Session control information processing method, device, system and storage medium
An information processing method and session control technology, applied in the Internet field, can solve the problems of encryption algorithm cracking, easy to be stolen by others, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] According to this embodiment, an embodiment of a method for processing session control information is provided.
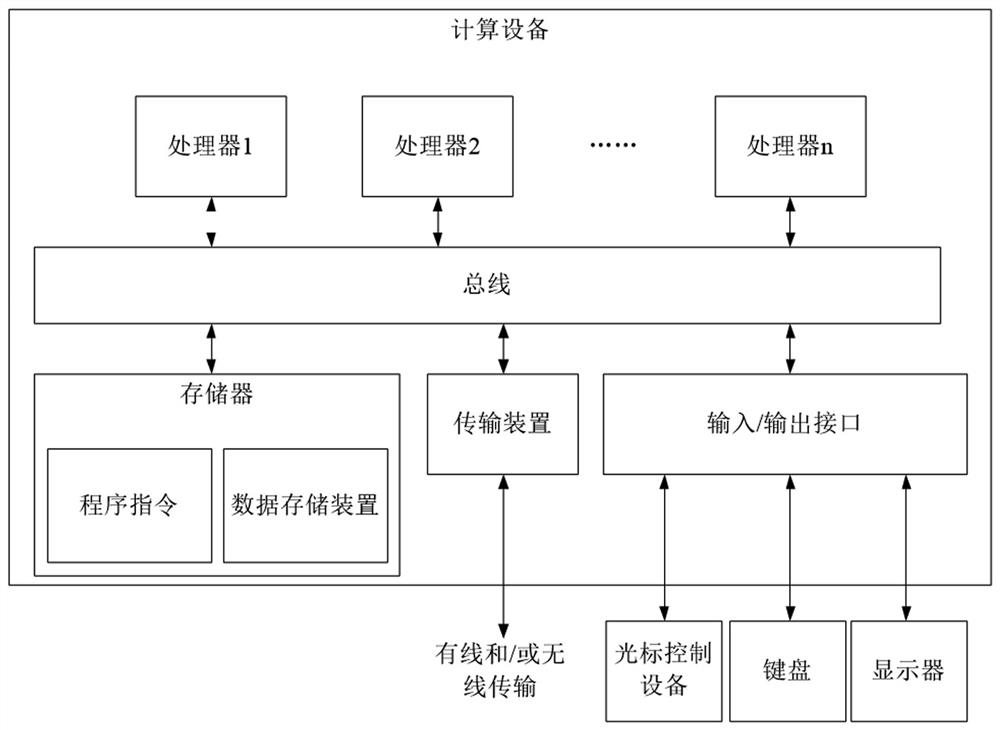
[0034] The method embodiments provided in this embodiment can be executed in mobile terminals, computer terminals, servers or similar computing devices. figure 1 A block diagram of a hardware structure of a computing device for implementing the method for processing session control information provided in this embodiment is shown. Such as figure 1 As shown, the computing device may include one or more processors (processors may include but not limited to processing devices such as microprocessors MCUs or programmable logic devices FPGAs), memory for storing data, and memory for communication functions transmission device. In addition, it can also include: display, input / output interface (I / O interface), universal serial bus (USB) port (which can be included as one of the ports of I / O interface), network interface, power supply and / or camera. Those of ord...
Embodiment 2
[0055] Figure 7 A session control information processing device according to this embodiment is shown, and the device corresponds to the method according to the first aspect of Embodiment 1. refer to Figure 7 As shown, the device includes:
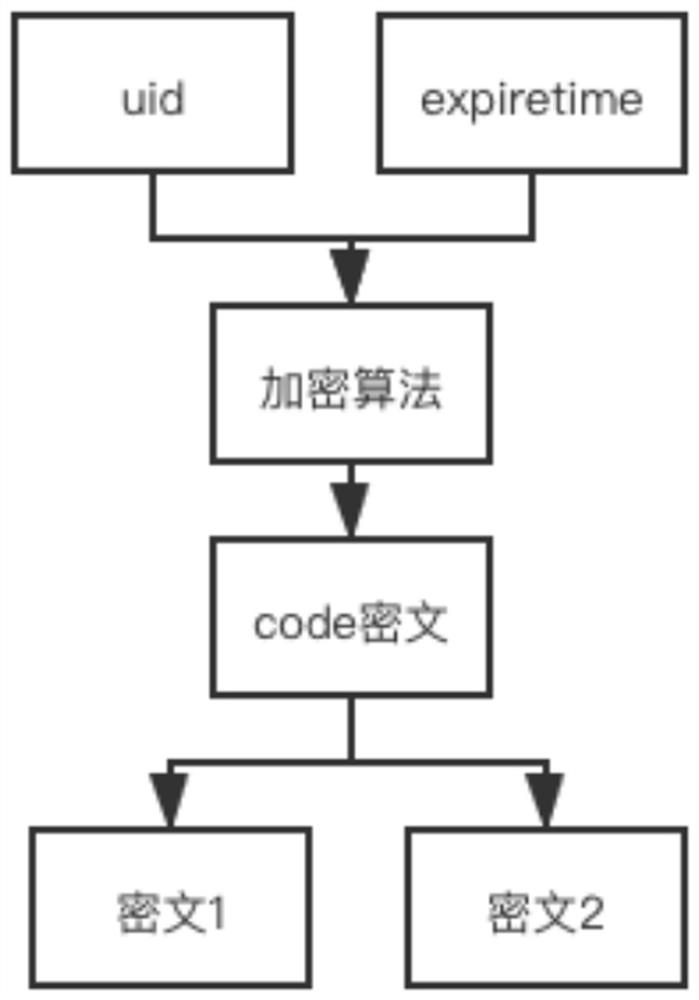
[0056] The data encryption and splitting module 701 is used to use the session control information including the user identity certificate and expiration time as the original information, use an encryption algorithm in the algorithm library matching the codebook to encrypt to obtain the code ciphertext, and split the ciphertext into multiple sections. The so-called cipherbook records the numbers of each algorithm in the algorithm library.
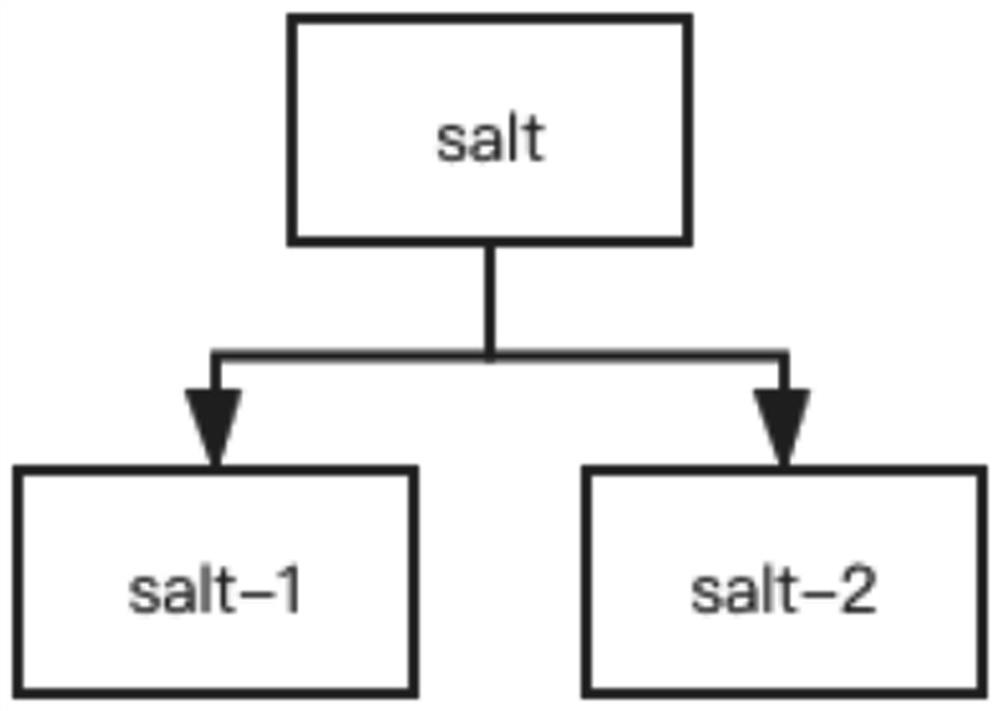
[0057] The salt generating and splitting module 702 is configured to randomly generate a salt and split the salt into multiple parts.
[0058] The combined sorting module 703 is configured to use a sorting algorithm in the above-mentioned algorithm library to sort the ciphertext of the above-menti...
Embodiment 3
[0064] Figure 8 A system for processing session control information according to this embodiment is shown, and the system corresponds to the method described in Embodiment 1. refer to Figure 8 As shown, the system includes:
[0065] processor 801; and
[0066] A memory 802 connected to the processor 801, the memory 802 stores a program, and the processor 801 executes any method provided according to Embodiment 1 when the program is running.
[0067] Although the description of Embodiment 3 is not comprehensively described herein, those of ordinary skill in the art can understand that its specific implementation corresponds to the method in Embodiment 1, and the same technical advantages and effects can be obtained.
[0068] The serial numbers of the above embodiments of the present invention are for description only, and do not represent the advantages and disadvantages of the embodiments.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com