Method and device for supporting MLAG active-active access in VXLAN network
A dual-active access and network technology, applied in the virtual network field, can solve problems such as inability to isolate VXLAN service messages, messages not taking effect, and inability to adapt to VXLAN networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
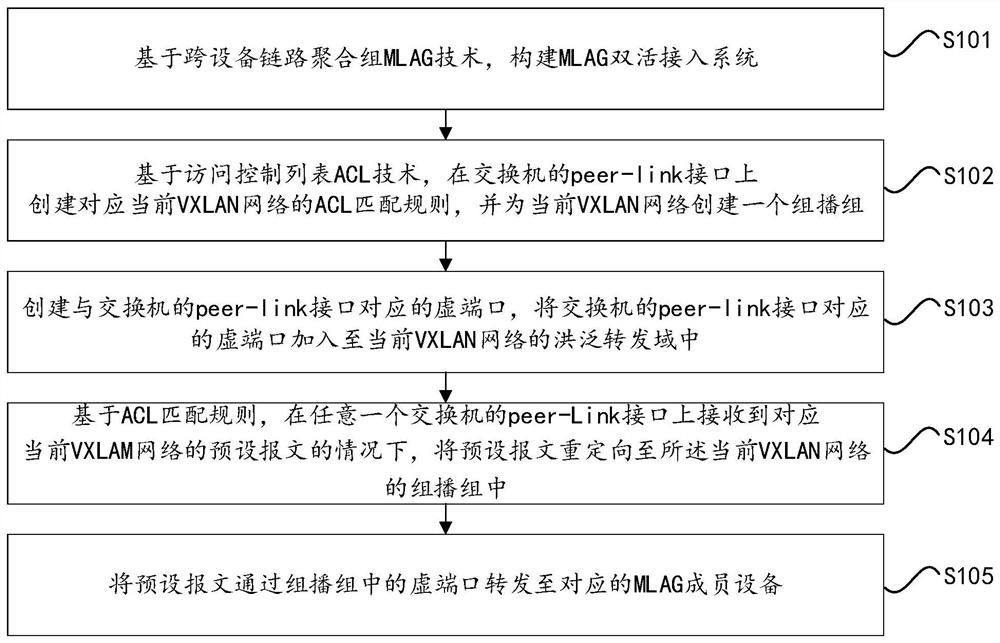
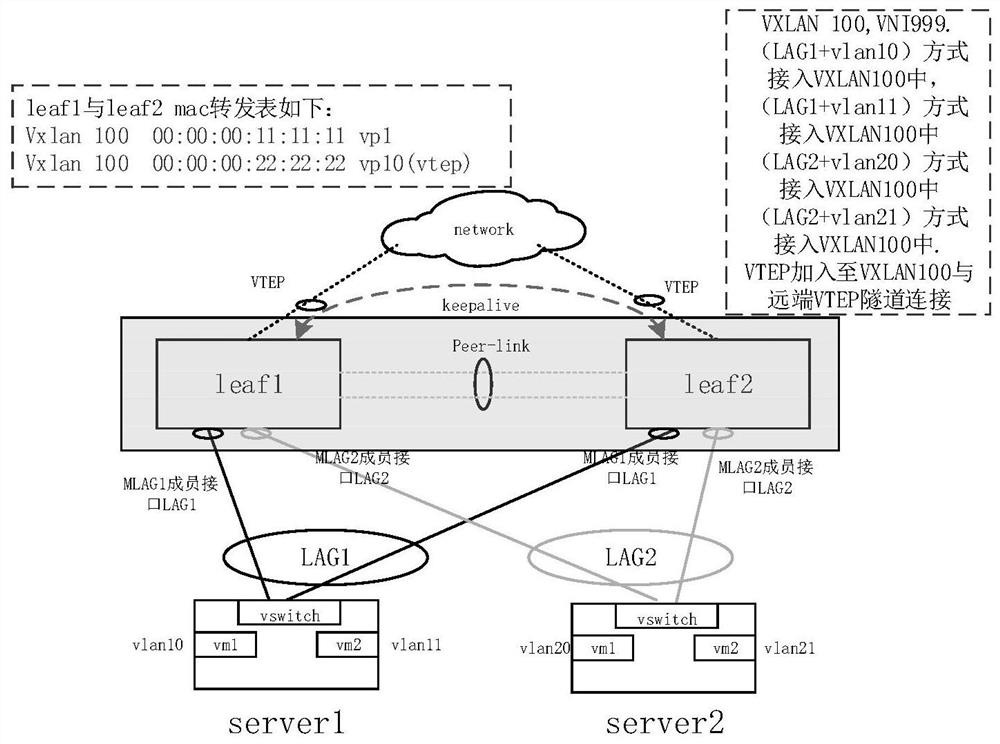
[0054] Embodiment 1: as figure 2 As shown, if the BUM message is forwarded from vm1 on server1 to the VTEP direction, the forwarding process of the BUM message is as follows:
[0055]Step 1: vm1 on server1 sends a BUM message, the VLAN tag of the BUM message is 10, and the destination MAC address is: FF:FF:FF:FF:FF:FF. Since server1 is connected to leaf1 and leaf2 respectively, the BUM message may be forwarded to leaf1 or leaf2, assuming that the LAG algorithm sends the message to leaf1.
[0056] Step 2: The LAG1 member interface in the MLAG1 member interface group on leaf1 receives a BUM packet with VLAN 10 tag and destination MAC address FF:FF:FF:FF:FF:FF broadcast address. According to the VLAN tag of the BUM message, the chip finds that the VXLAN network ID corresponding to the message is 100, that is, the message needs to be flood forwarded in the VXLAN 100 forwarding domain. Then leaf1 sends a BUM message to VP2, VP3, VP4, VP5, and VP10. The VTEP tunnel corresponding...
Embodiment 2
[0058] Embodiment 2: as figure 2 As shown, if a BUM packet is forwarded from the VTEP device on the leaf1 side to vm1 on server1, the forwarding process of the BUM packet is as follows:
[0059] Step 1: Decapsulate the BUM packet through the VTEP device on the leaf1 side, and obtain the inner destination MAC address of the BUM packet as the FF:FF:FF:FF:FF:FF broadcast address. According to the VLAN tag of the BUM message, the chip finds that the VXLAN network ID corresponding to the message is 100, that is, the message needs to be flood forwarded in the VXLAN 100 forwarding domain. Then leaf1 sends a BUM message to VP1, VP2, VP3, VP4, and VP5. Among them, VP1, VP2, VP3, and VP4 correspond to the local MLAG member devices of VXLAN 100 on leaf1, and are finally sent to vm1, vm2 on server1, and vm1, vm2 on server2. At the same time, leaf1 will send a QINQ packet with outer VLAN 4000 and inner VLAN 5 to the peer-link interface.
[0060] Step 2: The peer-link port on Leaf2 rece...
Embodiment 3
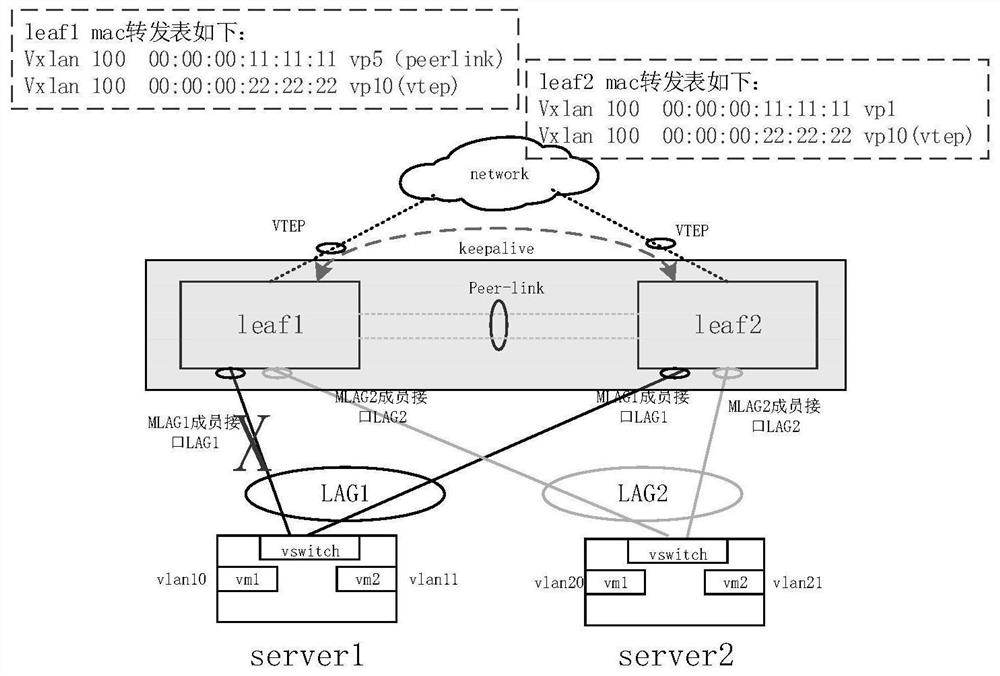
[0061] Embodiment 3: as figure 2 As shown, if the BUM packet is forwarded from the VTEP device on the leaf2 side to the vm1 direction on server1, the forwarding process of the BUM packet is as follows:
[0062] Step 1: Check the table and decapsulate the BUM packet through the VTEP device on the leaf2 side, and obtain the inner destination MAC address of the BUM packet as the FF:FF:FF:FF:FF:FF broadcast address. According to the VLAN tag of the BUM message, the chip finds that the VXLAN network ID corresponding to the message is 100, that is, the message needs to be flood forwarded in the VXLAN 100 forwarding domain. Then leaf2 sends a BUM message to VP1, VP2, VP3, VP4, and VP5. Among them, VP1, VP2, VP3, and VP4 correspond to the local MLAG member devices of VXLAN 100 on leaf2, and are finally sent to vm1 and vm2 on server1, and vm1 and vm2 on server2. At the same time, leaf2 will send a QINQ message with outer VLAN 4000 and inner VLAN 5 to the peer-link interface.
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com