Method for non-standardized dialing service monitoring between networks
A business and standardized technology, applied in the direction of automatic exchange, telephone communication, electrical components, etc., can solve the problems of inability to identify malicious calls, adverse maintenance, normal business impact, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] To monitor the callback card business, the specific steps are as follows:
[0046] Step 1, the user initiates an inter-network call request;
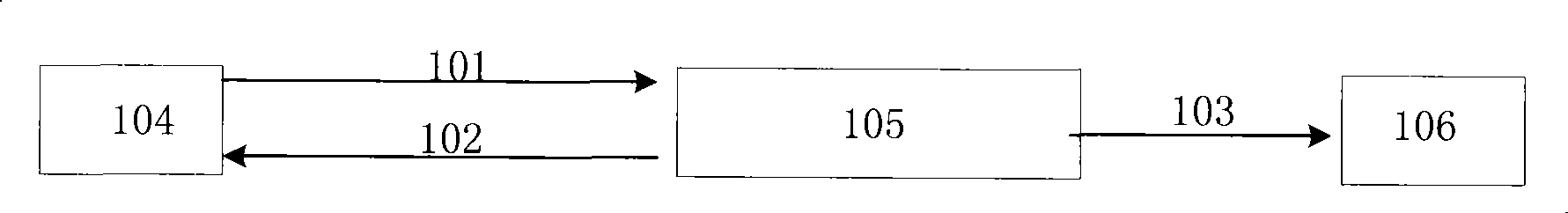
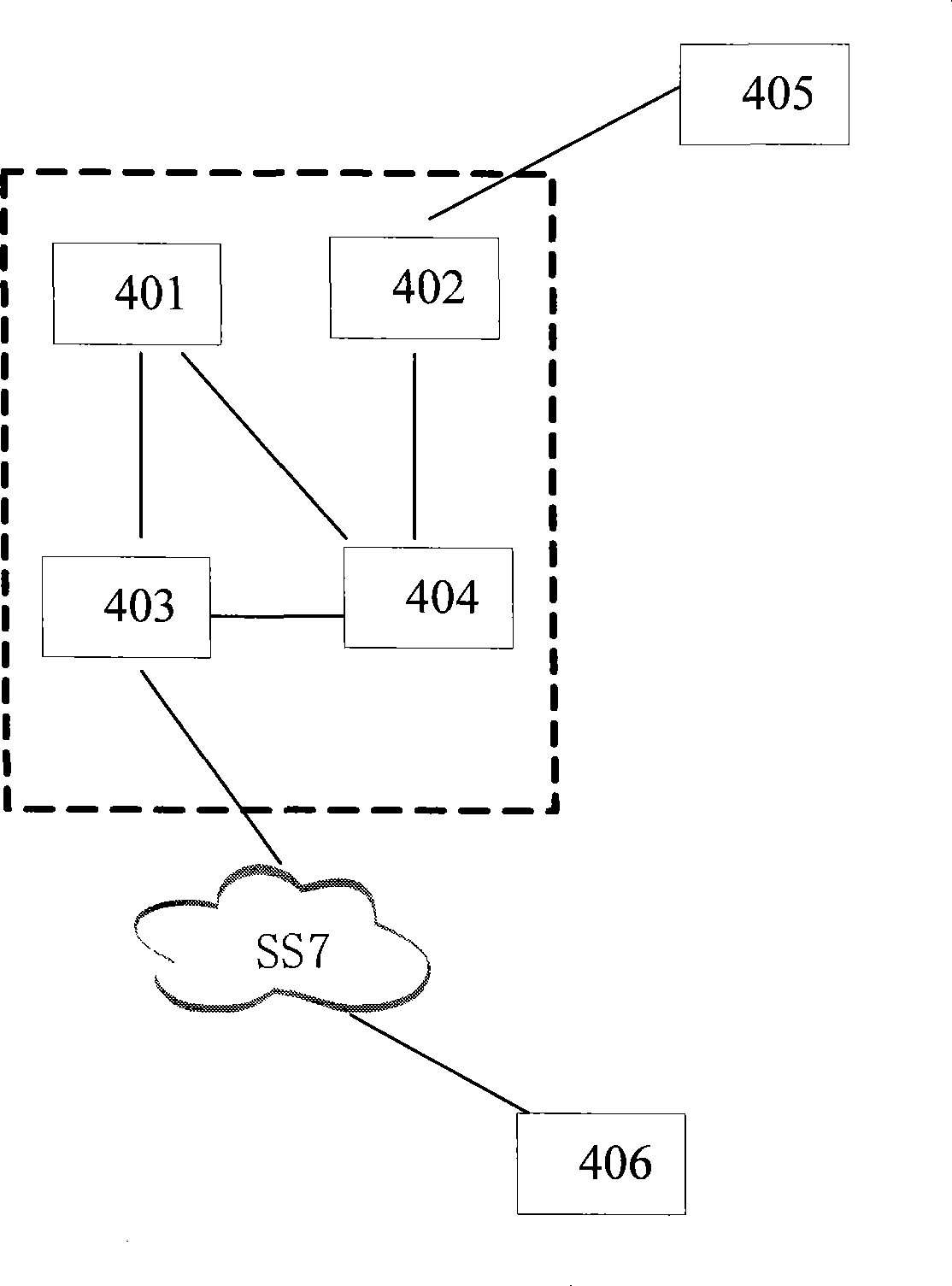
[0047] Step 2, MSC (Mobile Switching Center, Mobile Switching Center) triggers a call to intercept monitoring node according to user subscription information;
[0048] Step 3. Call back the card platform to call back the user;
[0049] Step 4, the GMSC of the gateway office triggers the inter-network incoming calls to the interception monitoring node;
[0050] Step 5. Intercept the monitoring node to collect the user's inter-network call records (including calling number, called number, call time, roaming location, ringing duration, call duration, etc.), and transfer the call records to the analysis via FTP node;
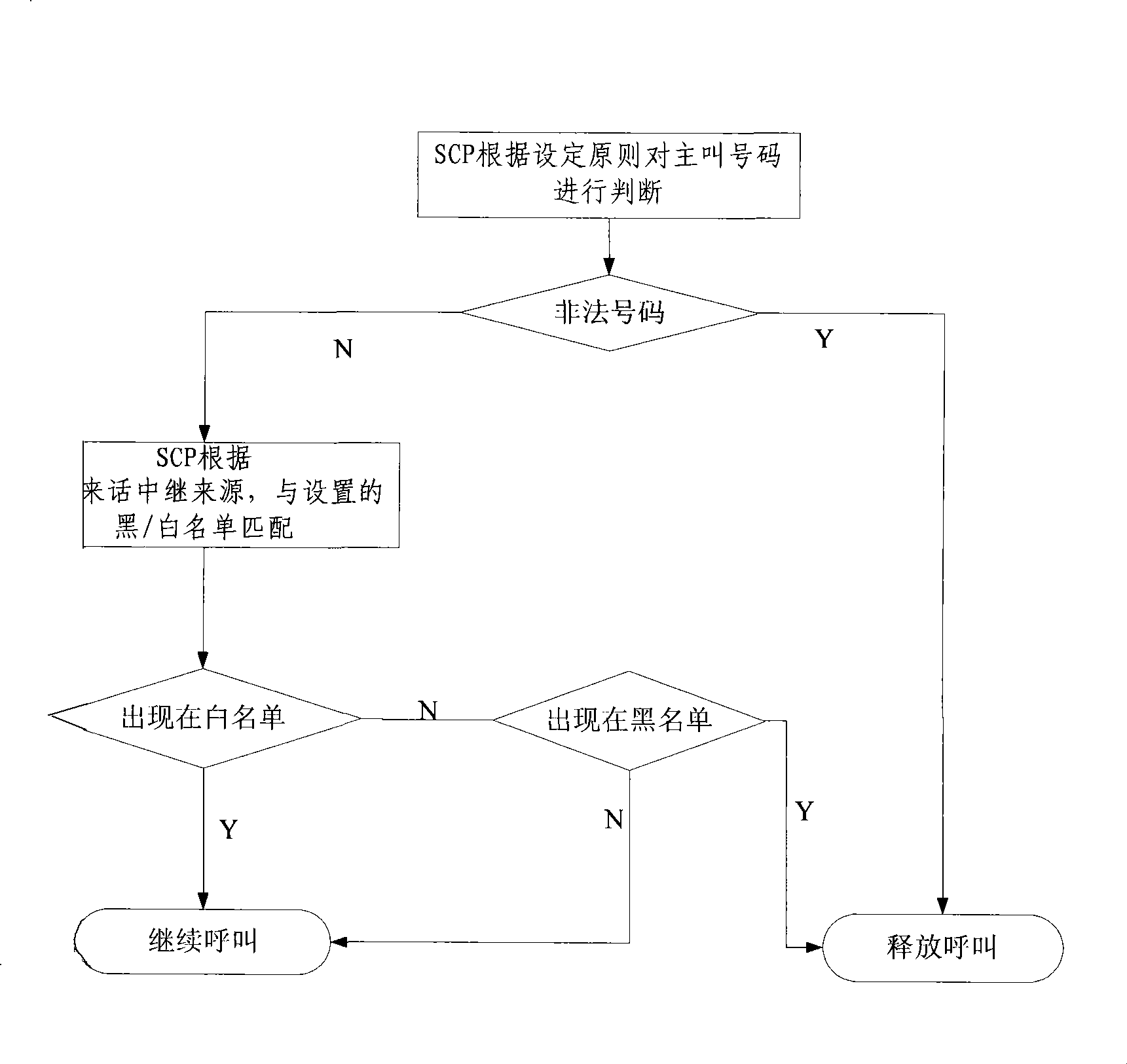
[0051] Step 6, the analysis node loads the call record provided by the interception monitoring node into the database for data analysis, setting the time threshold t and the quantity threshold n, as there is once A-...
Embodiment 2
[0057] The specific steps for the monitoring of harassing calls on the Internet are as follows:
[0058] Step 1, the user initiates an inter-network call request;
[0059] Step 2, the gateway office GMSC / tandem office TMSC receives the request, and triggers the call to the intercepting monitoring node;
[0060] Step 3, intercepting the call record (comprising information such as calling number, called number, calling time, ringing duration, call duration) of monitoring node collection user;
[0061] And transfer the call record to the analysis node through FTP;
[0062] Step 4, the analysis node loads the call record provided by the interception monitoring node into the database, first screens out the ultra-short ringing bill, and then according to the set parameter combination (such as call frequency, ringing duration, call time period, call range , Calling / Called Number Dispersion, Reply Connect Rate, etc., can use data mining software for logistic regression analysis to o...
Embodiment 3
[0068] The ANN call monitoring method is not standardized in the network, and the specific steps are as follows:
[0069] Step 1: The user initiates an inter-network call request;
[0070] Step 2: MSC receives the request, and triggers the call to the intercepting monitoring node according to the user's subscription information;
[0071] Step 3: Intercepting the monitoring node to collect the user's call record (including calling number, called number, calling time, roaming place and other information);
[0072] And transfer the call record to the analysis node through FTP;
[0073] Step 4: the analysis node loads the call records provided by the interception monitoring node into the database for data analysis, and adds the called numbers (such as high calling frequency and wide range of calling users) that meet certain statistical characteristics into the outgoing call answering monitoring list; The intercept monitoring node conducts response monitoring and real-time analys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com