Vulnerability detection method, device, device and medium based on software dependency analysis
A vulnerability detection and dependency analysis technology, applied in computer security devices, instruments, computing, etc., can solve problems such as large impact range, no security test, and expanded hacker attack range, so as to improve efficiency, reduce manual intervention, and improve loopholes The effect of detection potency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
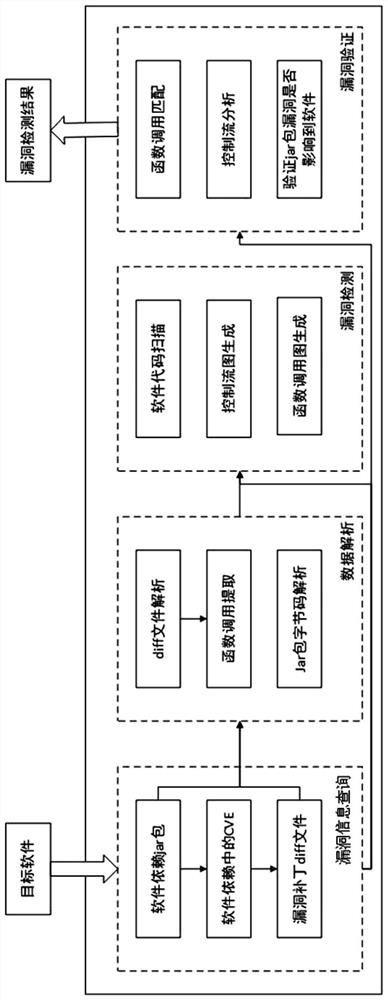
[0047] This embodiment provides a vulnerability detection method based on software dependency analysis, which analyzes the software dependencies (such as JAR packages, etc.) referenced in the target software and their calling functions, and uses the public vulnerability information database to query the software dependencies. The vulnerability information of the target software itself and the software dependencies are combined with the control flow graph and function call graph to determine whether the vulnerability of the software dependencies affects the target software.
[0048] like figure 1 As shown, the vulnerability detection method based on software dependency analysis in this embodiment includes:
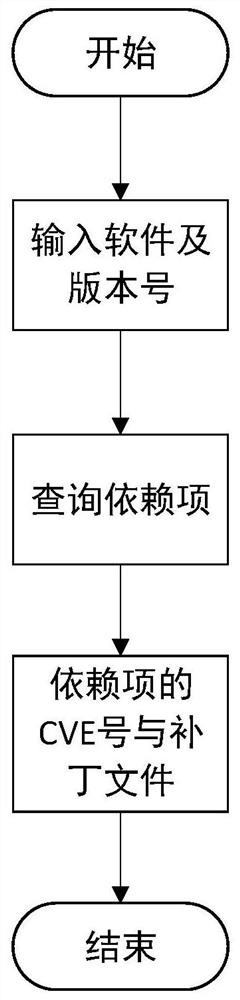
[0049] Vulnerability information query: use the target software and its software version information to query the software dependencies associated in the vulnerability information database and the vulnerability information in the dependencies. The vulnerability information ...
Embodiment 2
[0063] This embodiment is on the basis of Embodiment 1:
[0064] This embodiment provides a vulnerability detection device based on software dependency analysis, including:
[0065] Vulnerability information query module: use the target software and its software version information to query the associated software dependencies in the vulnerability information database and the vulnerability information in the dependencies. The vulnerability information includes CVE vulnerabilities and vulnerability patch diff files in the software dependencies;
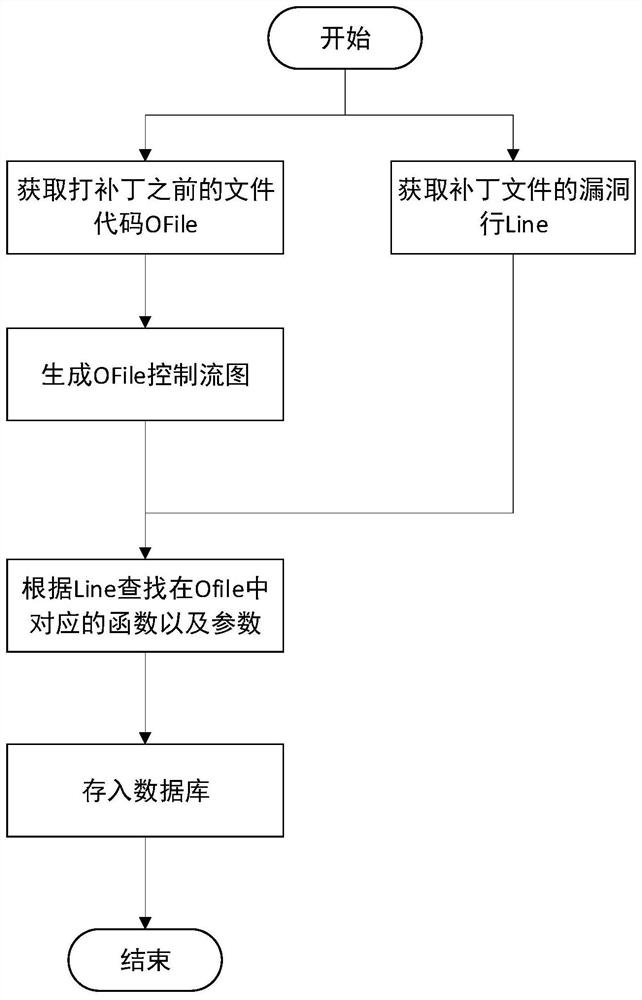
[0066] Data parsing module: parses the vulnerability patch diff file of software dependencies, confirms the specific location of the CVE vulnerability in the software dependency in the dependency code, and extracts the function calls affected by the CVE vulnerability through the source code file of the software dependency;
[0067] Vulnerability detection module: Based on the function call information generated by the data analysis mod...
Embodiment 3
[0074] This embodiment is on the basis of Embodiment 1:
[0075] This embodiment provides a computer device, including a memory and a processor, the memory stores a computer program, and the processor implements the steps of the software dependency analysis-based vulnerability detection method of Embodiment 1 when the processor executes the computer program. The computer program may be in the form of source code, object code, executable file, or some intermediate form.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com