A UAV-assisted terminal access authentication method, system, device and application
An authentication method and terminal access technology, applied in the field of communication network security, can solve problems such as attacks, affecting the execution of protocols, and threats to the security of entities to be authenticated, and achieve the effects of avoiding leakage and preventing computational overhead and communication overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
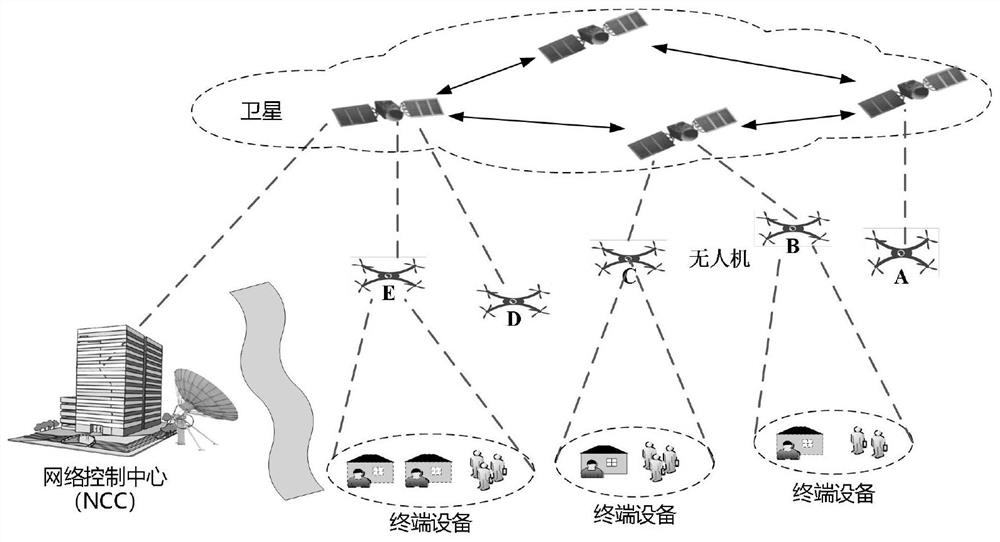
[0109] Aiming at the problems existing in the prior art, the present invention provides a method and application for terminal access authentication assisted by a drone in a space-ground integrated information network.
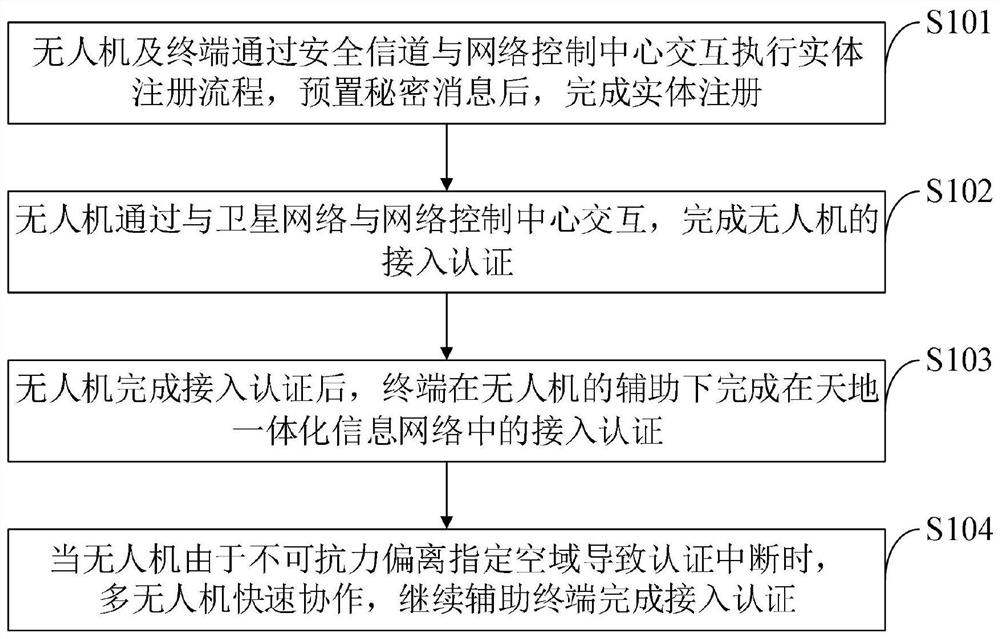
[0110] The present invention is achieved in this way, a terminal access authentication method assisted by a drone in a space-ground integrated information network, the terminal access authentication method assisted by a drone in a space-ground integrated information network includes the following steps:
[0111] In the first step, after adding a hardware-based physical unclonable function (PUF) to the memory of the UAV, terminal, and network control center, the UAV and terminal interact with the network control center through a secure channel to complete the registration;
[0112] In the second step, after both the drone and the terminal are registered, the drone performs access authentication;
[0113] In the third step, after the UAV access authentication is ...
Embodiment 2
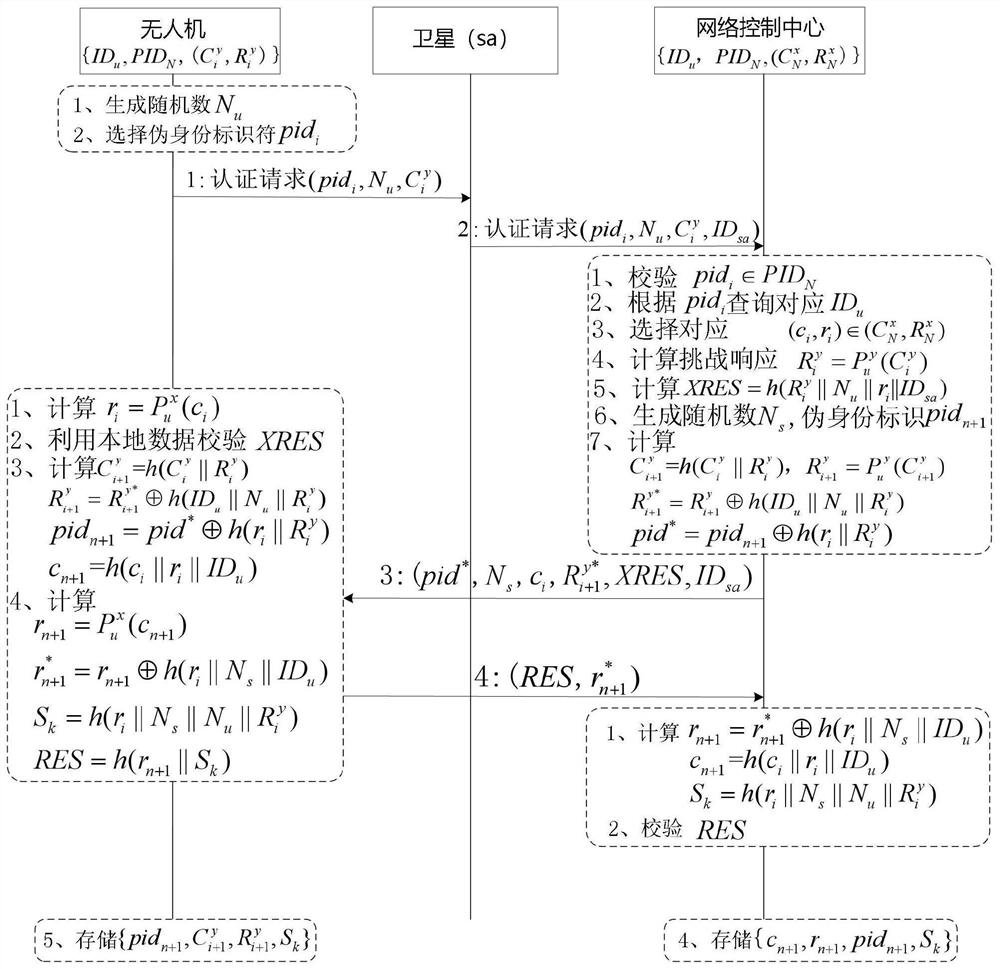
[0168] Aiming at the problems existing in the prior art, the present invention provides a UAV-assisted terminal access authentication method and application suitable for space-ground integrated information network. The present invention will be described in detail below with reference to the accompanying drawings. Previously, a supplementary explanation was made for the Physically Unclonable Function (PUF):
[0169] PUF is a physical stimulus-response function, whose input is called stimulus, which can be identified by x∈X, and the response corresponding to each stimulus can be represented by y∈Y. Usually a stimulus and its corresponding response are called a stimulus-response pair (Challenge Response pair, CRP), which can be represented by CRP(x,y). The following formula is used to describe the relationship of a physical unclonable function response to a specific stimulus: PUF:X→Y:PUF(x)=y. When queried with incentive x, the PUF produces a response It depends on x and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com