Network security active defense resource configuration method and system
A technology of active defense and network security, applied in the field of energy Internet, it can solve the problems of inability to deal with new attack methods, network security defense is easy to attack but difficult to defend, asymmetry and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention.
[0027] A network security active defense resource configuration method and system, comprising the following steps:
[0028] S1, based on the multi-level network architecture of the Energy Internet, combined with the multi-type construction objects of network deception, analyzes the multi-type active defense resources of energy Internet network security based on network deception;
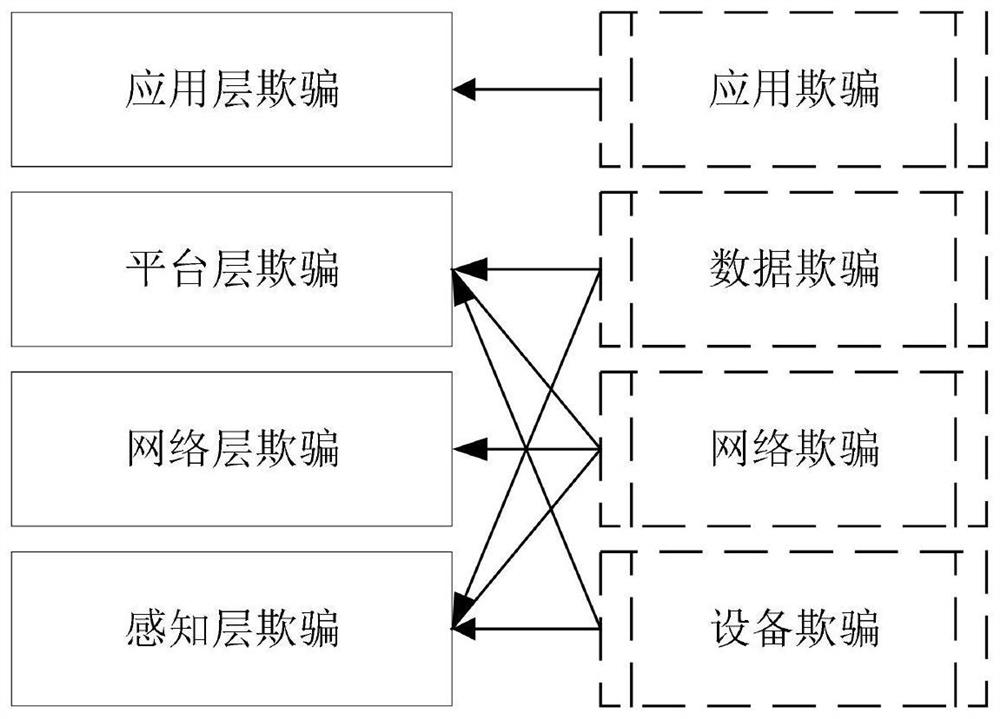
[0029] For example, based on the multi-level network architecture of the Energy Internet, network security active defense resources can be divided into perception layer deception, network layer deception, platform layer deception, and application layer deception;
[0030] For example, comb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com