An access control method, user equipment, and system for the Internet of Things
A technology for access control and user equipment, applied in the field of the Internet of Things, can solve the problems of long time-consuming verification of a single access request, increased access control delay, and key management burden, so as to avoid key management burden, improve response speed, The effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
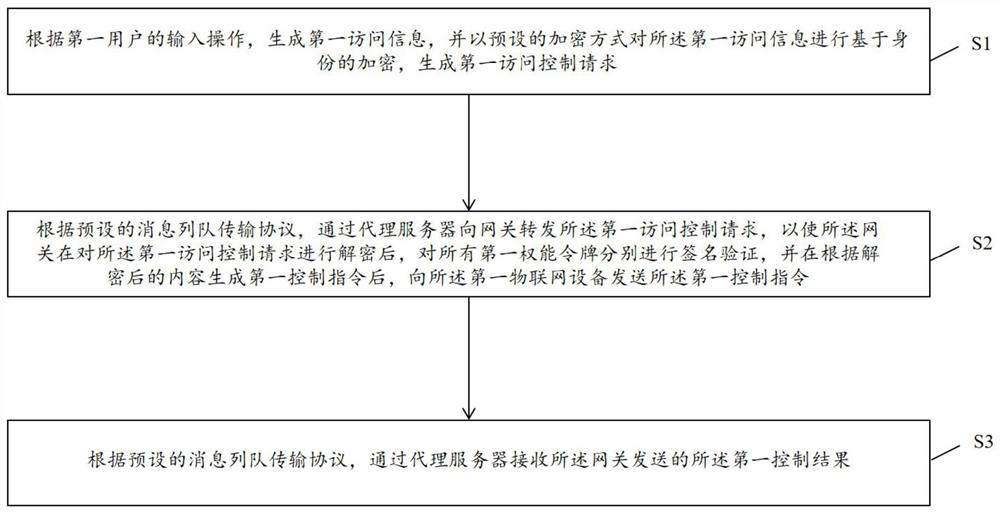
[0030] figure 1 A flowchart of an embodiment of an access control method for the Internet of Things according to the present invention is shown, and the method includes the following steps:
[0031] S1: Generate first access information according to the input operation of the first user, and perform identity-based encryption on the first access information in a preset encryption manner to generate a first access control request.
[0032] To realize the access control process of the IoT device, it is first necessary to determine the first IoT device that the first user wants to access and control according to the input operation of the first user, and the first user expects to control the first IoT device. operation, and obtain the first user's first capability token chain at the same time, so as to verify the legitimacy of the operation later. Therefore, the first access information should include the first capability token chain currently stored in the first user equipment, ...
specific Embodiment 2
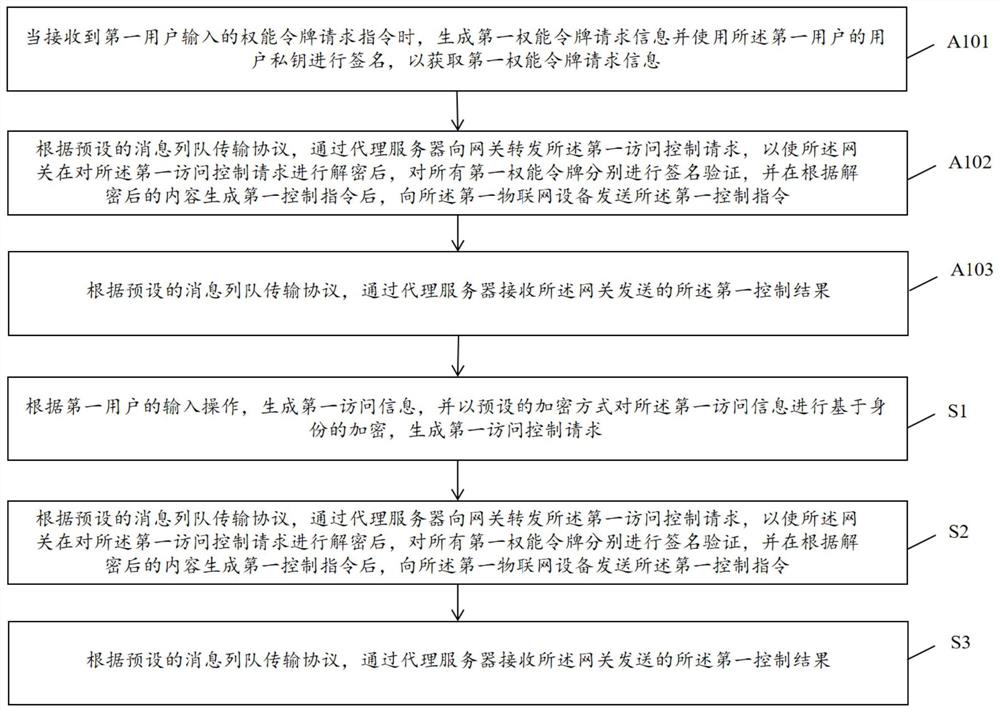
[0047] figure 2 A flowchart showing another embodiment of the access control method for the Internet of Things according to the present invention, the method includes the following steps:
[0048] S1: Generate first access information according to the input operation of the first user, and perform identity-based encryption on the first access information in a preset encryption manner to generate a first access control request.
[0049] In fact, there is a prerequisite for the execution of this step, that is, the first user equipment must currently save the first capability token chain corresponding to the access control request, otherwise it will not be able to prove in the subsequent first access control request that The legitimacy of its identity and operating authority. Therefore, if the first user needs to access and control the first IoT device, he should obtain the first capability token chain by inputting a capability token request instruction to the first user device...
specific Embodiment 3
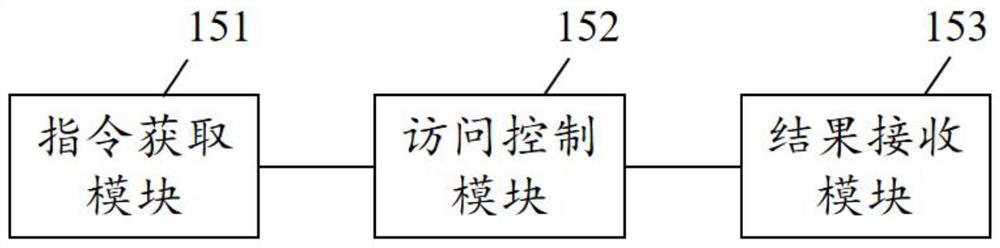
[0074] In addition to the above method, the present invention also provides a user equipment of the Internet of Things. image 3 A structural diagram of an embodiment of a user equipment of the Internet of Things according to the present invention is shown. Such as image 3 As shown, the user equipment 15 includes: an instruction obtaining module 151 , an access control module 152 and a result receiving module 153 .
[0075] The instruction obtaining module 151 is used to generate first access information according to the input operation of the first user, and perform identity-based encryption on the first access information in a preset encryption method to generate a first access control request; The access information includes a first capability token chain currently stored in the first user equipment and a first IoT device to be controlled by the first user; the first capability token chain includes one or more first capability tokens .
[0076] The access control module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com