Known vulnerability positioning method and device for network equipment
A technology of network equipment and positioning method, which is applied in the direction of computer security devices, instruments, and electrical digital data processing, etc., which can solve the problems of false positives, high cost, and incorrect function matching in vulnerability positioning, so as to reduce workload, improve efficiency, The effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047]In order to make the technical solution of the present invention more obvious and easy to understand, the technical solution in the embodiment of the present invention is clearly and completely described with specific examples and in conjunction with the accompanying drawings.
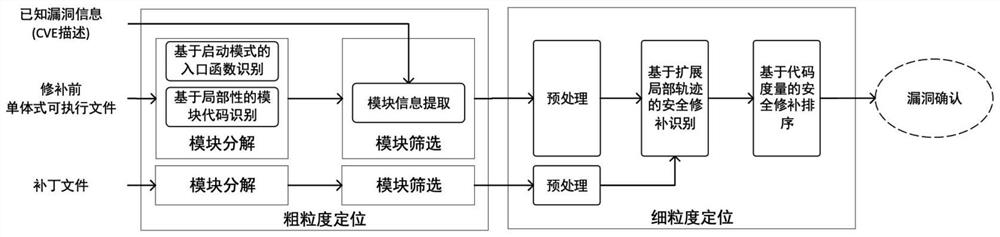
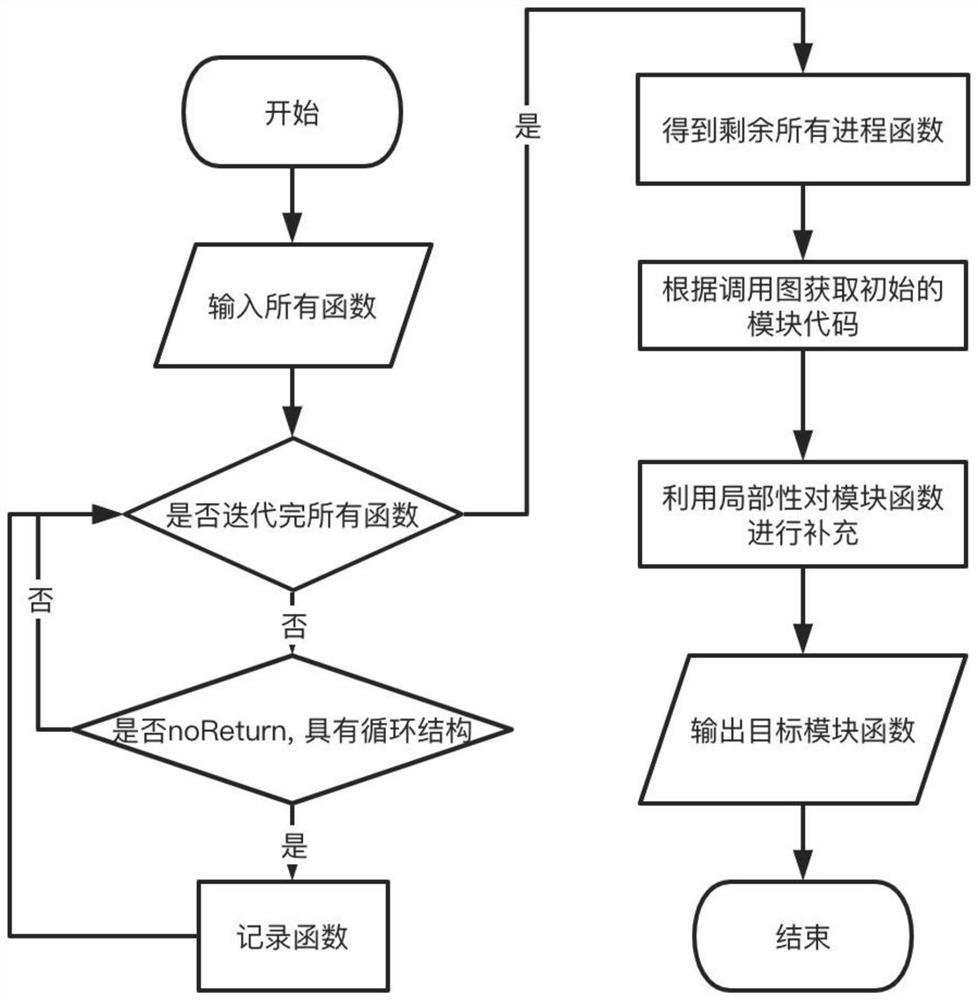
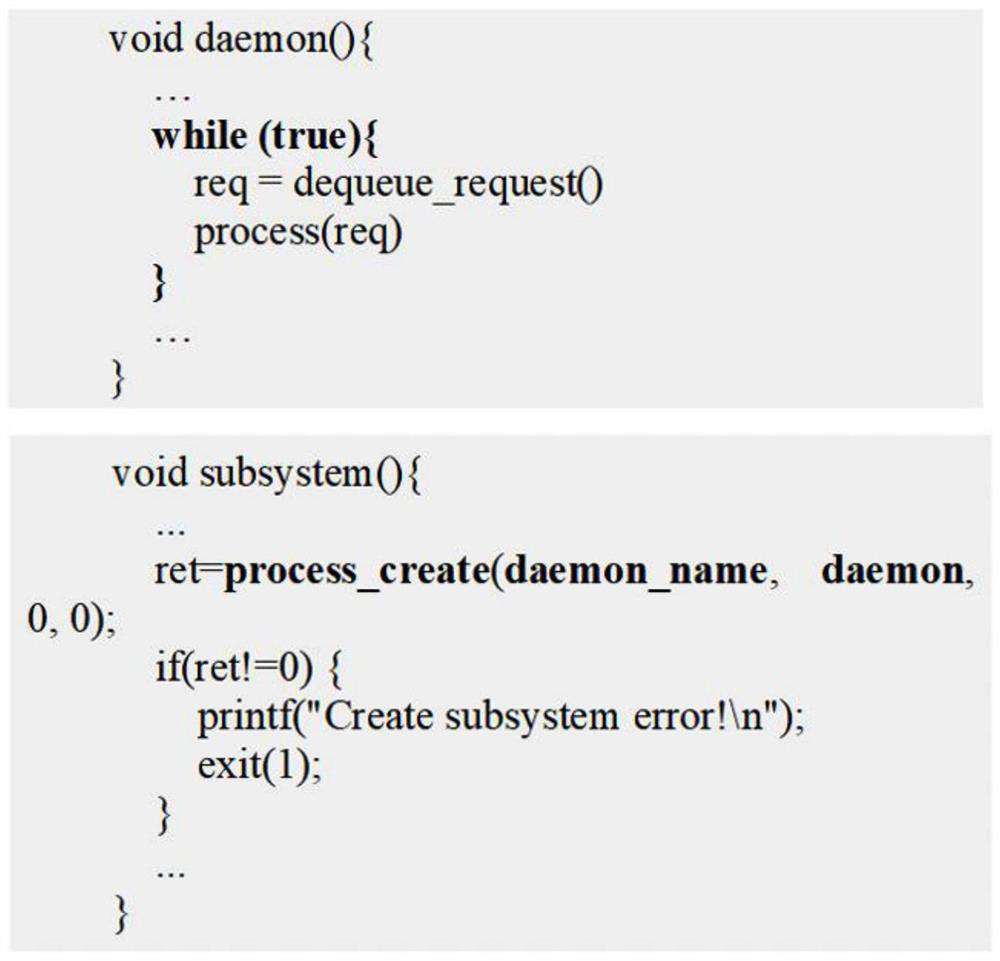
[0048] Network equipment usually encapsulates main functions such as network protocol service code and public operation support code into an executable file, which is called a single executable file in the present invention. The network protocol services usually include SNMP, HTTP, IKE, OSPF, BGP, etc. These single executable files cover all the contents of the management plane, control plane, and data plane. Monolithic executable files are binary files of the main network protocols of some large-scale network devices. Using binary patch comparison technology to locate vulnerabilities in them is an important auxiliary means to analyze the detailed information of vulnerabilities. By locating known ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com