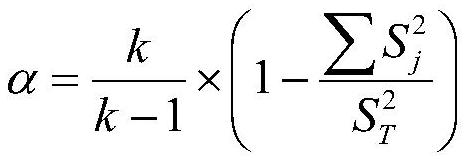Individual cognitive security awareness assessment method based on questionnaire survey
A consciousness and questionnaire technology, applied in the field of individual cognitive security awareness assessment based on questionnaire survey, can solve the problems of low cost of social engineering attack, small attack risk, limited effect of defense methods, etc., and achieve intuitive physical meaning, strong robustness and reasonableness sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
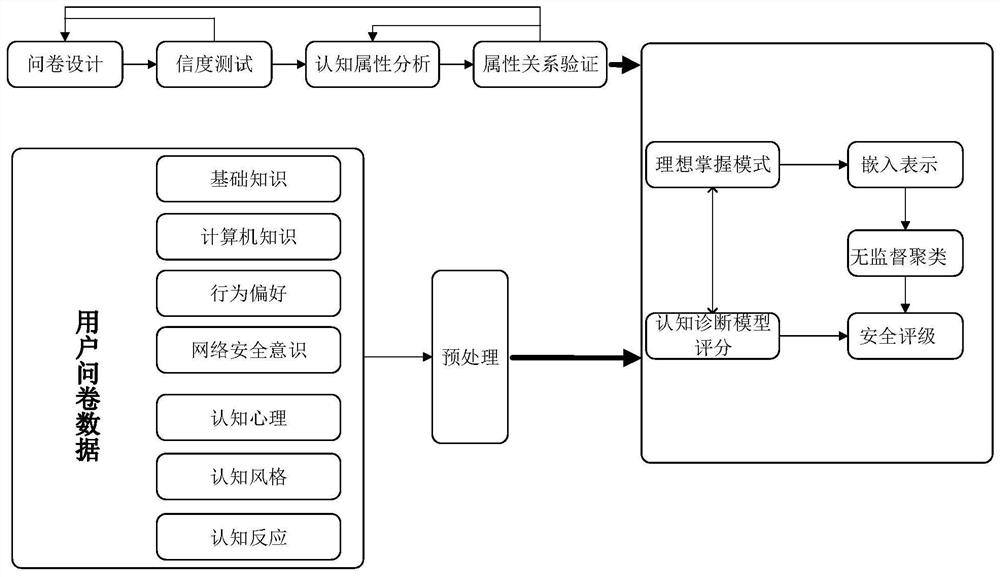
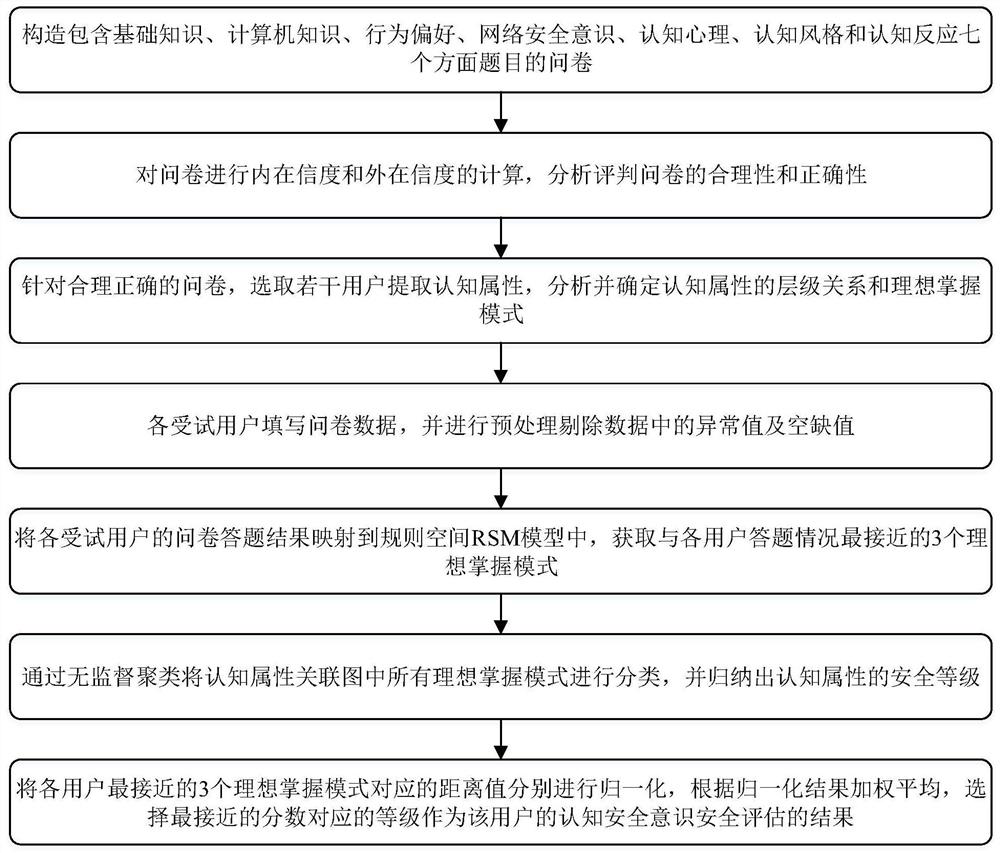
[0120] First of all, the designed questionnaire refers to the HAIS-Q (Human Aspects of Information Security Questionnaire) model, and sets the questions covering basic knowledge, computer knowledge, behavior preference, network security awareness, cognitive psychology, cognitive style and cognitive response. ; and use the pre-test results to analyze the reliability of the questionnaire to judge the rationality and correctness of the questionnaire;
[0121] Then, analyze the cognitive attributes of the content related to network security and social engineering covered by the questionnaire, and determine the hierarchical relationship of cognitive attributes and the ideal mastery mode;
[0122] Further, the questionnaire data filled in by the subjects is preprocessed, and the outliers and blank values in the data are eliminated; the cognitive level and structure of the subjects are analyzed by using the cognitive diagnostic model;
[0123] Classify desirable mastery patterns by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com