Three-party authentication and key agreement method, system and computer storage medium supporting data sharing across cloud domains
A data sharing and key negotiation technology, applied in the field of network security, can solve problems such as inefficiency and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] Embodiment 1: In this embodiment, three existing technical solutions are compared with the technical solution of the present invention, and the advantages of the technical solution of the present invention are illustrated by comparing the calculation overhead and communication overhead in the key agreement phase.
[0062] The three prior art solutions are: Patonico et al., Lu et al. and Ma et al.
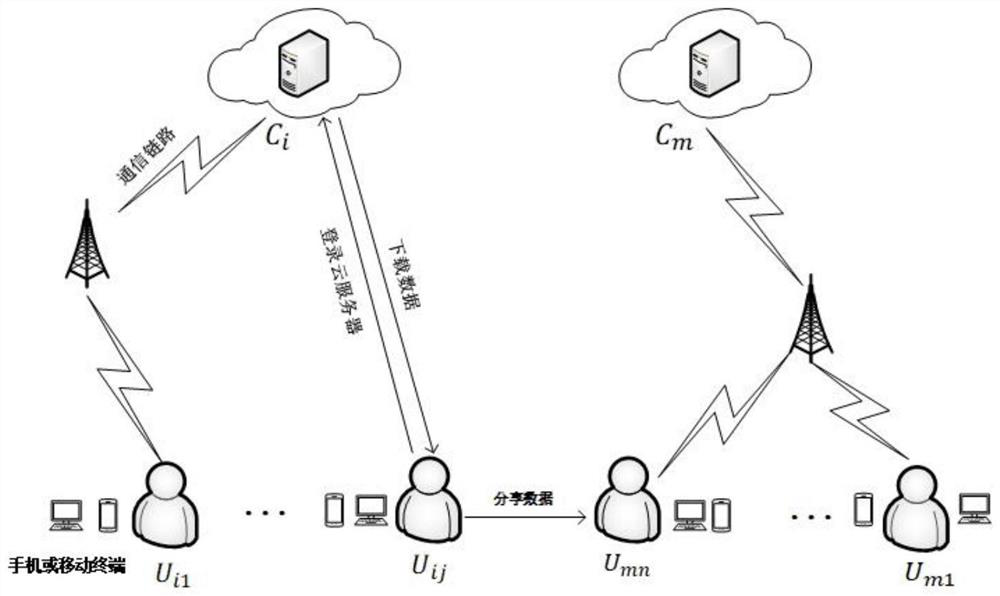
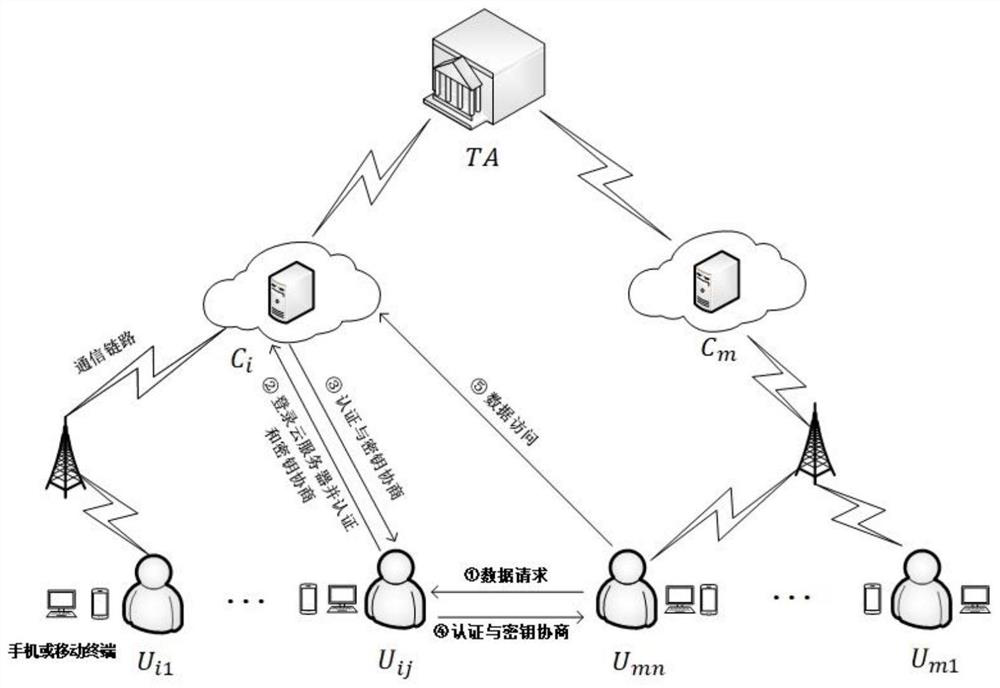
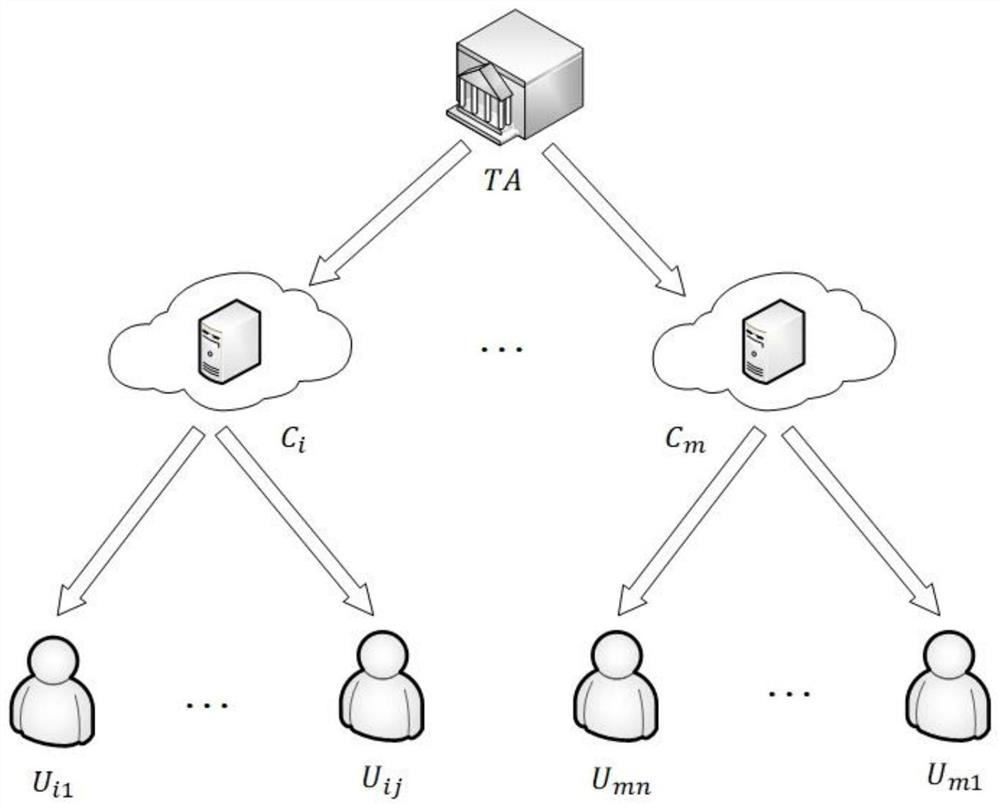
[0063] The node participating in tripartite authentication and key agreement of the present invention is: U ij (users sharing data), C i (store U ij data cloud server) and U mu (Users registered under other cloud service providers).
[0064] The difference between the present invention and the above three prior art solutions lies not only in the different nodes participating in the authentication, but also in the different frameworks. The present invention refers to the service scope of each cloud service provider to its own users as a cloud domain. The sharer user acts a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com