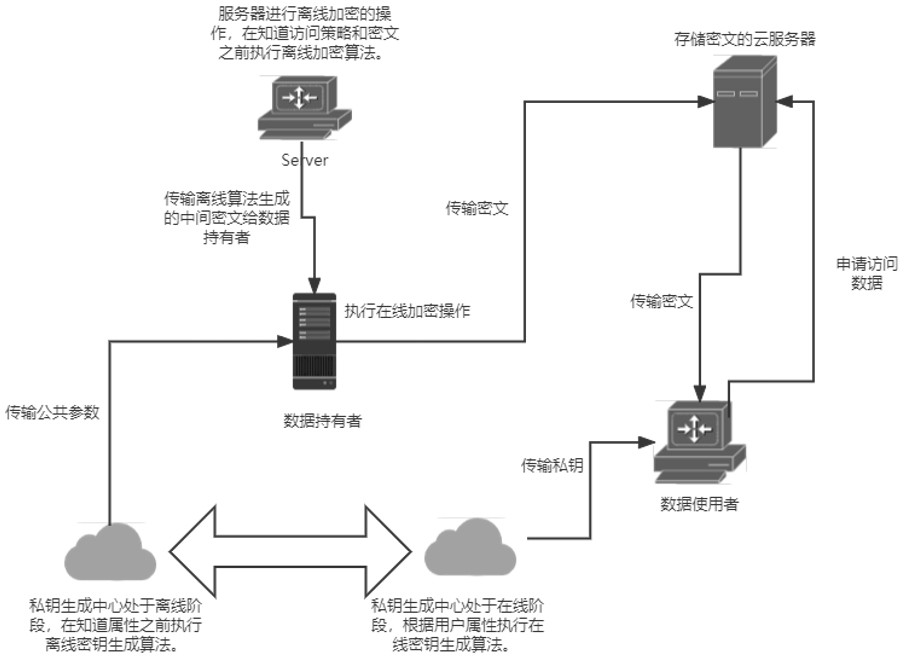
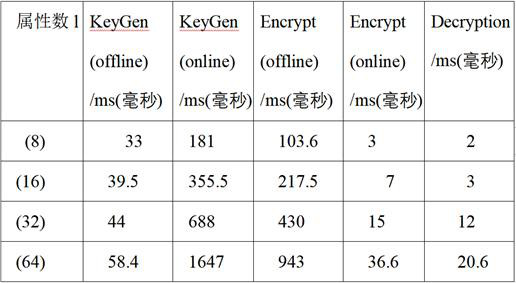
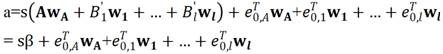Offline/Online Lattice-Based Attribute-Based Encryption
An attribute-based encryption and encryption algorithm technology, applied in the field of encryption, can solve the problems of weak computing power of lightweight devices, achieve the effects of reducing computing and storage complexity, high parallelism, and resisting quantum attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0076] The attacker L generates an access policy , and will Send to simulator M.
[0077] Simulator M receives Afterwards, the simulator M requests the oracle machine O, and obtains with .
[0078] for each , M requests the oracle machine O, and obtains .
[0079] for each , M requests the oracle machine O, and obtains , and then calculate .
[0080] for each , M requests the oracle machine O, and obtains , and then calculate .
[0081] Simulator M released . Keep not known.
[0082] Phase 1: Key query
[0083] Upon receiving a query with an attribute set S, if and , the simulator M outputs . Otherwise, for each , if S contains the attribute which is , M let ,otherwise . Then there must be a ,at this time Generated by TRAPGEN algorithm. Therefore M knows its Trapdoor, then the corresponding key can be calculated . L can make more than one query.
[0084] challenge
[0085] When the attacker L submits the message ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com