Safety alarm event processing method and device, equipment and storage medium
A technology of alarm events and processing methods, applied in computer security devices, electronic digital data processing, hardware monitoring, etc., can solve problems that affect national cyberspace sovereignty, security and development interests, affect the healthy development of enterprises, and flood security alarms, etc. Achieve scientific network security defense, maximize cost-effectiveness, and reduce serious impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
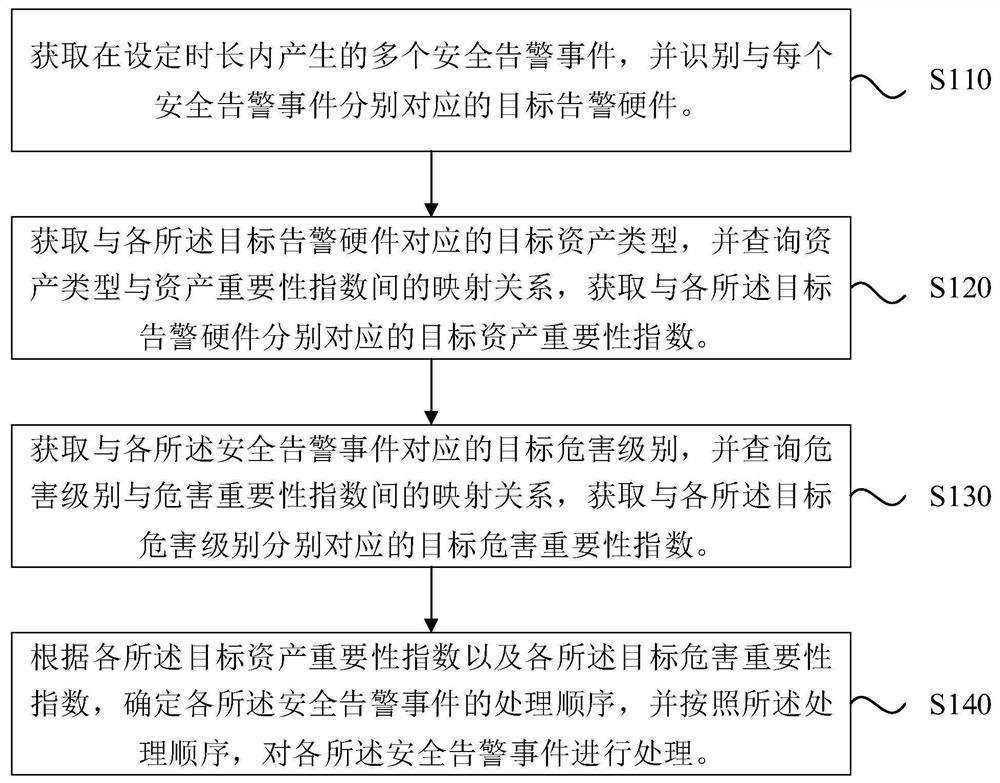
[0025] Figure 1a It is a flowchart of a method for processing a security alarm event provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation where multiple hardware assets are alarmed at the same time, and the defense order of multiple alarming hardware assets is determined. The method of this embodiment may be executed by a device for processing security alarm events, which device may be implemented in the form of software and / or hardware, and which device may be configured in a computer device such as a server or a terminal device.
[0026] Correspondingly, the method specifically includes the following steps:
[0027] S110. Obtain multiple security alarm events generated within a set time period, and identify target alarm hardware corresponding to each security alarm event.
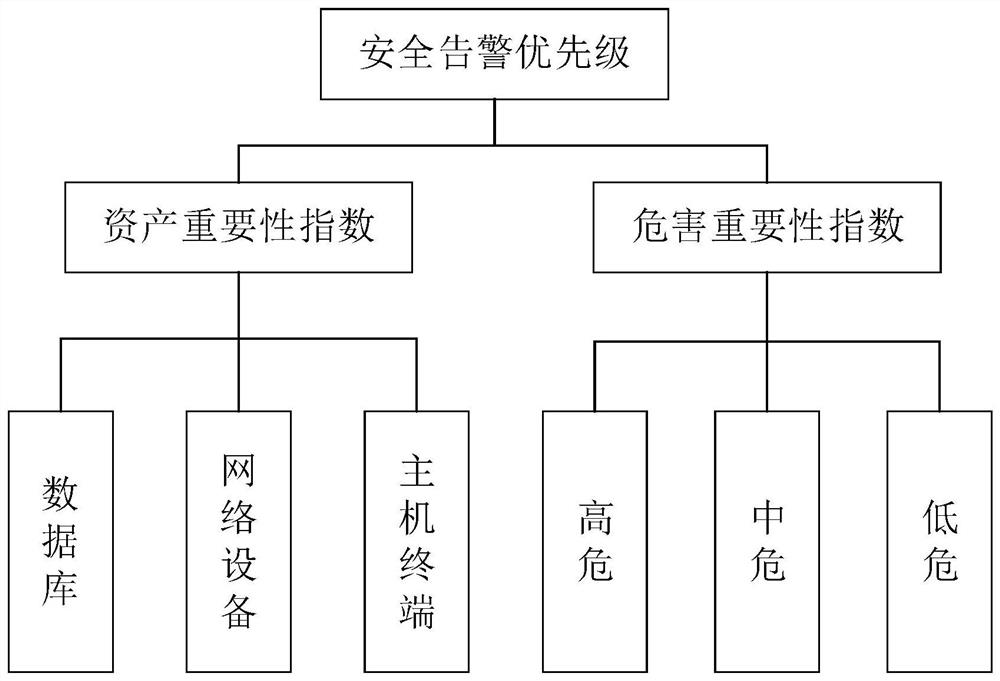
[0028] Among them, the security alarm event can be the threat in the server or cloud product detected by the cloud security center. These threats can be an a...
Embodiment 2
[0108] figure 2 It is a schematic structural diagram of a security alarm event processing device provided in Embodiment 2 of the present invention. The security alarm event processing device provided in this embodiment can be implemented by software and / or hardware, and can be configured in a server or a terminal A method for processing a security alarm event in an embodiment of the present invention is implemented in a device. Such as figure 2 As shown, the device may specifically include: a security alarm event acquisition module 210, a target asset importance index acquisition module 220, a target hazard importance index acquisition module 230 and a processing sequence determination module 240.
[0109] Wherein, the security alarm event acquisition module 210 is used to acquire multiple security alarm events generated within the set duration, and identify target alarm hardware corresponding to each security alarm event;
[0110] The target asset importance index acquisi...
Embodiment 3
[0135] image 3 It is a structural diagram of a computer device provided in Embodiment 3 of the present invention. Such as image 3 As shown, the device includes a processor 310, a memory 320, an input device 330, and an output device 340; the number of processors 310 in the device can be one or more, image 3 Take a processor 310 as an example; the processor 310, memory 320, input device 330 and output device 340 in the device can be connected by bus or other methods, image 3 Take connection via bus as an example.
[0136] The memory 320, as a computer-readable storage medium, can be used to store software programs, computer-executable programs and modules, such as program instructions / modules corresponding to the security alarm event processing method in the embodiment of the present invention (for example, security alarm event acquisition module 210, target asset importance index acquisition module 220, target hazard importance index acquisition module 230 and processin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com