementation scenario involves secure multi-party computation based on a secondary server. refer to figure 1 , secure multi-party computing involves multiple user nodes including user node 111, user node 112, and user node 113, first server 12, and second server 13. It can be understood that the number of multiple user nodes is not limited to three In the figure, only three user nodes are taken as an example, and the number of multiple user nodes may specifically be four, five, six, etc. The auxiliary server includes a first server 12 and a second server 13 deployed separately.
[0059] Secure multi-party computing is also called multi-party computing (MPC), that is, in the absence of a trusted third party, multiple parties...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap