Encryption and decryption method for identity authentication of user-free system
A technology of encryption, decryption, and identity verification, applied in user identity/authority verification, transmission system, digital transmission system, etc., can solve the problems of insecure data transmission and slow transmission, and reduce operation time, increase workload, and reduce operation. effect of steps
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The preferred embodiments of the present invention will be described below with reference to the accompanying drawings, and preferred embodiments described herein are intended to illustrate and explain the present invention, and is not intended to limit the invention.
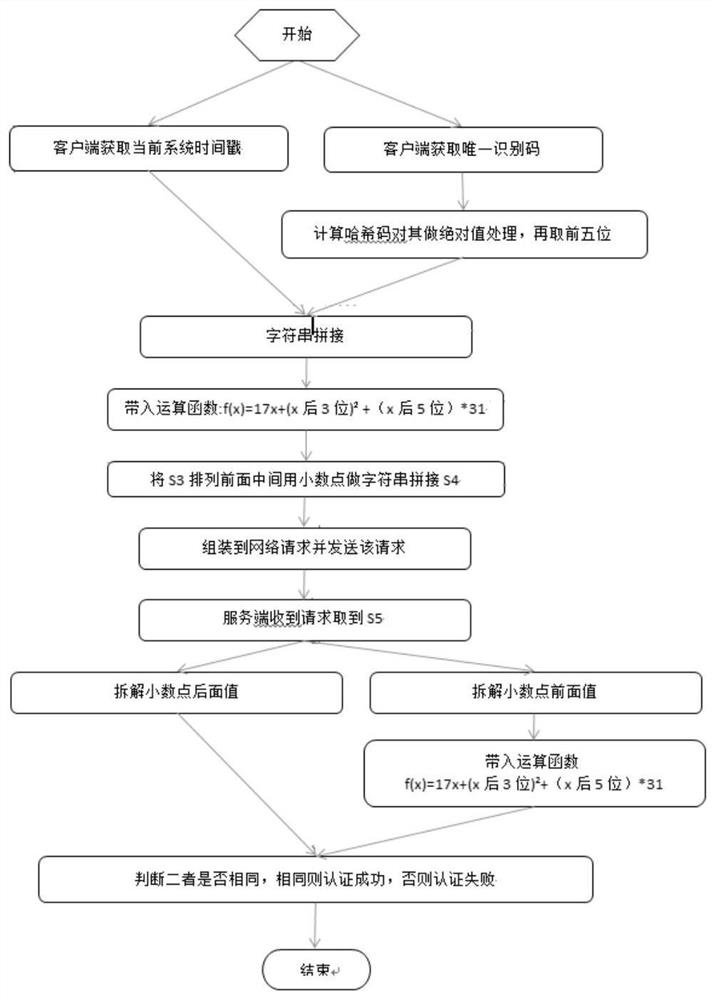
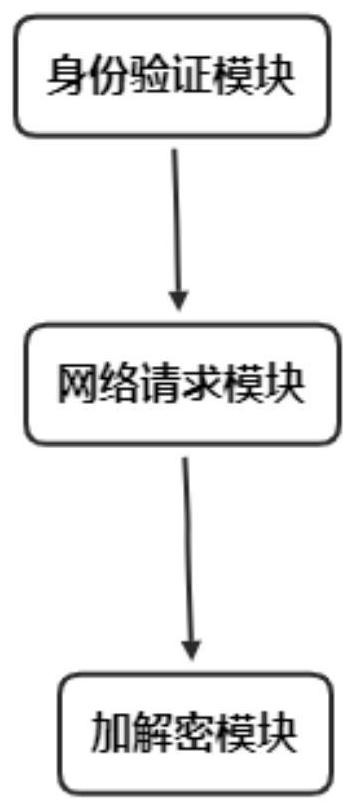
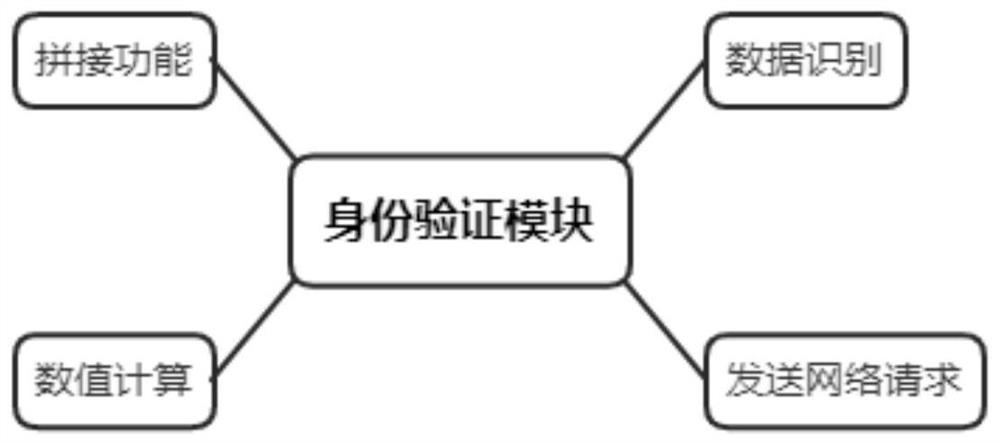
[0074] Append figure 1 Attachment figure 2 Attachment image 3 Attach Figure 4 As shown, embodiments of the present invention provide an authentication and an encryption method based on client autonomous request, including:
[0075] S1 gets the client's timestamp and unique identification code,
[0076] S2 is calculated on the unique identification code and determines the absolute value of the calculation result;
[0077] S3 splicing the timestamp in the absolute value of the preset number, and assembles to a network request sent to the server;
[0078] S4 performs the network request to decompose the decision calculation of the decimal point disassembly, and determine whether the decimal point of the decimal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com