Anomaly detection method based on cloud edge fusion environment
An anomaly detection and integrated environment technology, applied in the field of the Internet of Things, can solve the problems of invalid data transmission, large energy consumption, and inaccurate detection results, and achieve the effects of expanding the scope, improving accuracy, and reducing resource and energy consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
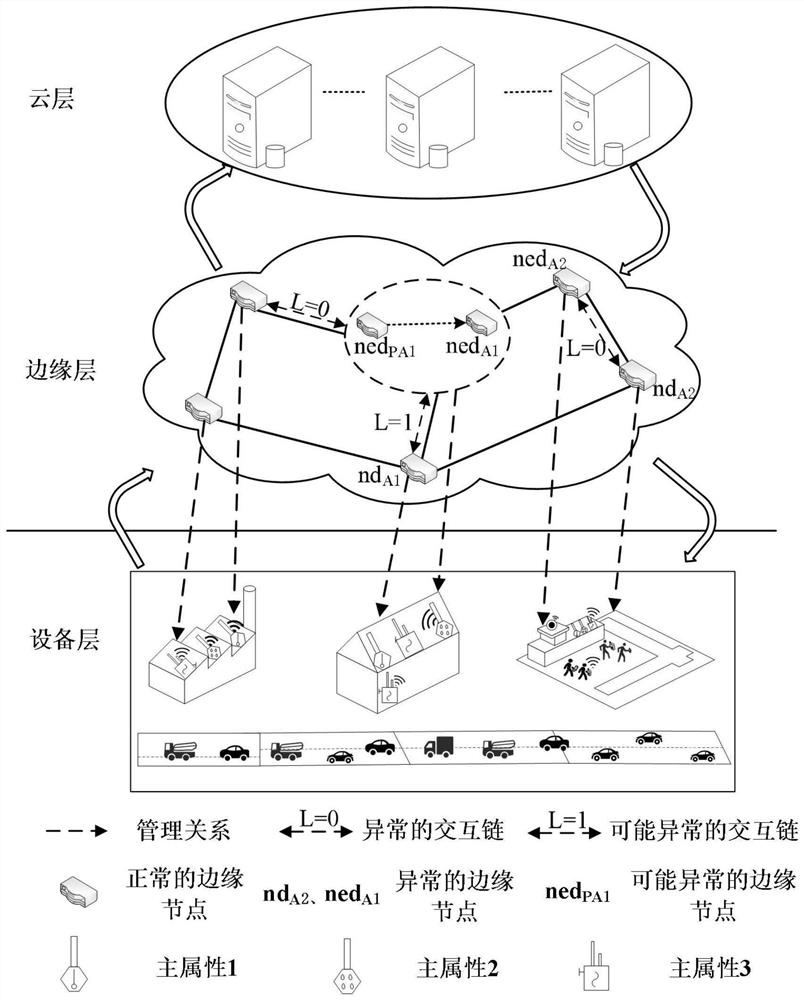
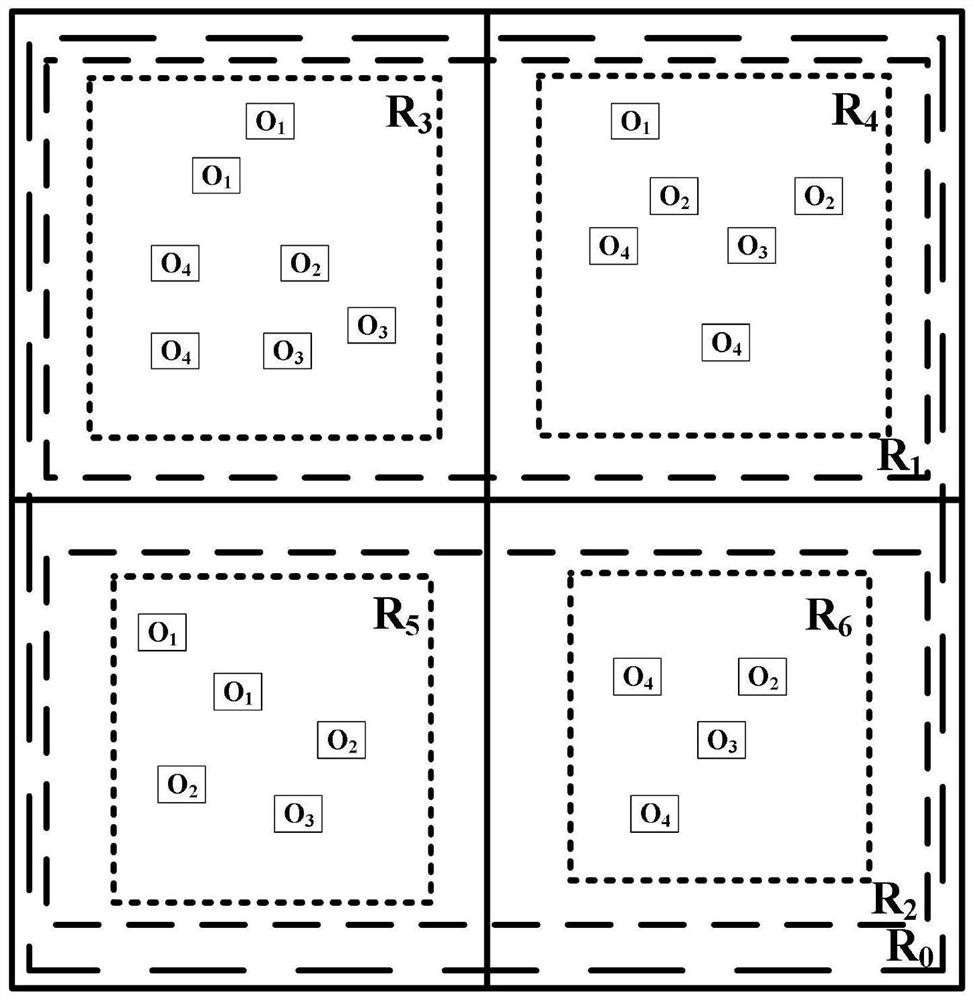
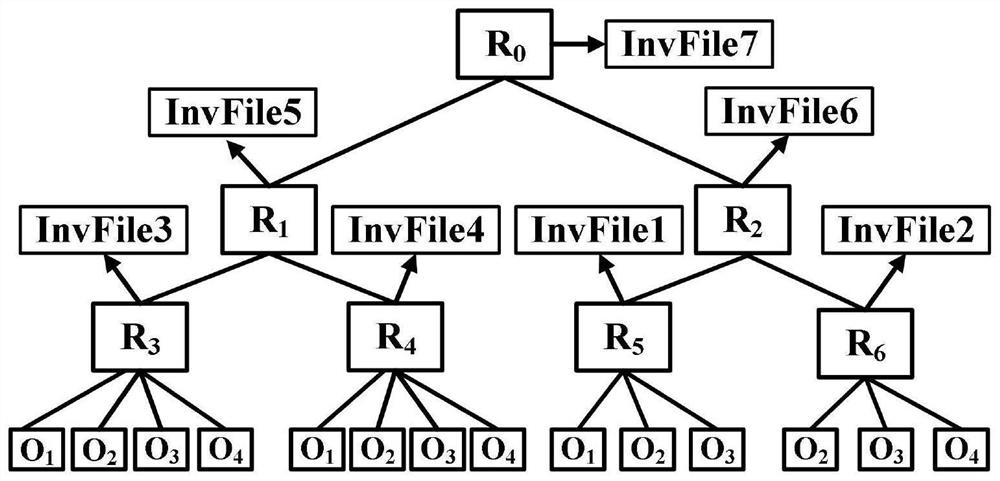
[0074] In this embodiment, the detection of indoor fire is taken as an example. The multi-attribute abnormal event detection method based on the cloud-edge fusion environment includes the following steps:
[0075] Step 1. Select a set of historical data for detecting indoor fires, and select data points from the historical data of detection equipment in a space area according to the time series at intervals of 1 min to obtain the original attribute information sequence; the attributes include temperature, smoke, CO, CO 2 , O 2 7, heat and watering amount, these 7 attributes are substituted into the multivariate logistic regression model of formula (1), and the regression coefficients of the 7 attributes are solved by maximum likelihood estimation, and temperature, smoke and CO are selected according to the regression coefficients from large to small The three attributes of concentration are used as the main attribute, that is, m=3;
[0076] Step 2. In order to make the edge n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com