Method and system for generating smart contract with vulnerabilities based on TreeGAN
A smart contract and vulnerability technology, applied in the field of blockchain technology and deep learning, can solve problems such as unnaturalness, lack of training data, and extensiveness, and achieve the effect of accelerating model convergence and flexible selection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific embodiments.
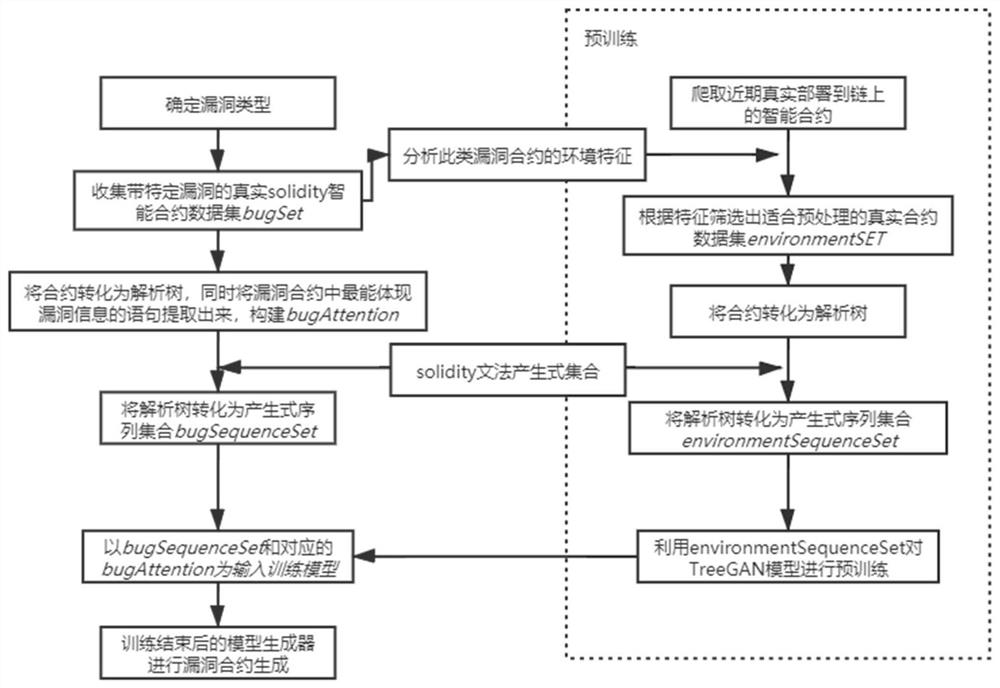
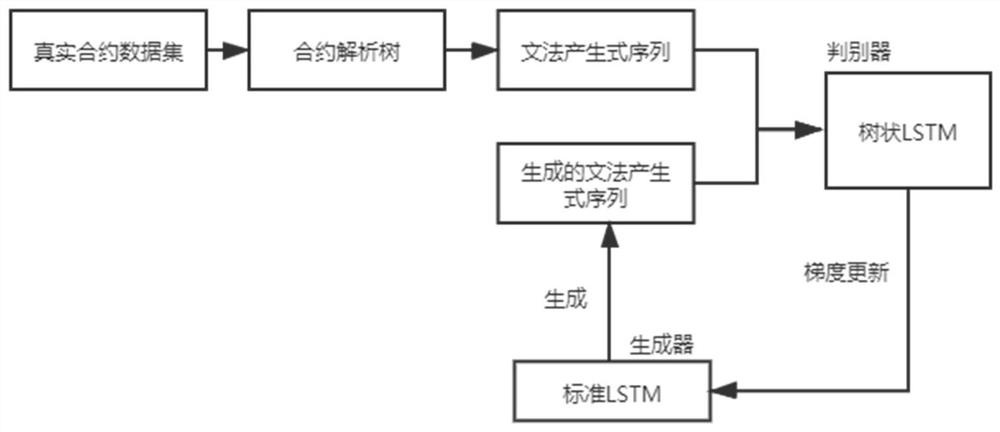
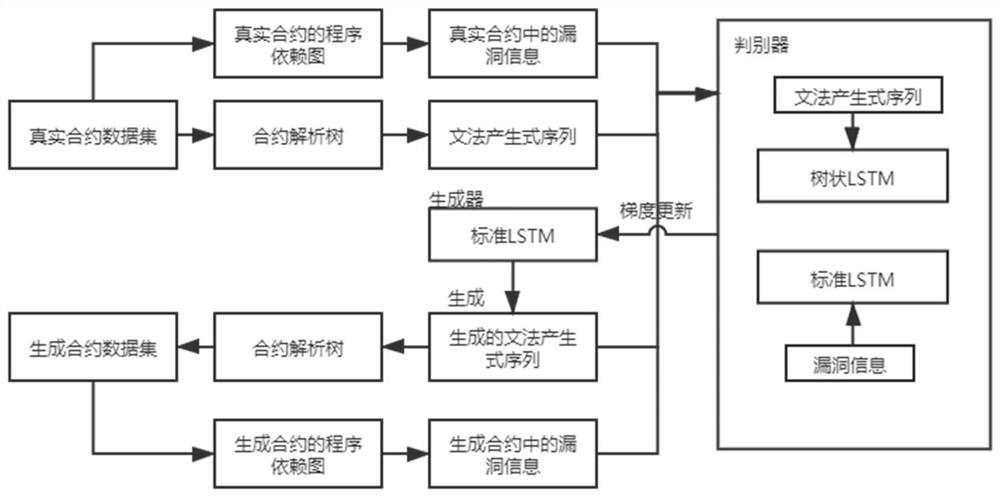
[0040] In order to ensure that the generated vulnerability smart contract can pass through the compiler without grammatical errors, the present invention selects TreeGAN as the framework. After determining the type of vulnerability in the generated contract, collect the real vulnerability smart contract data set bugSet on the public platform.
[0041] In order to speed up the convergence, the model needs to be pre-trained first. Considering that most vulnerable contracts only need to modify the characters or positions of one or a few statements, it can be concluded that the environmental information of the vulnerable contract and some real contracts should be similar. Therefore, the pre-training strategy of the present invention is: analyze the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com