Encrypted traffic detection method and device, and storage medium
A detection method and storage medium technology, applied in the field of network security, can solve problems such as deviation, large difference in model recognition rate, and difficulty in building a detection model, and achieve effective creation, accurate and efficient detection, and effective and accurate judgment Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
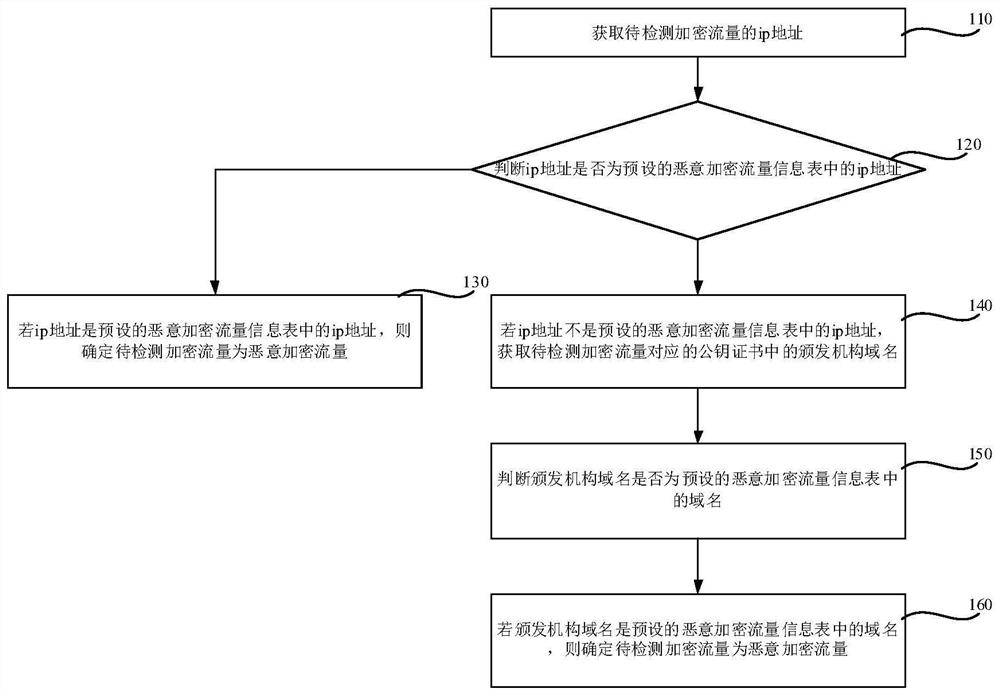
[0061] It is introduced in the foregoing embodiments that in the malicious encrypted traffic information table, each ip address corresponds to a malicious domain name. In order to realize a more accurate judgment, the judgment can also be made in combination with the malicious domain name corresponding to the ip address. Therefore, as an optional implementation, the detection method further includes: obtaining the domain name of the encrypted traffic to be detected, and correspondingly, step 130 includes: if the IP address is the IP address in the preset malicious encrypted traffic information table, judging Whether the domain name corresponding to the ip address in the preset malicious encrypted traffic information table is consistent with the domain name of the encrypted traffic to be detected; if the domain name corresponding to the ip address in the preset malicious encrypted traffic information table is consistent with the domain name of the encrypted traffic to be detected...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com