An enterprise legal person identity authentication management method and system based on enterprise chain code
A technology of identity authentication and management methods, applied in user identity/authority verification, transmission systems, digital transmission systems, etc., can solve problems such as easy forgery, low credibility, and fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
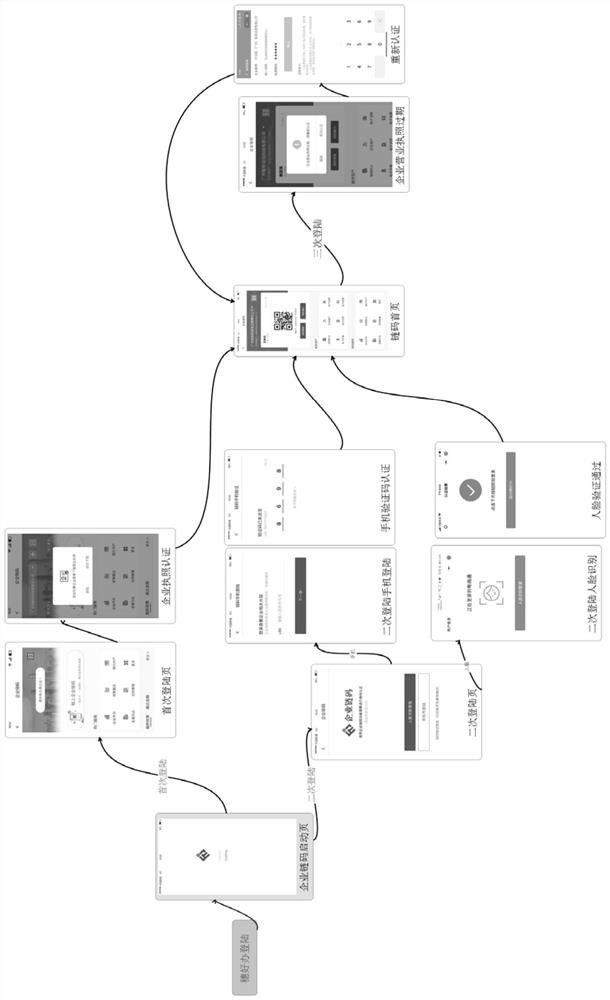
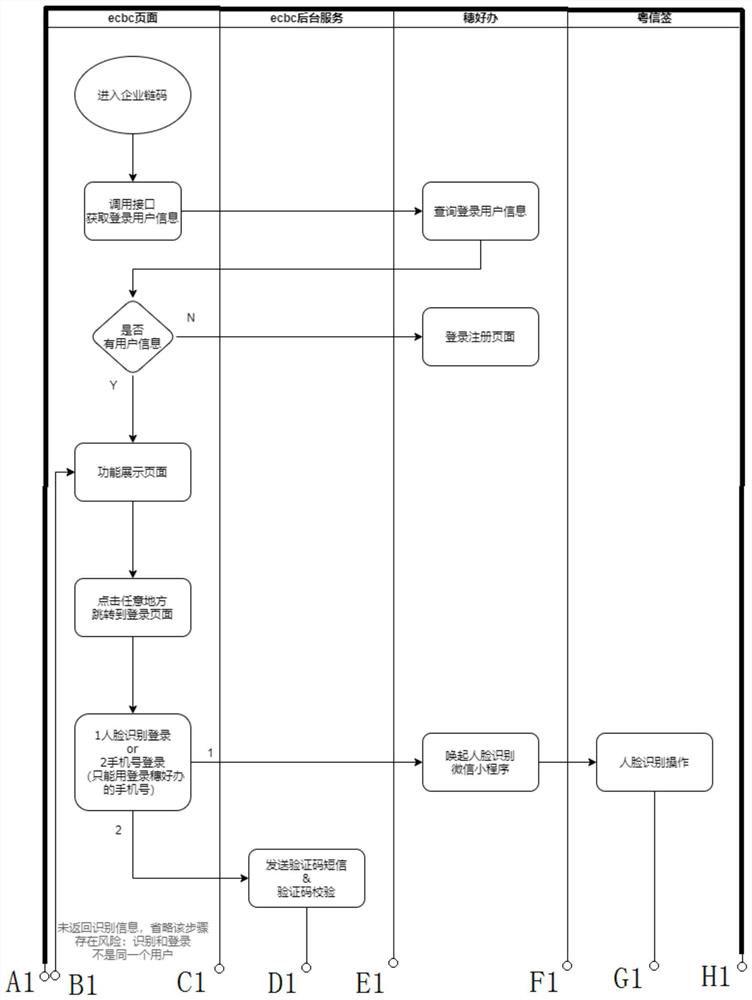
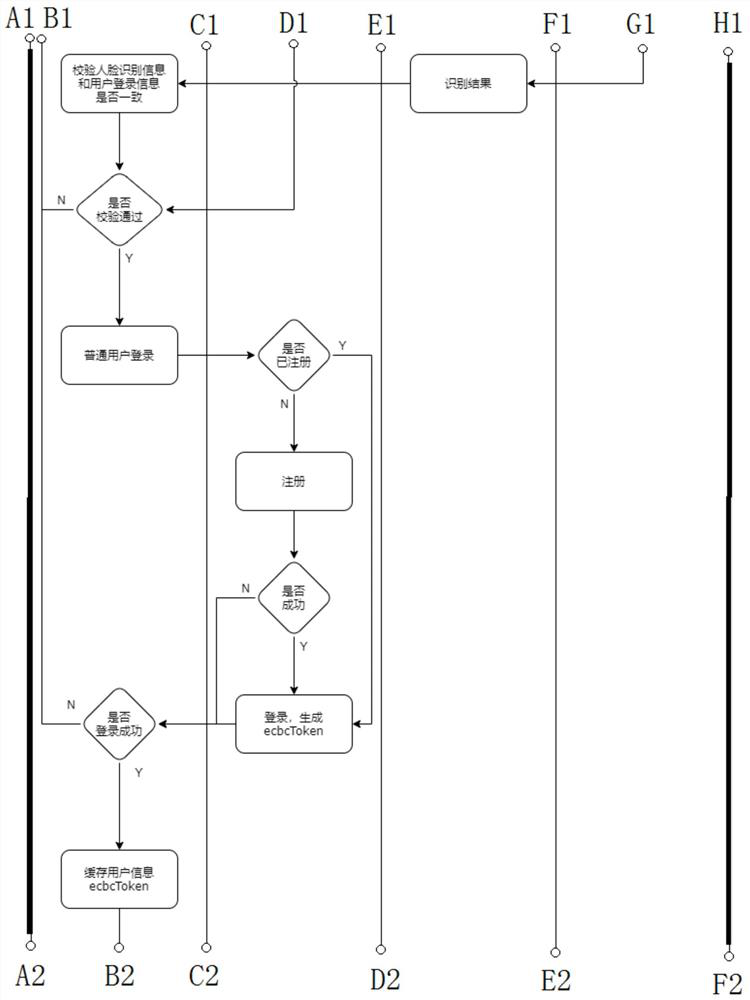
[0063] Enterprise chain code account: There are three major elements: private key, public key, and address. The way they are generated in general,
[0064] Address: The address is generated by the public key and is also the identification of the system interacting. On the one hand, because the public key is too long, in
[0066] Face recognition is a kind of biometric identification technology based on human facial feature information for identification. with camera
[0076] Dimensionality reduction is an important step in face recognition. Different feature expression methods and dimension sizes will directly affect the face
[0079] The feature of face recognition is a multi-light source face recognition technology based on active near-infrared images. it can overcome light
[0080] The human face is innate like other biological features of the human body (fingerprints, iris, etc.), and its uniqueness and
[0081] Non-mandatory: the user does not need to cooperate with the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com