Network resource access control method based on identity authentication and data packet filtering technology
A technology of identity authentication and network resources, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of unfavorable fine-grained access control of network resources, inability to prevent illegal access control of network resources, illegal use of network resources, etc. To achieve the effect of preventing illegal access behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] In order to make the purpose, content and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
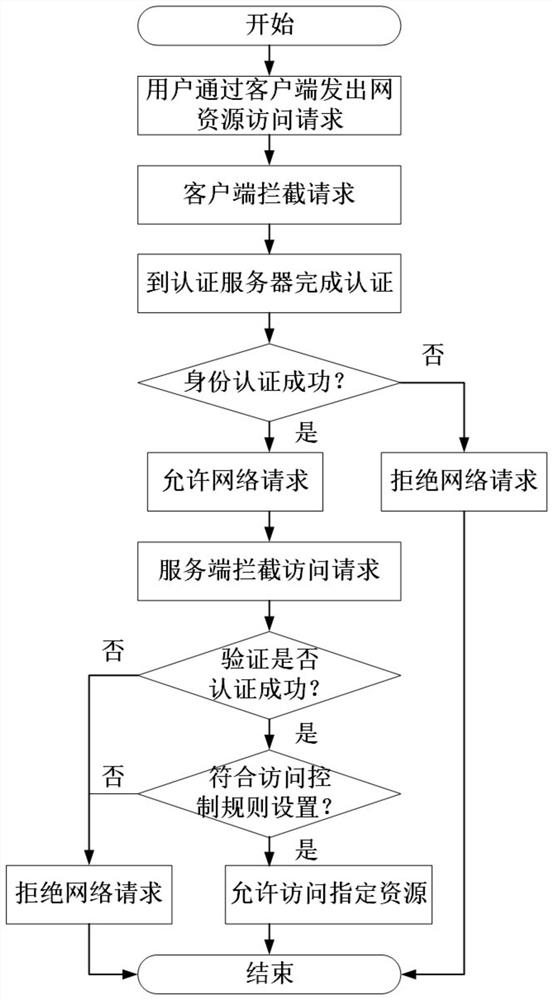
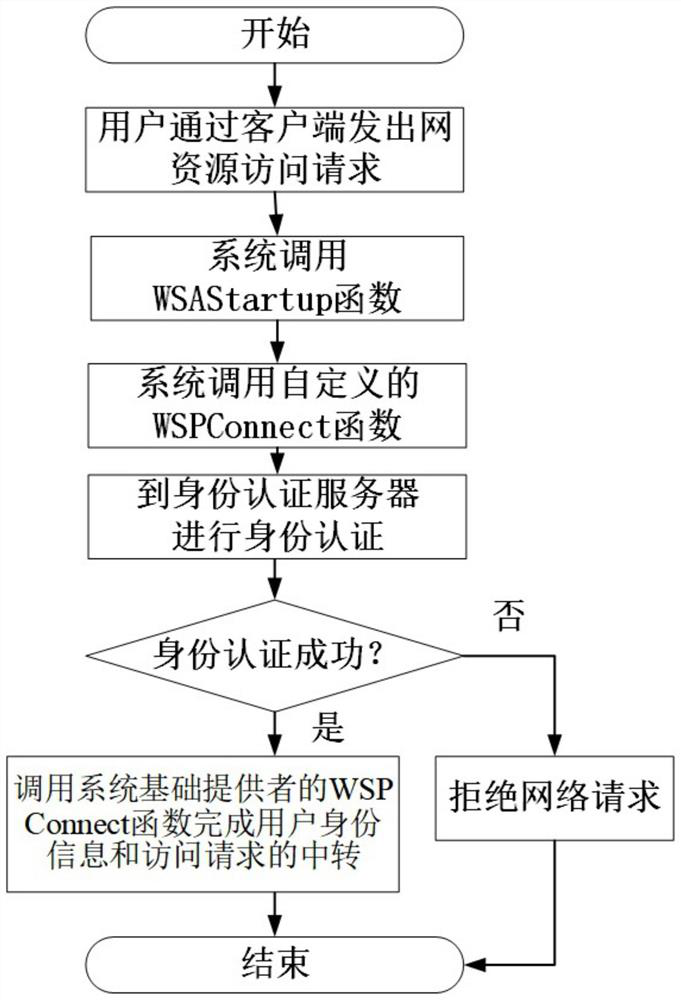
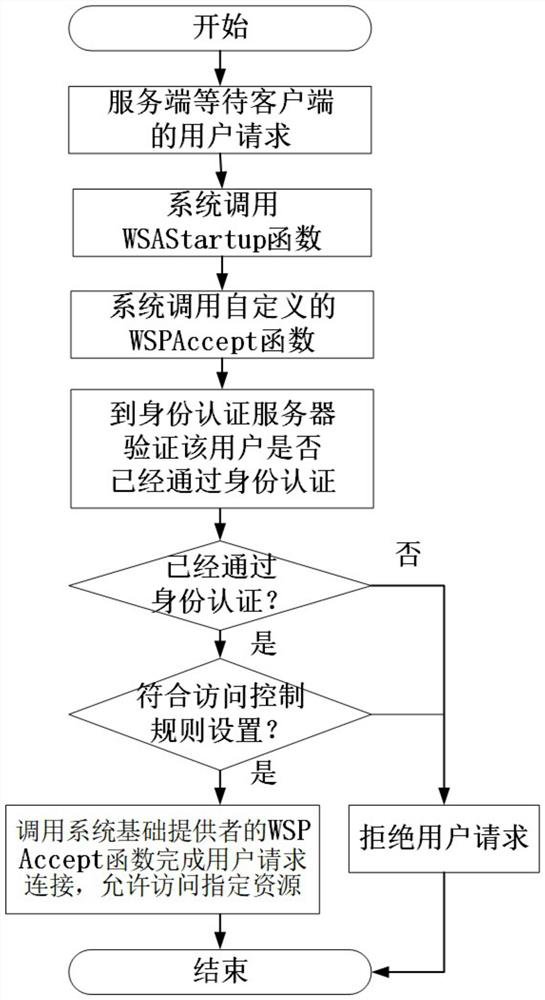
[0051] The purpose of the present invention is to propose a network resource access control method based on identity authentication and data packet filtering technology. Aiming at the above-mentioned problems in the prior art, the request for accessing network resources is combined with the user identity to achieve fine-grained Network resource access, and effective post-event audit analysis.
[0052] The basic principle of the present invention is to filter network access requests at the network resource access request initiator (client) and network resource access receiver (server), intercept the network request initiated by the user on the client, and require the user to complete identity authentication After the aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com