Method and system for preventing back end from tampering uplink data and blockchain network
A block chain and anti-tampering technology, which is applied in digital transmission system, transmission system, user identity/authority verification, etc., can solve the problems of unguaranteed stability and large transformation of the original structure, so as to achieve low transformation cost and prevent tampering effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Embodiments of the present invention are described below with reference to the accompanying drawings, so that those skilled in the art can better understand the present invention and implement it, but the enumerated embodiments are not used as a limitation of the present invention. In the case of no conflict, The following embodiments and the technical features in the embodiments can be combined with each other, wherein the same components are denoted by the same reference numerals.
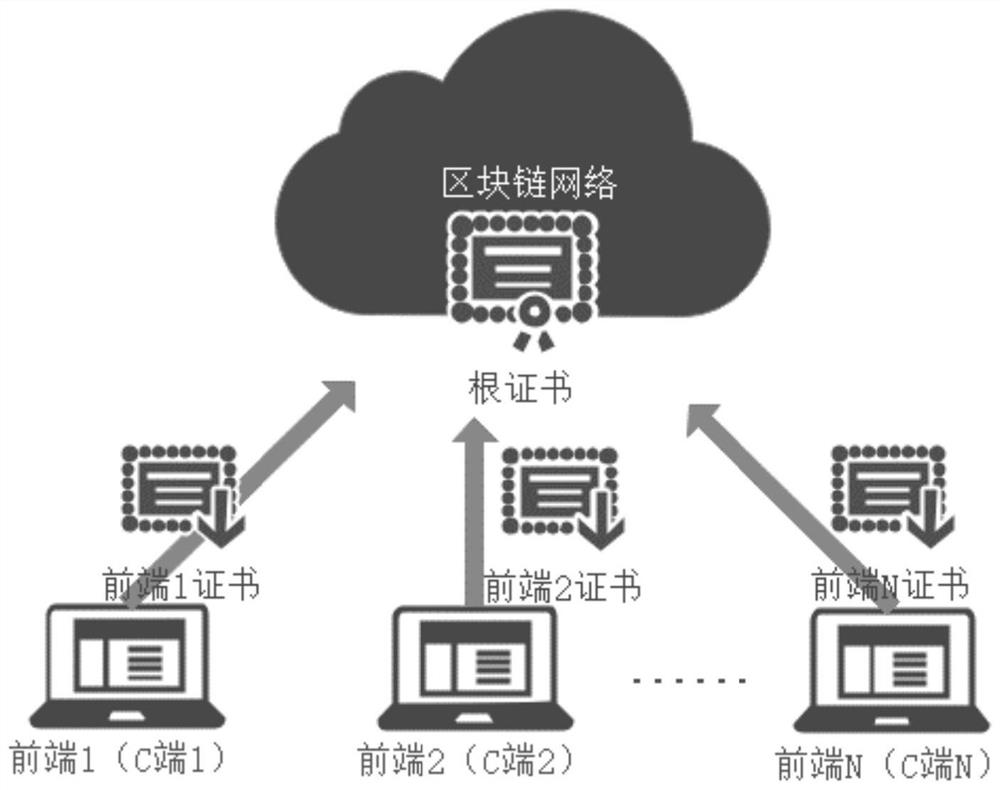
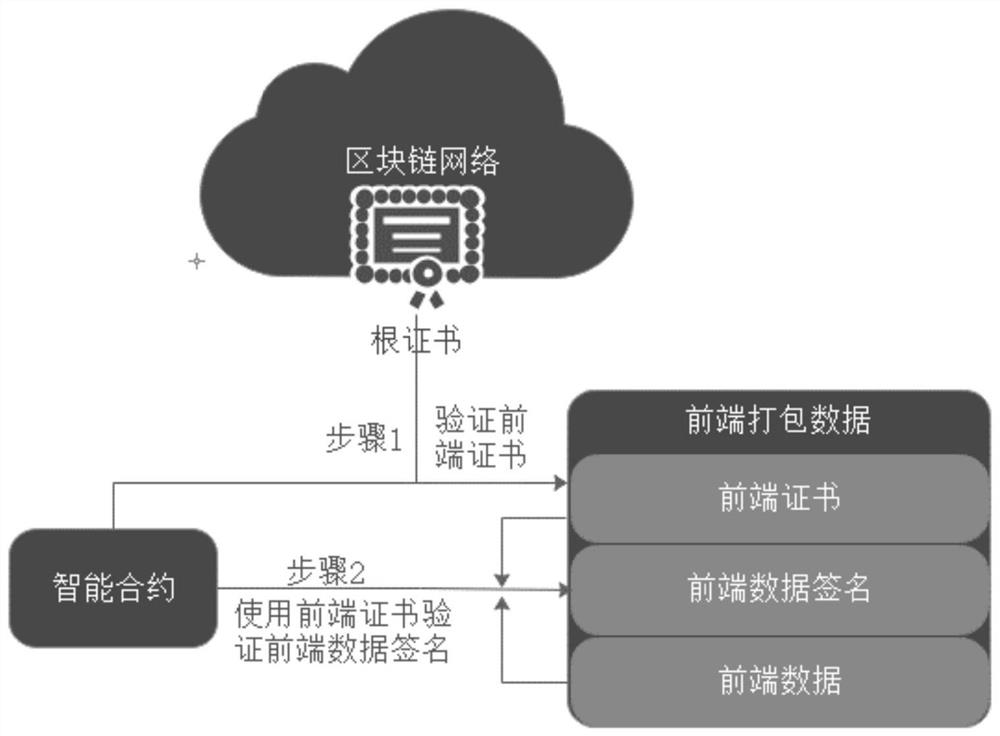
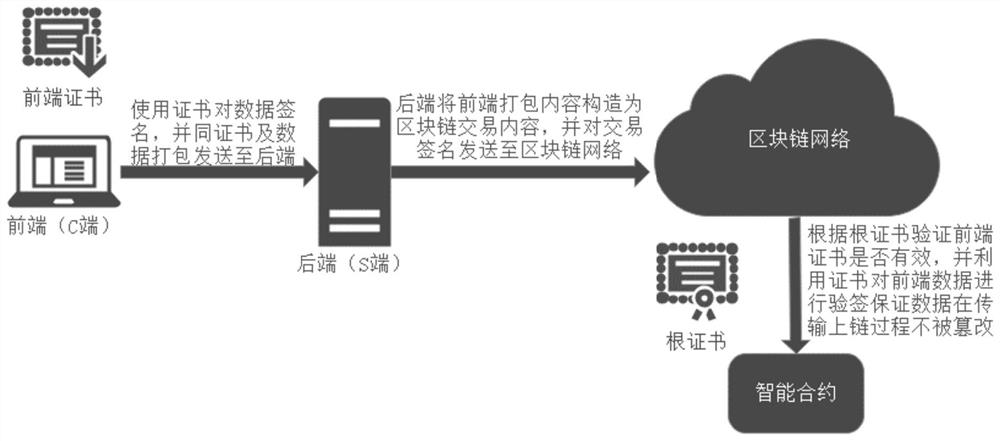
[0016] The method of the present invention mainly solves the problem that the uplink data is tampered with in the transformation of the traditional C / S architecture block chain, that is, after the back end (S end) receives the data D of the front end (C end), it uploads it to Before the blockchain, the data D may be tampered with, and after being on the chain, the blockchain cannot verify whether the data D has been tampered with. The present invention uses a certificate system to protect ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com