Identity recognition method, device and equipment based on keystroke characteristics of mobile equipment and medium
A mobile device and identity recognition technology, applied in the field of identity recognition, can solve the problems of decreased accuracy and inability to perfectly match the keystroke characteristics of mobile users, and achieve the effects of improving accuracy, reducing the amount of input data, and easy expansion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] This embodiment provides an identification method based on keystroke features of a mobile device, including:
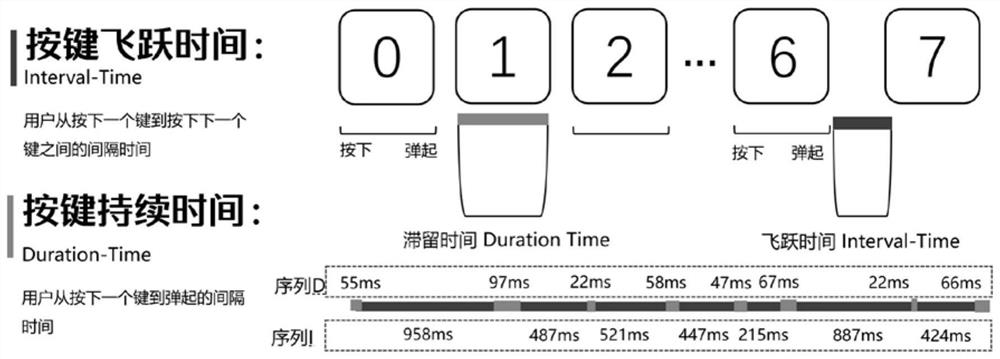
[0062] Step 1. For the user whose identity is to be identified, extract the keystroke features from the keystroke process of the user logging in to the mobile device: the leap time series, the residence time series and the contact coordinate sequence, and calculate the relationship between each keystroke feature and the keystroke during registration. Variance, Euler distance and Pearson correlation coefficient between key features to obtain the following 9 characteristic parameters of user login: leap time series variance, leap time series Euler distance, leap time series Pearson correlation coefficient, stay time series variance , Euler distance of residence time series, Pearson correlation coefficient of residence time series, variance of contact coordinate sequence, Euler distance of contact coordinate sequence and Pearson correlation coefficient of contact c...
Embodiment 2
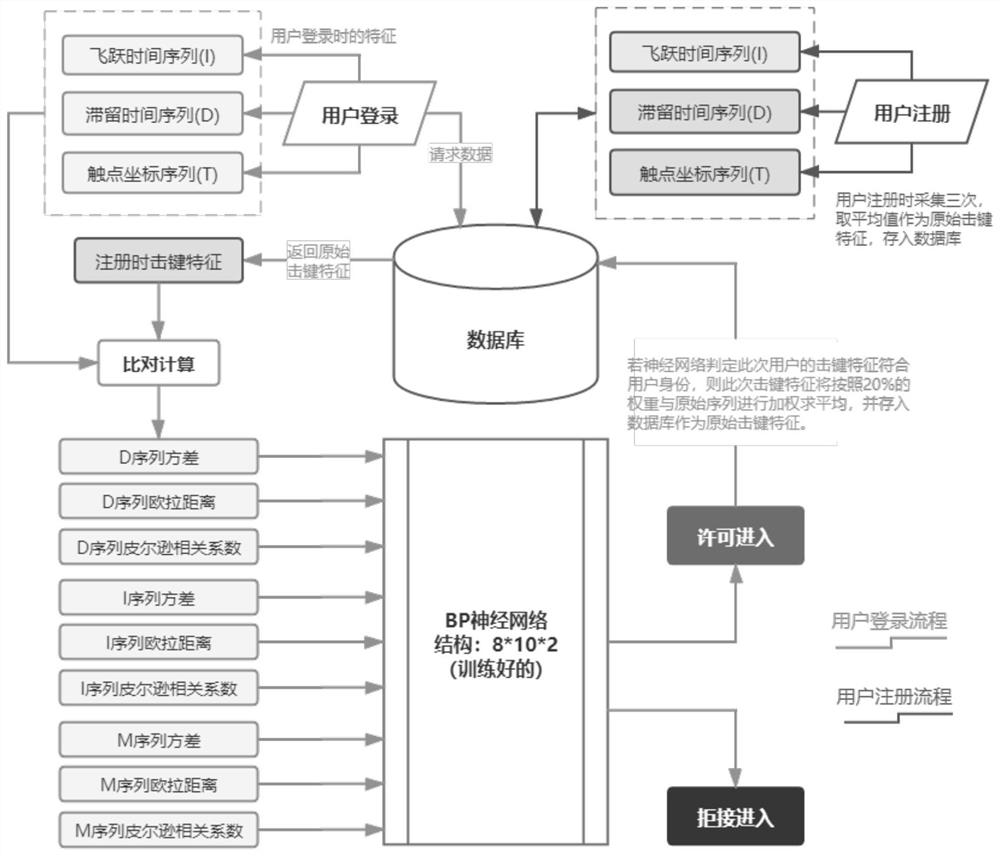
[0120] This embodiment provides an identification device based on keystroke features of mobile equipment, such as image 3 As shown, it includes: a keystroke feature collection module, a comparison module, an identity recognition model, a database module and a feature update module; where:
[0121] The keystroke feature collection module is used for: extracting keystroke features from the keystroke process of logging in the mobile device for the user whose identity is to be identified: leap time sequence, residence time sequence and contact coordinate sequence;
[0122] The comparison module is used to: calculate the variance, Euler distance and Pearson correlation coefficient between each keystroke feature and the keystroke feature at the time of registration, and obtain the following 9 feature parameters of user login: leap time series variance, leap Time Series Euler Distance, Leap Time Series Pearson Correlation Coefficient, Stay Time Series Variance, Stay Time Series Eule...
Embodiment 3
[0127] Embodiment 3 provides an electronic device, including a memory and a processor, and a computer program is stored in the memory. It is characterized in that, when the computer program is executed by the processor, the processor implements the embodiment 1. the method described.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com