Computer network information safety control device
A computer network and information security technology, applied in the field of computer network information security control devices, can solve the problems of easy cracking of passwords, unsatisfactory computer information anti-theft methods, and inability to effectively prevent computer information from being stolen, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in further detail below in conjunction with the accompanying drawings.
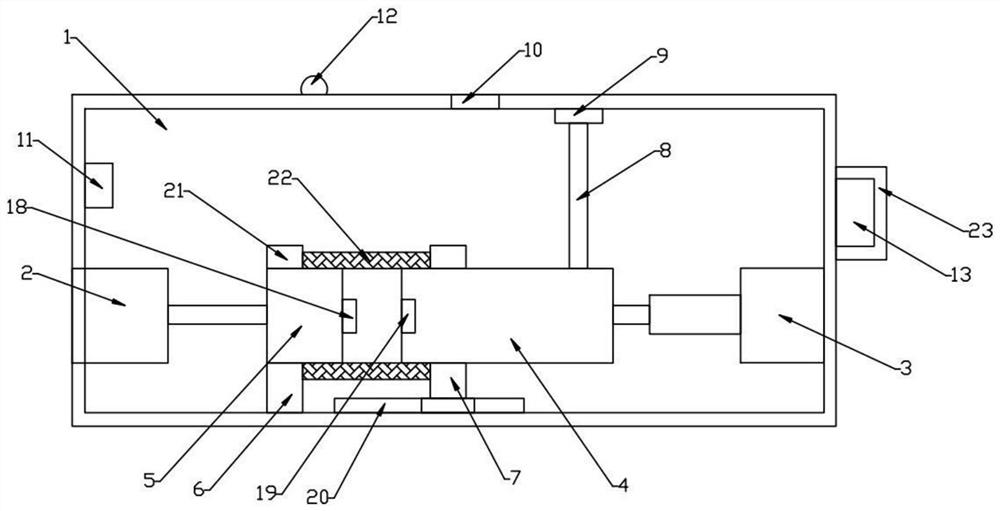
[0019] A computer network information security control device, comprising a chassis 1, a power cord plug 2 is installed on one side of the chassis 1, an electric push rod 3 is installed on the other side of the chassis 2, and the electric push rod 3. The end is connected to the power supply device 4, the power cord plug 2 is connected to the power supply device 5 through a wire, the inner bottom surface of the chassis 1 is equipped with a fixing seat 6, and the power supply device 5 is fixed on the fixing seat 6. The power supply device 4 is fixed on the movable seat 7, the top surface of the power supply device 4 is connected with a vertical line pipe 8, the top of the line pipe 8 is electrically connected to the USB interface 9, and the top surface of the chassis 1 is provided with a The through hole 10 corresponding to the USB interface 9, the inner wall o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com