Harmful act detection system and method
A technology for detecting systems and behaviors, applied in the fields of unstructured text data retrieval, instruments, data processing applications, etc., can solve problems such as large social burdens, and achieve the effect of improving the workplace environment and preventing deterioration.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0028] use Figure 1 to Figure 10 The harmful behavior detection system and method according to Embodiment 1 of the present invention will be described. The harmful behavior detection system of Embodiment 1 is a system including a computer that observes and detects harmful behaviors such as authority harassment among personnel in a workplace environment. The harmful behavior detection method according to the first embodiment is a method having steps executed by the computer of the harmful behavior detection system according to the first embodiment.
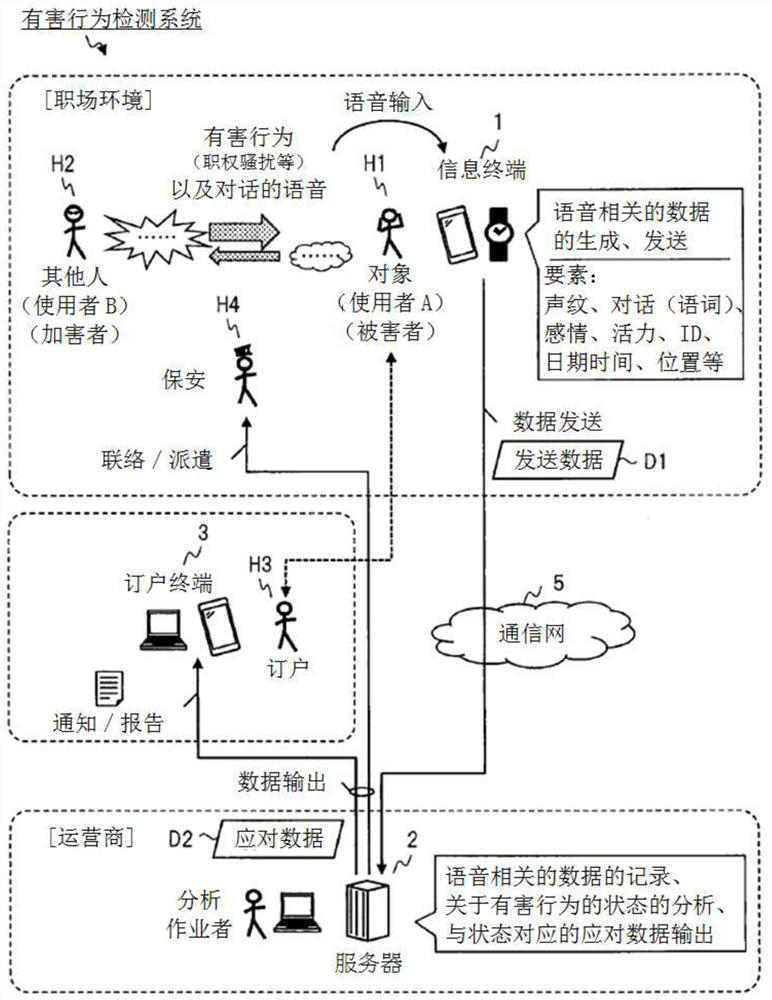
[0029] [Harmful Behavior Detection System (1)]
[0030] figure 1 The basic structure of the harmful behavior detection system of Embodiment 1 is shown. The harmful behavior detection system according to Embodiment 1 includes, as a computer, an information terminal 1 of an object H1 , a server device 2 of a carrier, and a subscriber terminal 3 of a subscriber H3 , and the devices are suitably connected by communication via a com...
Embodiment approach 2
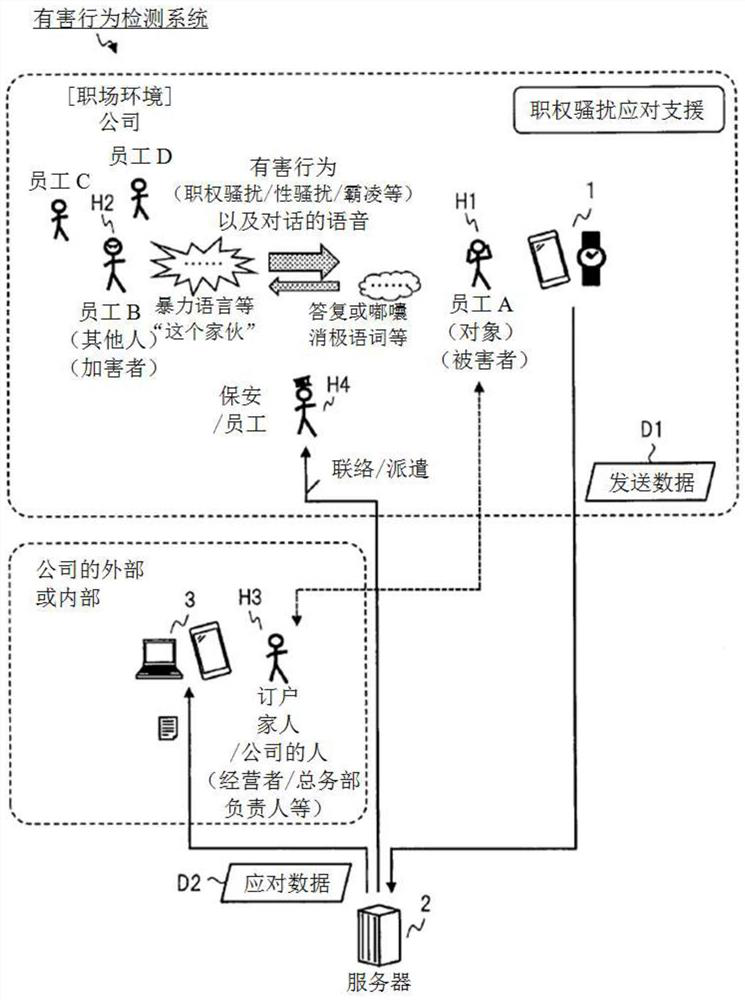
[0148] use Figure 11 , the harmful behavior detection system according to Embodiment 2 of the present invention will be described. The configurations in Embodiment 2 and the like that are different from Embodiment 1 will be described below. Embodiment 1 is a configuration in which the information terminal 1 and the server 2 cooperate to share processing. This sharing can be in various configurations. Embodiment 2 is a configuration in which the main processing related to the harmful behavior detection function is performed in the server 2 .
[0149] Figure 11 The structure of the harmful behavior detection system of Embodiment 2 is shown. as described with Figure 6 In terms of different configurations, the information terminal 1 does not include the voice data processing unit 13 and the index value calculation unit 17 . The data generation and transmission unit 18 of the information terminal 1 obtains voice data, date and time, location, activity data, etc., and const...
Embodiment approach 3
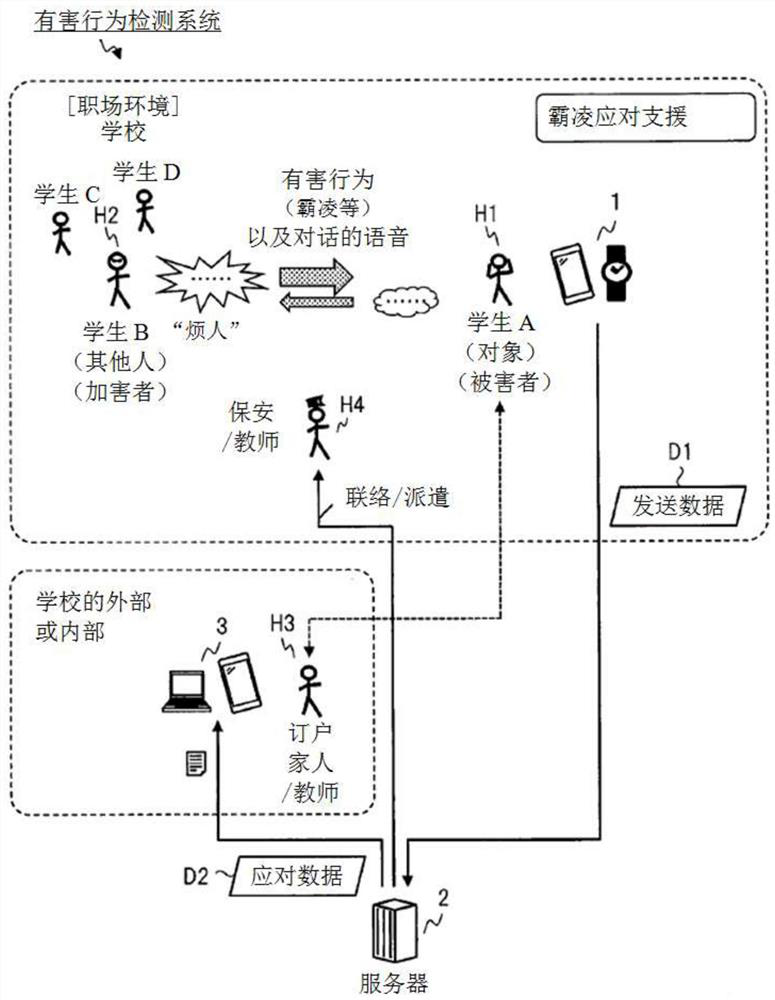
[0153] use Figure 12 , the harmful behavior detection system according to Embodiment 3 of the present invention will be described. Embodiment 3 forms a configuration in which main processing related to the harmful behavior detection function is performed in the information terminal 1 .
[0154] Figure 12 The structure of the harmful behavior detection system of Embodiment 3 is shown. relative to the Figure 6 The information terminal 1 includes an analysis unit 31 , a response operation unit 32 , a communication unit 33 , a display unit 34 and a DB 60 . The analysis unit 31 determines the degree of risk using the index value calculated by the index value calculation unit 17 . The countermeasure operation unit 32 decides countermeasures according to the degree of risk, generates countermeasure data D2, and controls actions such as notification and reporting. The communication unit 33 performs communication with the server 2 , communication with the subscriber terminal 3 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com