Information security capability evaluation system and method based on mobile terminal behaviors
A mobile terminal and information security technology, applied in the field of information security, can solve problems such as low efficiency and incapable terminal evaluation, and achieve the effects of fast processing, accurate processing, and accurate collection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
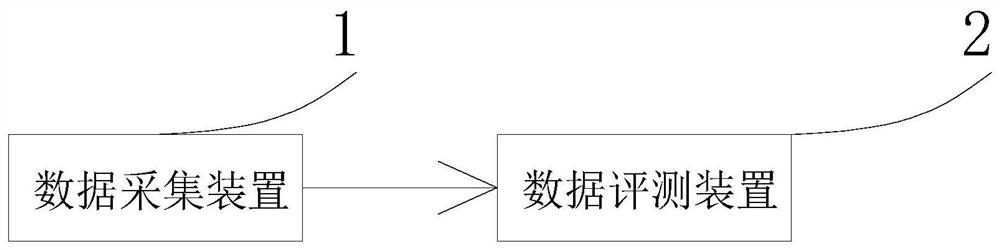
[0049] see figure 1 , in Embodiment 1 of the present invention, a structural diagram of an information security capability evaluation system based on mobile terminal behavior provided by the embodiment of the present invention, including: a data collection device 1 and a data evaluation device 2 connected to the data collection device 1 in communication ; Specifically, the data acquisition device 1 and the data evaluation device 2 can be connected through a wired connection or a wireless connection, which uses an existing communication protocol for connection.
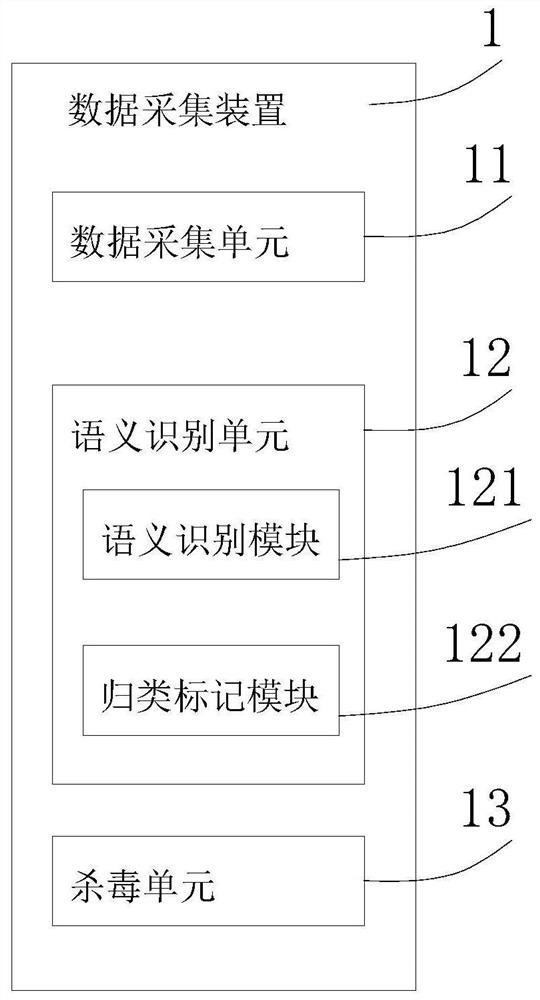
[0050] The data collection device 1 is used to collect behavior data of the mobile terminal, perform semantic recognition on the acquired behavior data, classify and mark the behavior data according to the semantic recognition result, and send the classified and marked behavior data to the data evaluation device 2;
[0051] The data evaluation device 2 is used to evaluate the classified and marked behavior data through...
Embodiment 2
[0074] see Figure 4 The embodiment of the present invention also provides a method for evaluating information security capabilities based on mobile terminal behavior, including the following steps:
[0075] S101: collecting behavior data of the mobile terminal;
[0076] S102: Perform semantic recognition on the acquired behavior data;
[0077] S103: Classify and mark the behavior data according to the semantic recognition result;
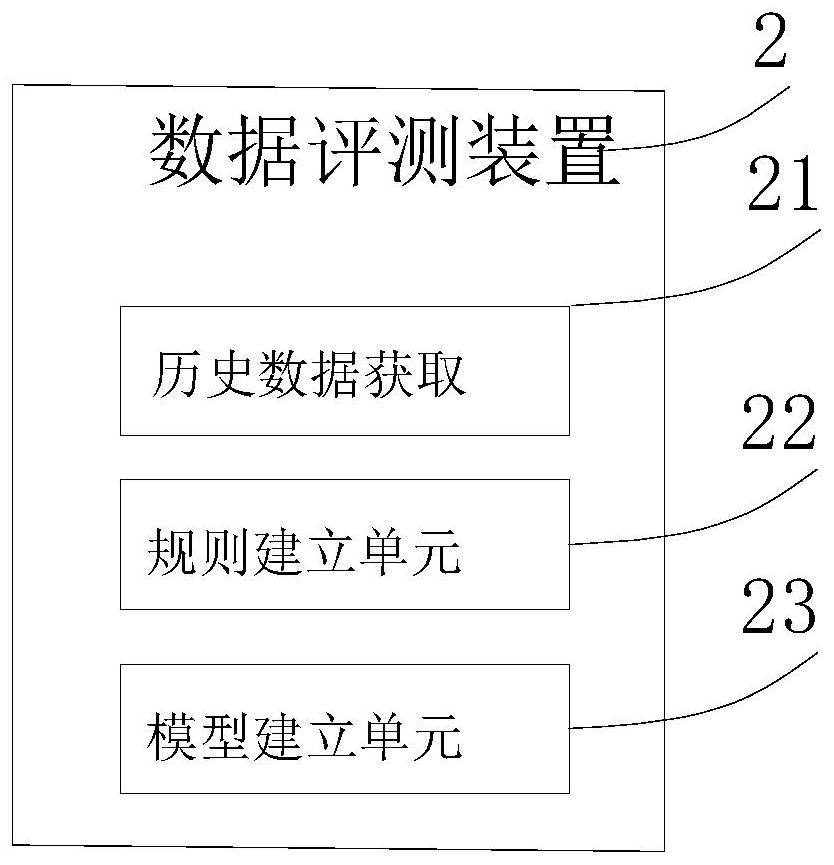
[0078] S104: Evaluate the classified and marked behavior data through a preset evaluation model to obtain safety level data.
[0079] see Figure 5 , the S104 step, also includes the following steps:
[0080] S1041, acquiring a set of historical behavior data samples of the mobile terminal;
[0081] S1042. Determine the weight of the historical behavior data sample, and establish an unsafe behavior evaluation rule for evaluating the safety of the behavior data according to the weight of the historical behavior data sample;
[0082] S1043. Con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com