Computer security protection system based on big data
A computer security and protection system technology, applied in the field of information security, can solve the problems of reduced free space and reduced user experience, and achieve the effect of reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] A specific embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings, but it should be understood that the protection scope of the present invention is not limited by the specific embodiment.
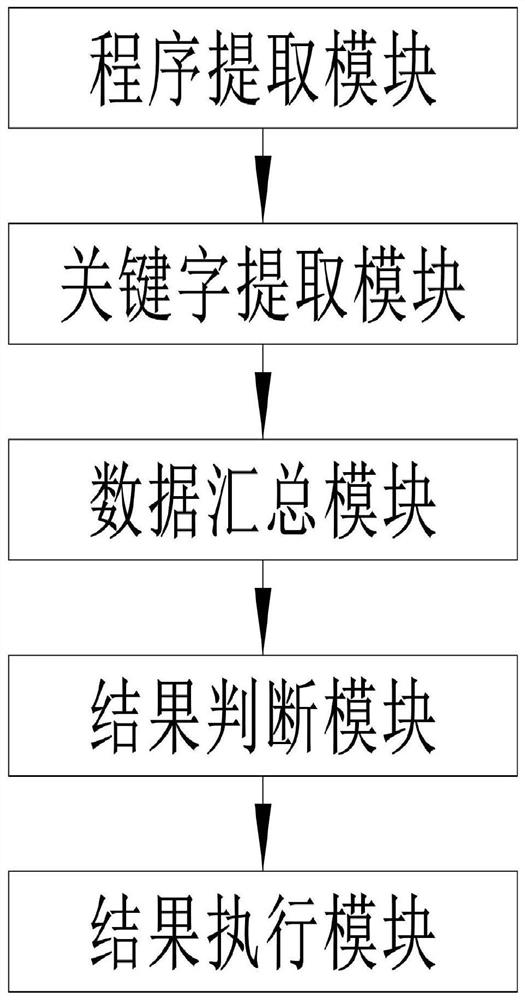
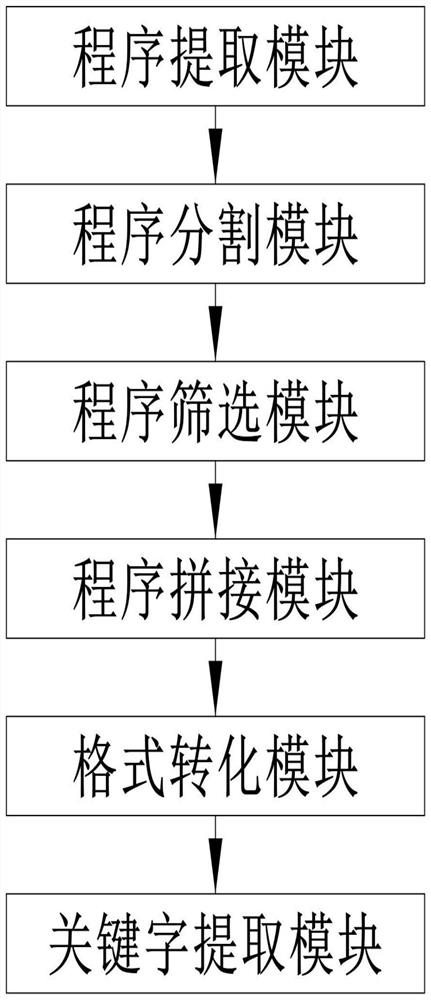
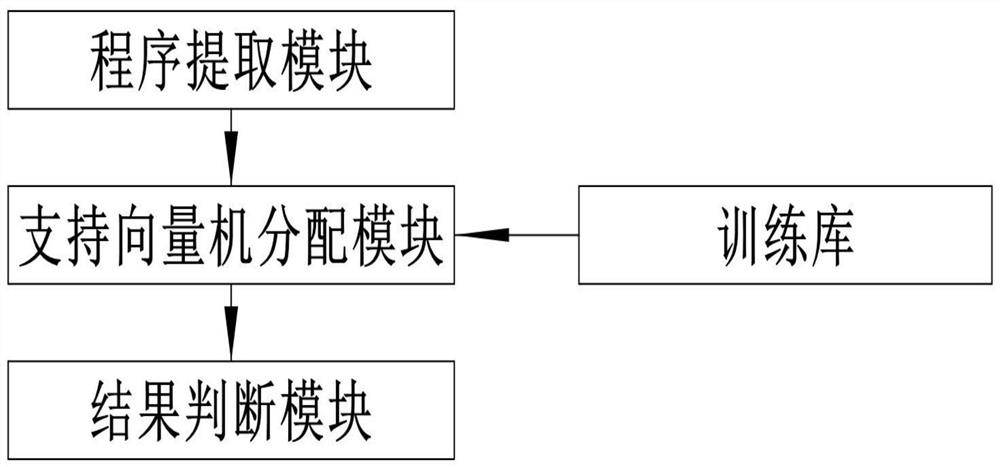
[0035] Specifically, such as Figure 1-4 As shown, the embodiment of the present invention provides a computer security protection system based on big data, including: a program extraction module, a keyword extraction module, a data summary module, a result judgment module and a result execution module. The following is an introduction to the functions of each module.
[0036] The program extraction module is used for intercepting the program to pass through the firewall, and converting the program into a text format to obtain the original program text. In this module, the program that needs to pass through the firewall is the program that is currently accessing the computer, and it is also the program that is blocked by ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com