Zero-rule XSS attack detection method based on web application runtime
A technology for application operation and attack detection, applied to electrical components, transmission systems, etc., can solve problems such as easy false positives or false negatives, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057]以下将参照附图,对本发明的优选实施例进行详细的描述。应当理解,优选实施例仅为了说明本发明,而不是为了限制本发明的保护范围。
[0058]本领域技术人员可以理解,除非另有定义,本文所使用的所有的技术和科学术语与属于本申请的技术领域的技术人员通常理解的含义相同;本文中在申请的说明书中所使用的术语只是为了描述具体的实施例的目的,不是旨在于限制本申请;本申请的说明书和权利要求书及上述附图说明中的术语"包括”和"具有”以及它们的任何变形,意图在于覆盖不排他的包含。本申请的说明书和权利要求书或上述附图中的术语"第一”、"第二”等是用于区别不同对象,而不是用于描述特定顺序。
[0059]在本文中提及"实施例”意味着,结合实施例描述的特定特征、结构或特性可以包含在本申请的至少一个实施例中。在说明书中的各个位置出现该短语并不一定均是指相同的实施例,也不是与其它实施例互斥的独立的或备选的实施例。本领域技术人员显式地和隐式地理解的是,本文所描述的实施例可以与其它实施例相结合。
[0060]目前,对待与xss攻击的防御,最主要就是对用户的输入要进行安全过滤,比如对用户的输入过滤掉、alert、iframe等关键字,但黑客通过在上述关键字中间加入空格,即可轻松的避开对scriptalertiframe的过滤,例如将javascript写为javascript;对于安全过滤的策略,还可以通过白名单策略和黑名单策略,通过穷举白名单内的关键词或字符串达到过滤数据的目的。
[0061]以上方法均是通过关键词或关键语句的检测识别XSS攻击,但是,以上方法均是基于已知的字符和关键词,而随着系统的升级和新技术的不断研发,会出现新的XSS攻击策略,曾经的白名单会存在漏报的问题,曾经的黑名单会存在误报的问题,使得目前的防范XSS攻击的方式存在着误报和漏报的问题。
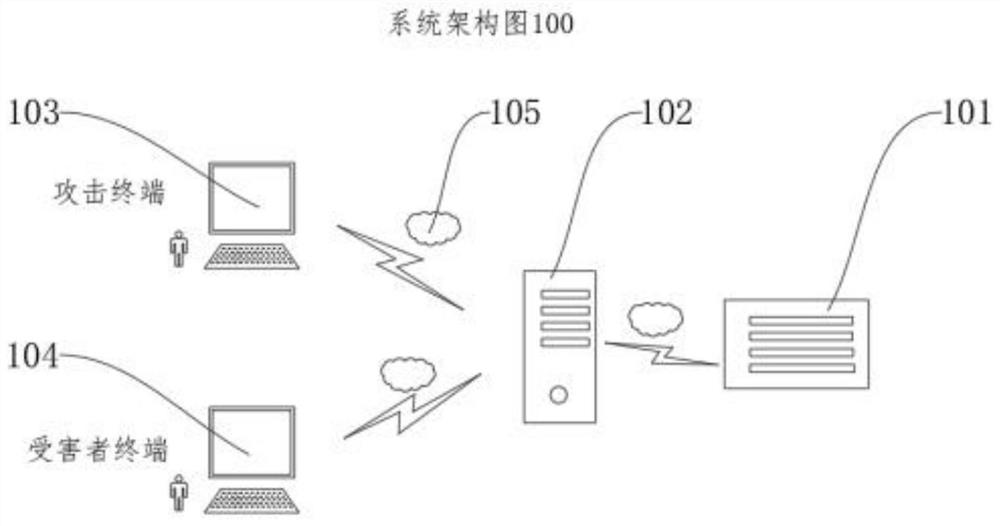
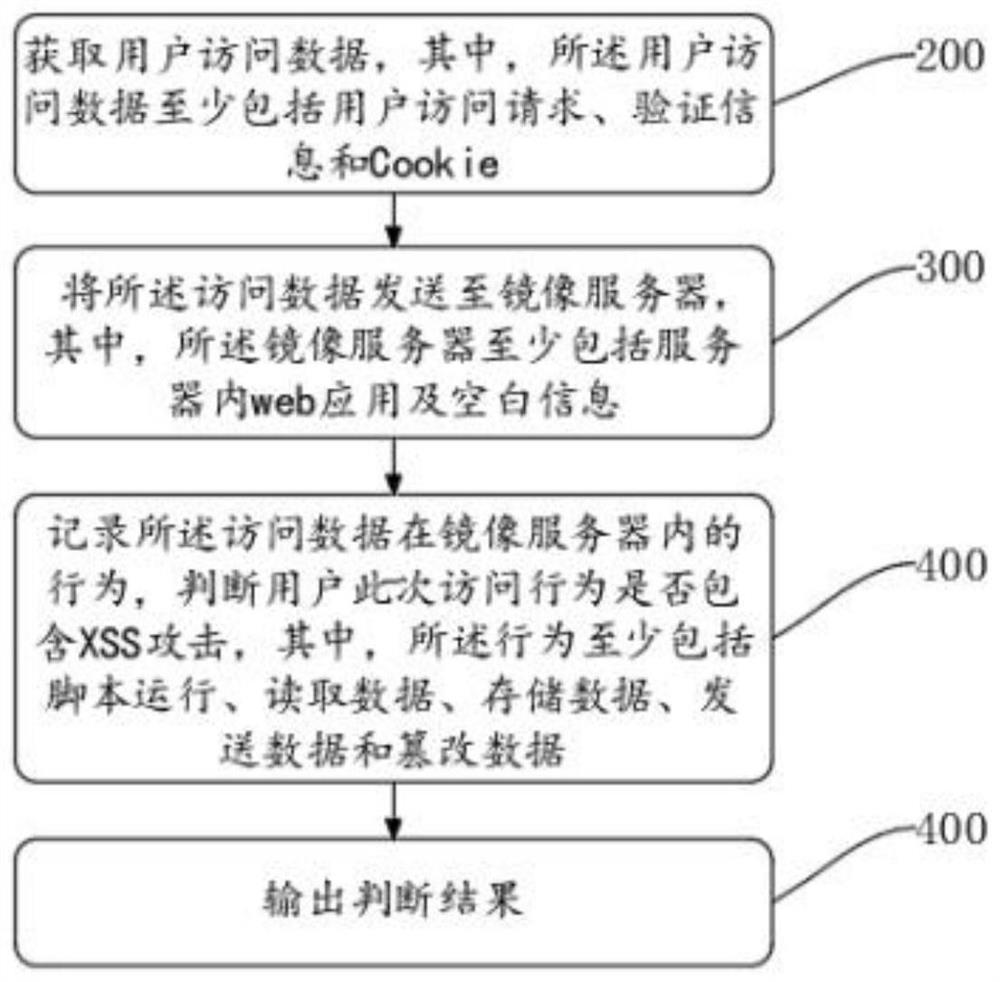
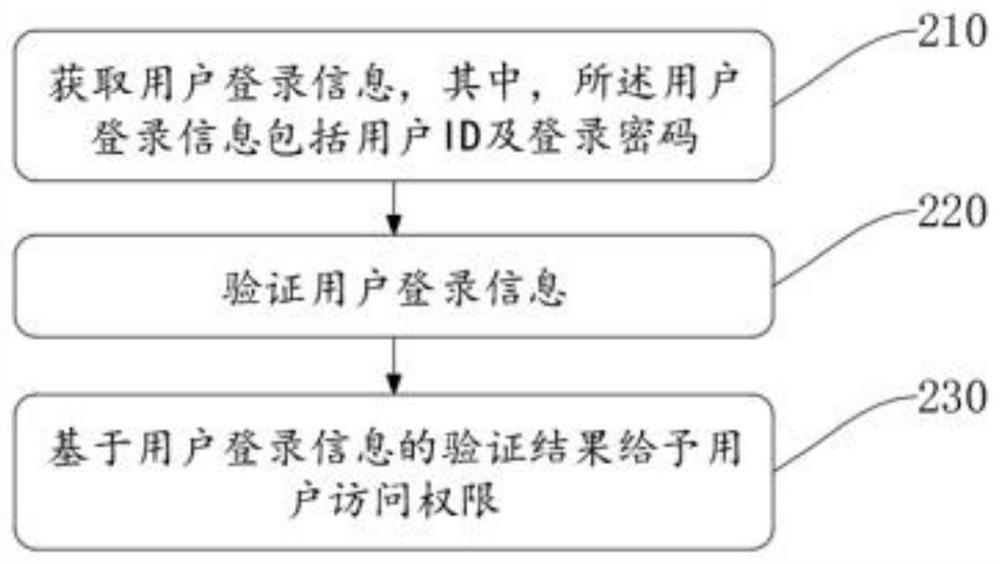
[0062]为解决上述问题,在本发明实施例提供的基于web应用运行时的零规则XSS攻击检测中,通过获取用户访问数据,其中,所述用户访问数据至少包括用户访问请求、验证信息和Cookie;将所述访问数据发送至镜像服务器,其中,所述镜像服务器至少包括服务器内web应用及空白信息;记录所述访问数据在镜像服务器内的行为,判断用户此次访问行为是否包含XSS攻击,其中,所述行为至少包括脚本运行、读取数据、存储数据、发送数据和篡改数据;输出判断结果。本发明实...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com