Malicious software detection system
A malware detection system technology, applied in biological neural network models, instruments, platform integrity maintenance, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can easily implement the present invention.
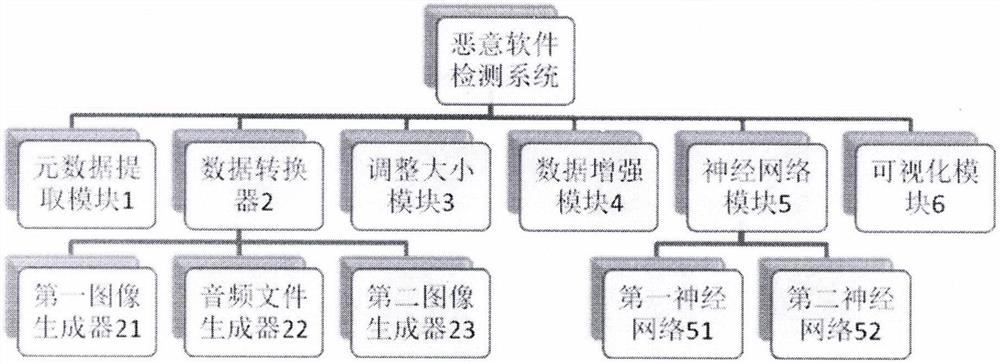
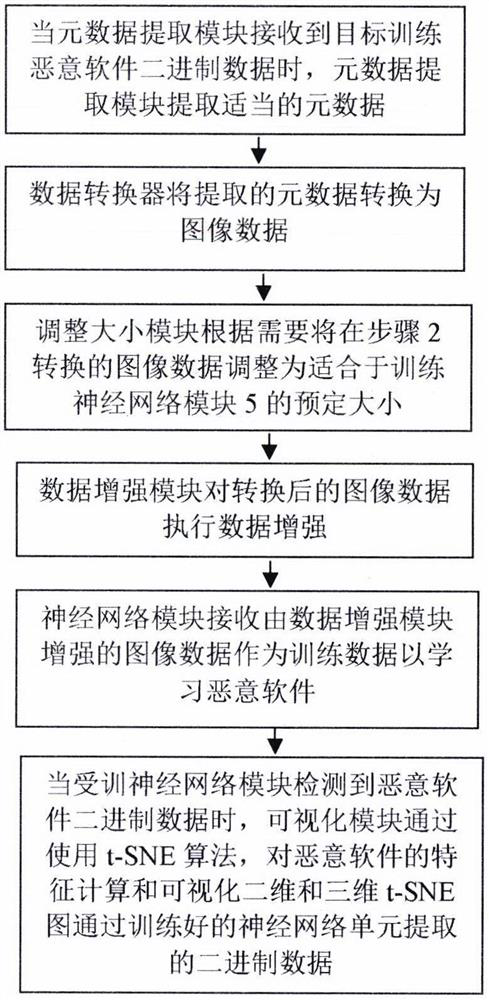
[0023] like figure 1 As shown, the malware detection system of the present application includes a metadata extraction module 1 , a data converter 2 , a resizing module 3 , a data enhancement module 4 , a neural network module 5 and a visualization module 6 .
[0024] Metadata extraction module 1 can receive malware binary data as training data and extract metadata. Malware metadata could be strings, DLL and API calls, byte-n-grams, Opcode-n-grams, PE header fields, network and host activity, image properties, hardware characteristics, and similar. In the case of mobile computing, malware metadata can be permissions and intents, strings, system calls, image attributes, network and host activity, etc.
[0025] The data converter 2 may convert the extracted metadata in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com