Secret key negotiation method suitable for secret key sharing of two communication parties
A secret key negotiation and secret key technology, which is applied in the field of information security, can solve the problems of high-end real-time communication control and difficult to meet the demand
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
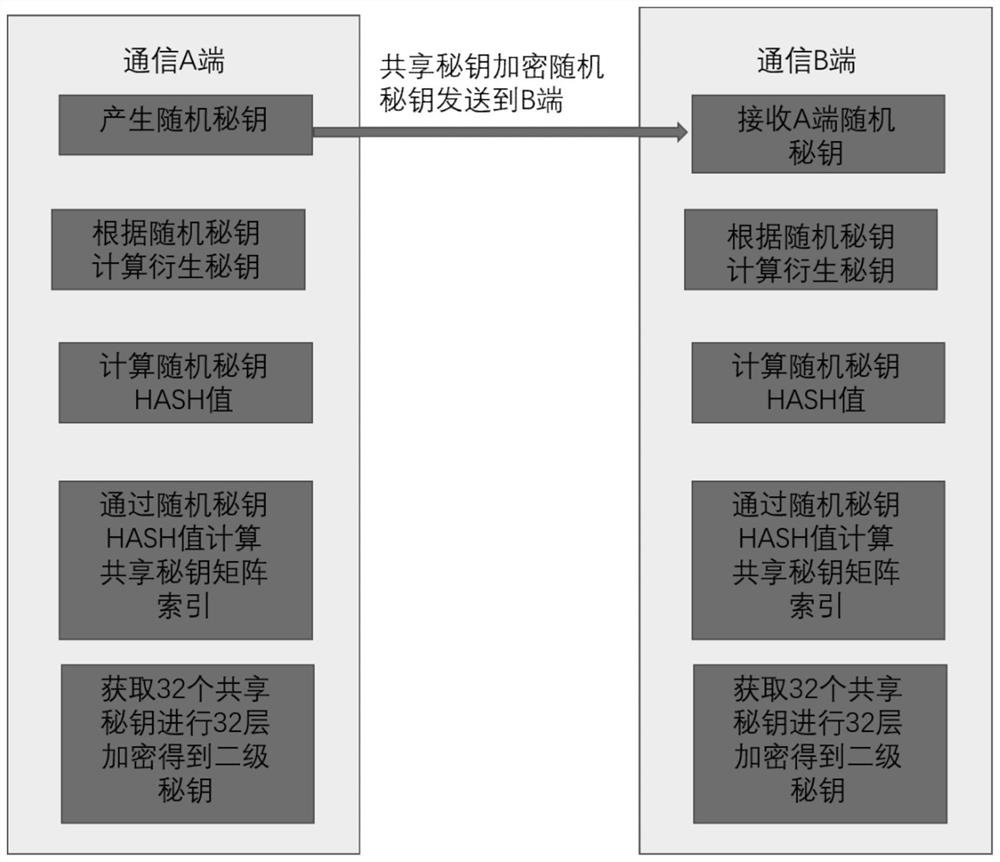
[0037] In order to make the purpose, content and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0038] The invention relates to a method for negotiating a secret key between communication parties, which is particularly suitable for an environment that requires high real-time communication and limited hardware computing resources.
[0039] Need to realize following key content in the present invention:
[0040] 1) Shared secret key matrix
[0041] The shared secret key matrix is composed of 32x32 secret keys. The corresponding element of each row and column is a true random number secret key. The length of the secret key varies according to different requirements. In this invention, a 32-byte true random number secret key is used. , other secret keys of byte size also belong to the scope of the invention. Accor...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap