High-security terminal system based on cloud computing, and equipment and use method thereof
A terminal system and security technology, applied in the field of cloud computing, can solve problems such as single method, poor data encryption and decryption effect, and achieve the effect of avoiding malicious theft, high security, and high protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
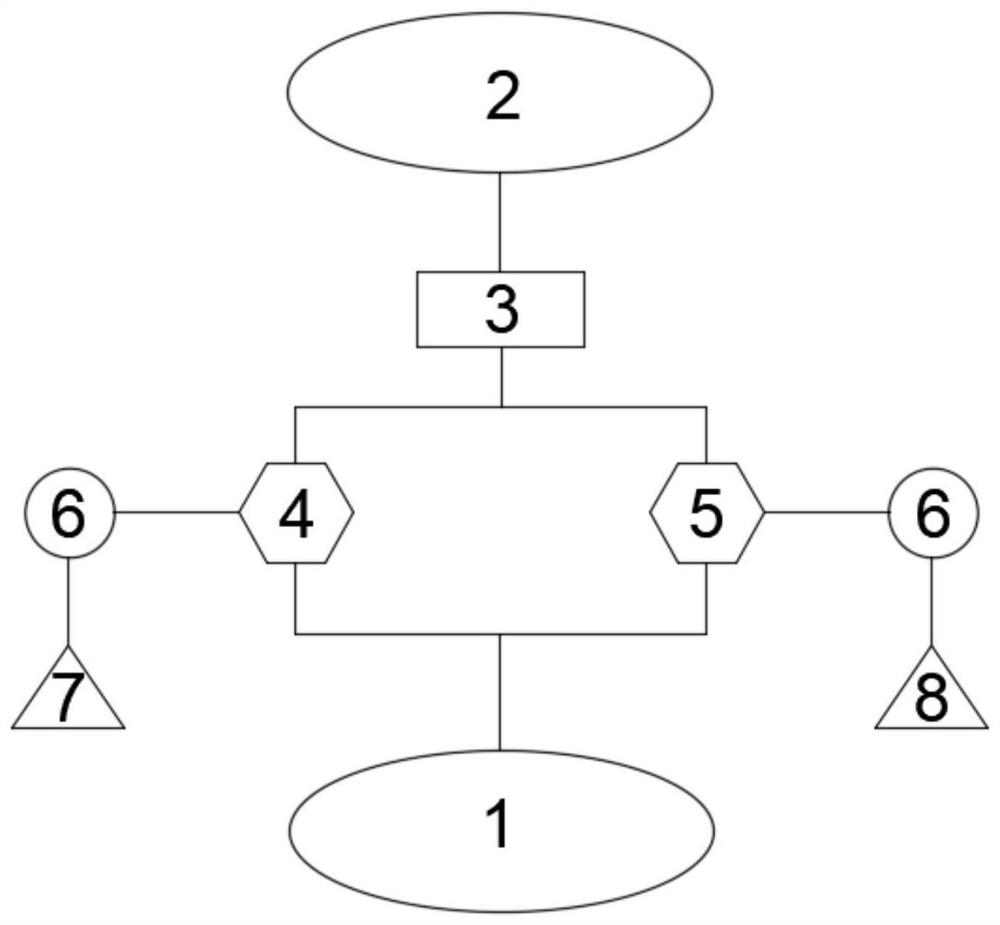
[0030] Such as figure 1 Shown:
[0031] A terminal system with high security based on cloud computing, including a control terminal module 1, a cloud computing server 2, a communication module 3, an encryption module 4 and a decryption module 5, and the control terminal module 1 is connected to the cloud computing server 2 through the communication module 3 The communication module 3 is used to upload data to the cloud computing server 2 or download data from the cloud computing server 2, and the communication module 3 includes one or more of a mobile communication module, a WIFI communication module or a Bluetooth communication module. The communication module 3 transmits bidirectionally.
[0032] The encryption module 4 and the decryption module 5 are respectively connected with the control terminal module 1, the encryption module 4 is used to encrypt the data to be uploaded, the decryption module 5 is used to decrypt the data downloaded from the cloud computing server 2, a...
Embodiment 2
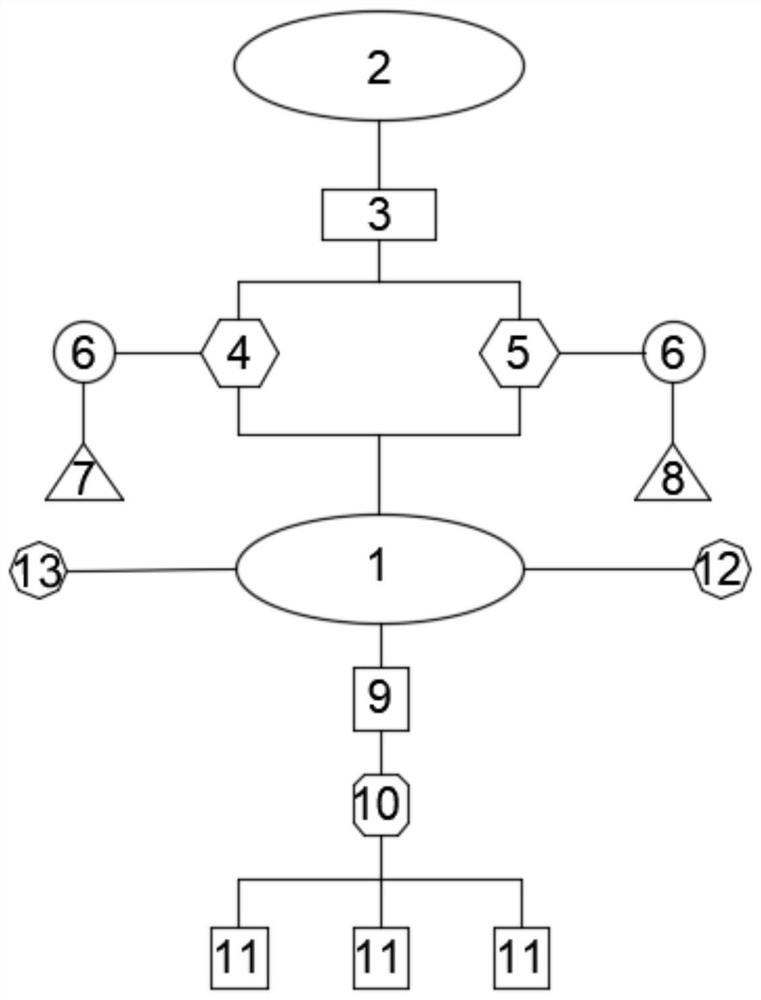
[0034] Such as figure 2 Shown:
[0035] The structure of this embodiment is basically the same as that of Embodiment 1, the difference is that the control terminal module 1 of this embodiment is connected to the input and output interface 10 through the device communication module 9, and the control terminal module 1 can be connected to multiple equipment terminal 11. The control terminal module 1 is also connected with a comparison module 12, which is used for comparing the received password data with the pre-stored user password. The control terminal module 1 is also connected with a retrieval module 13, and the retrieval module 13 is used for retrieving data from the cloud computing server 2.
Embodiment 3
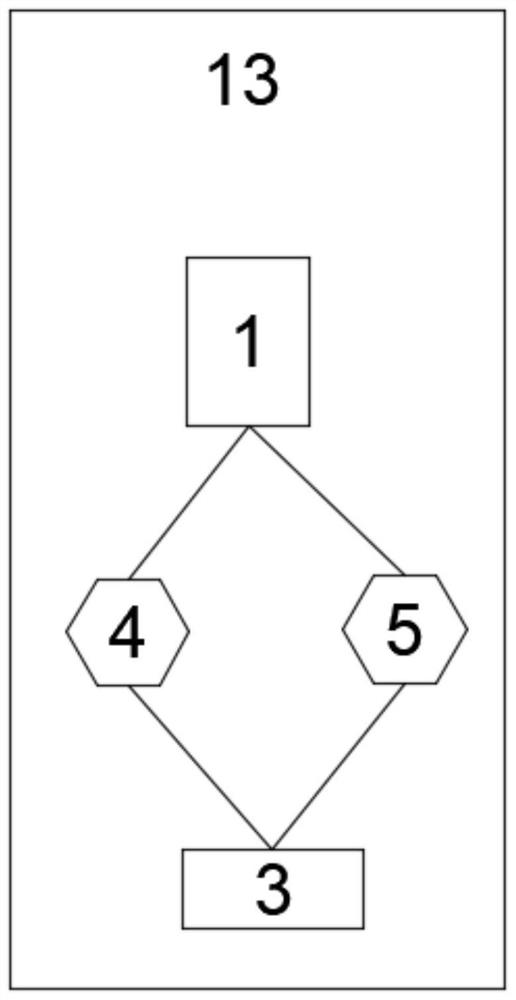
[0037] Such as image 3 Shown:
[0038] A terminal device with high security based on cloud computing, including a control terminal device 14, on which a control terminal module 1, a communication module 3, an encryption module 4 and a decryption module 5 are installed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com