Color image encryption method based on composite chaotic mapping
A color image and chaotic mapping technology, which is applied in the direction of chaos model, image data processing, image data processing, etc., can solve the problems of small key space, short cycle, large amount of calculation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
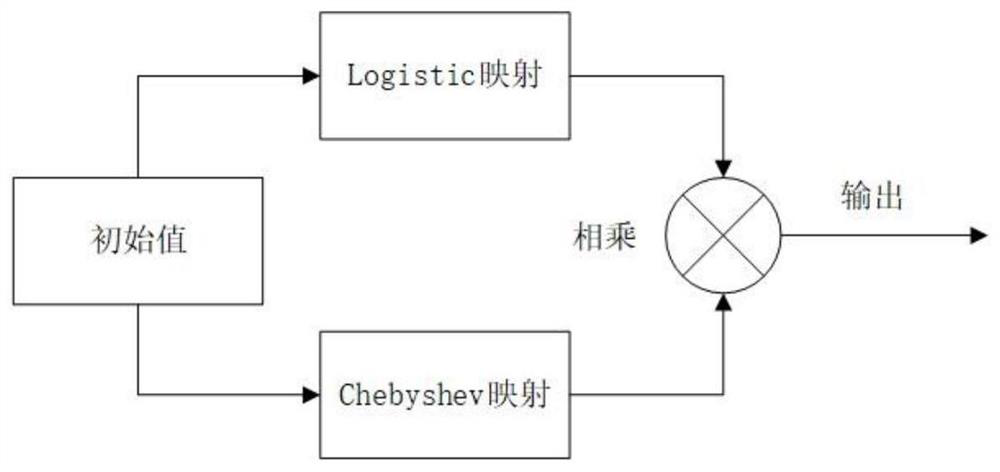
[0035] The present invention will be further described in detail in conjunction with the following specific embodiments and accompanying drawings. Key x during encryption 0 =y 0 =z 0 =C 0 = 0.1, m R =200, m B =300, m G =400, m 1 =500, R=2
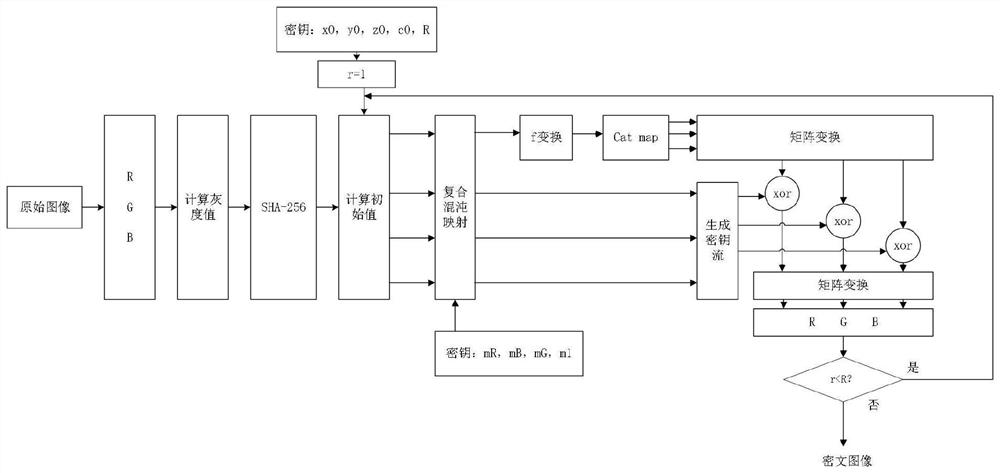
[0036] Such as figure 1 As shown, a color image encryption method based on compound chaotic map, the specific implementation is as follows:
[0037] Step 1. Take the color image of size N*N as the original image Image1, such as Figure 5 shown;
[0038] Step 2. Extract the three RGB components of the original image, and convert the original image into a matrix D R ,D G ,D B . And calculate the gray value matrix D of the image 1 ;
[0039] Step 3. According to the gray value matrix D 1 And SHA-256 produces a 256-bit binary Hash value L 0 ;
[0040] Step 4, the L 0 Segmentation, every 8 bits, can get 32 segmentation keys k i (i=1,2,...,32);
[0041] Step 5. Let the current number of rounds r=1, according to the segment...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap