Bidirectional authentication trusted starting system and method based on TPCM chip
A two-way authentication and start-up system technology, applied in the field of computer security, can solve problems such as system dishonesty, TPCM chip verification, and inability to guarantee the security of the computing environment, and achieve the effect of realizing security verification and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
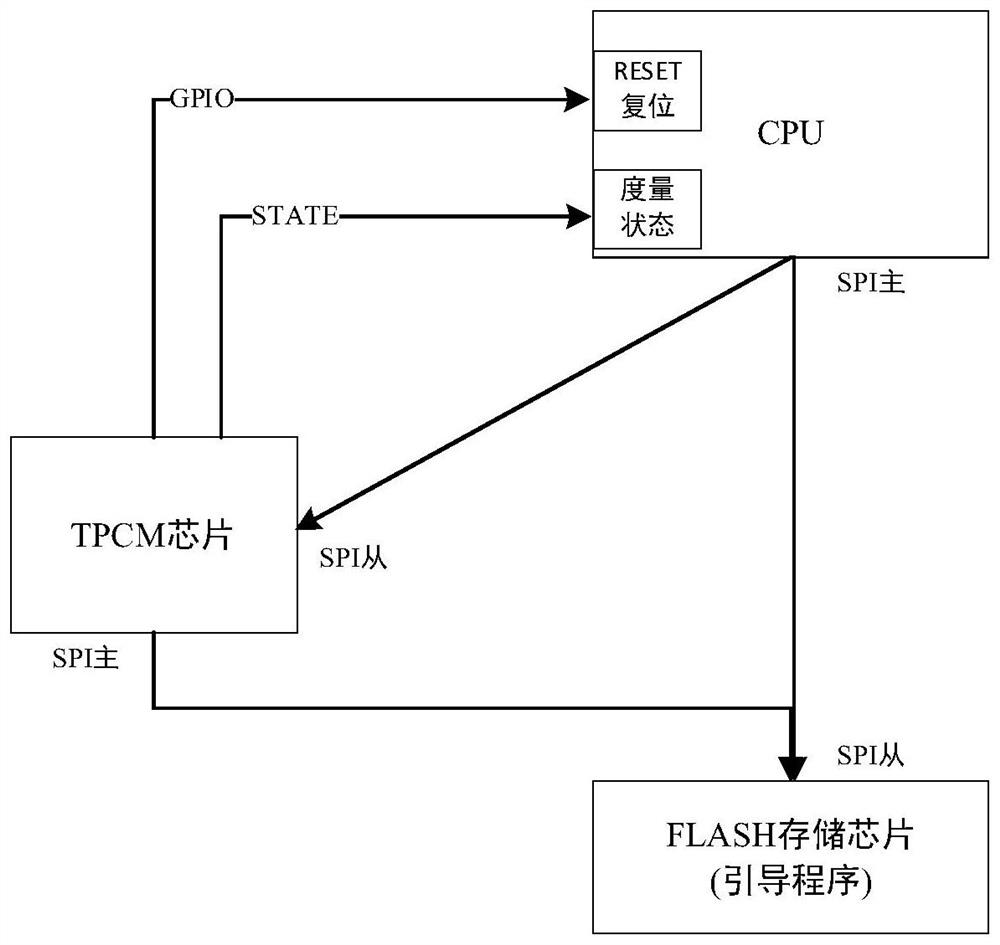
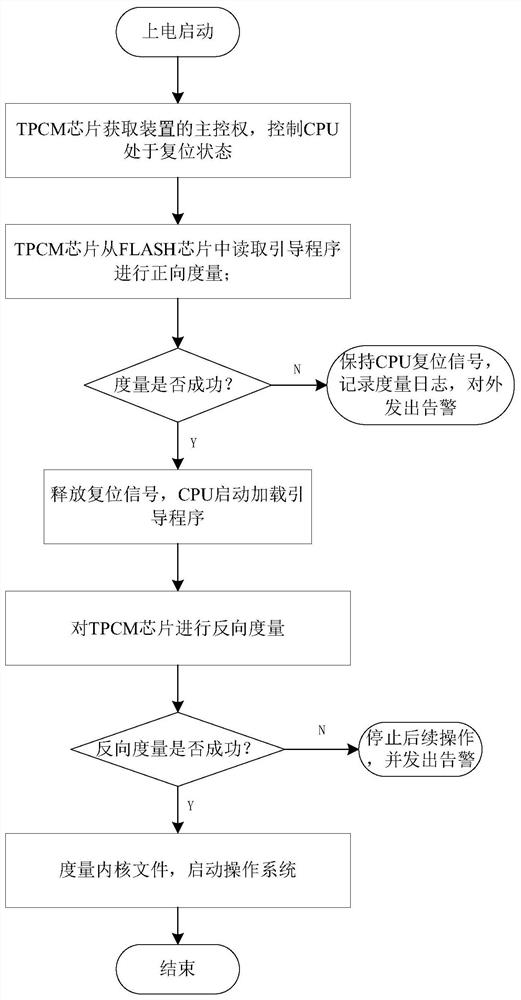
[0047] The invention performs reverse identity authentication on the TPCM chip after the boot program is started, supervises the trust root, and ensures the authenticity and credibility of the TPCM chip. Using the memory chip FLASH ID as a third-party trusted factor removes the public factor in identity authentication and prevents the public factor from being stolen or tampered with during the interaction. Realize the credible verification of the source of the trusted chain to ensure the security of the device operating environment.
[0048] Those skilled in the art should understand that the embodiments of the present application may be provided as methods, systems, or computer program products. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com