Method for encrypting authentication failure plaintext information in 5G security protocol
A technology of plaintext information and authentication failure, applied in the field of communication, can solve problems such as poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
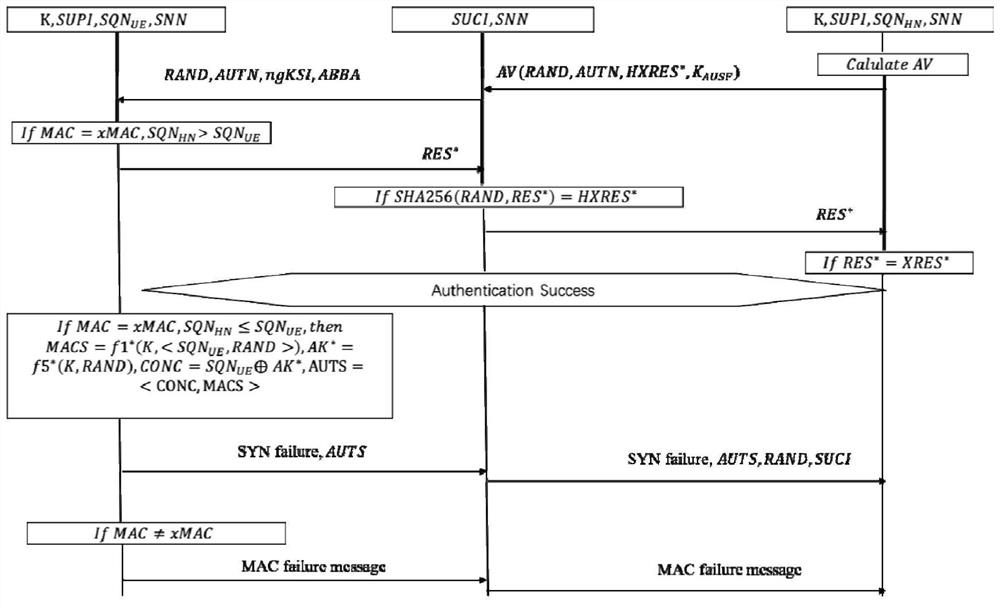
[0039] Such as figure 1 As shown, the authentication process of the 5G AKA security authentication protocol is as follows:
[0040] 1) The home network HN generates the security authentication vector AV(RAND, AUTN, HXRES*, K AUSF ), and then send the authentication vector to the service network SN;
[0041] 2) The SN sends the two parameters RAND and AUTN in the AV, and the remaining two parameters ngKSI and ABBA in the combined authentication, and sends these information to the UE;
[0042] 3) UE performs message authentication code MAC verification and synchronization sequence number SQN verification. If both MAC and SQN are verified, it calculates and generates a response code RES* and sends it to SN, and then sends it to HN for two-way verification;
[0043...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com