Safety verification method, device and system
A technology of security verification and identity verification, which is applied in the direction of user identity/authority verification, location information-based services, etc. It can solve problems such as insufficient proof of user legitimacy, easily leaked login password, cumbersome operation, etc., to improve security and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
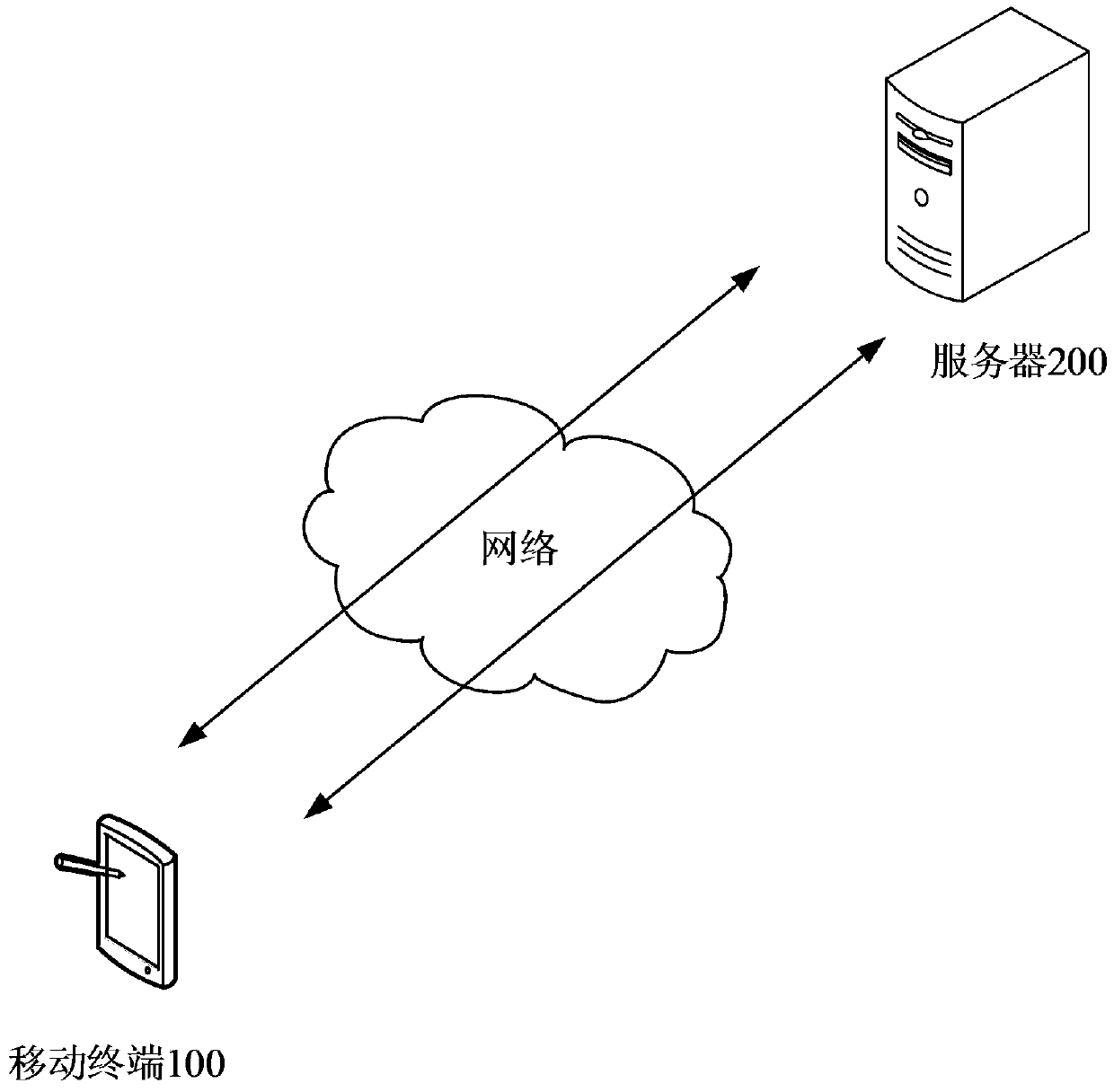
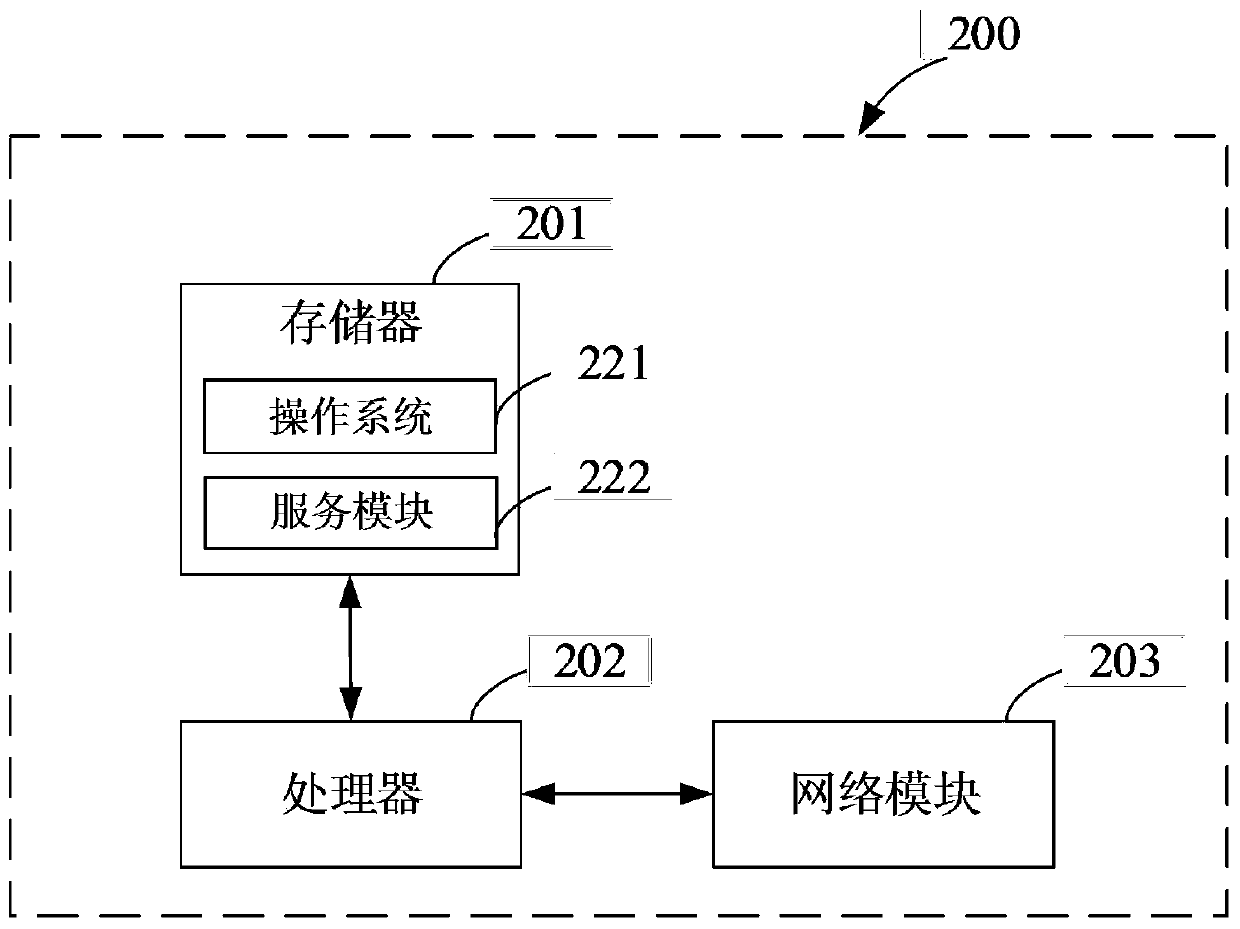
[0027] see Figure 1 to Figure 3 , figure 1 It is a schematic structural diagram of the security verification system provided by the first embodiment of the present invention. Such as figure 1 As shown, the security verification system 10 provided in this embodiment includes: a mobile terminal 100 and a server 200 . The mobile terminal 100 and the server 200 are located in a wired or wireless network, and the mobile terminal 100 and the server 200 perform data interaction through the wired or wireless network.
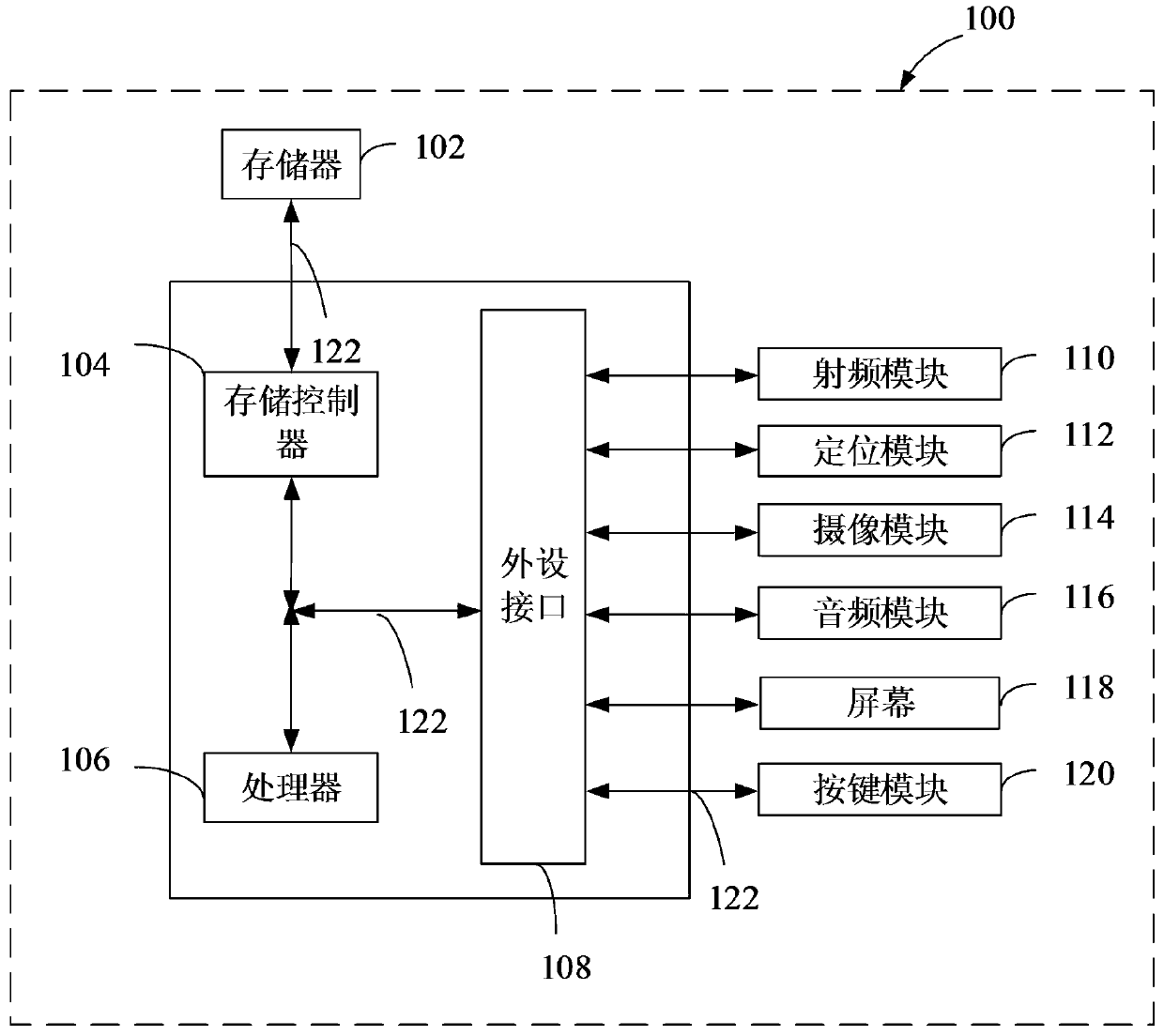
[0028] The mobile terminal 100 may include: a smart phone with a positioning function, a tablet computer, an e-book reader, an MP3 player (Moving Picture Experts Group Audio Layer III, moving picture expert compression standard audio layer 3), MP4 (Moving Picture Experts Group Audio Layer IV, Motion Picture Expert Compression Standard Audio Layer 4) Players, Laptops, Car PCs, Wearables, etc.
[0029] In this embodiment, the mobile terminal 100 is configured to send...
no. 2 example
[0052] see Figure 4 , Figure 4 It is a flow chart of the security verification method provided by the second embodiment of the present invention. The following is a detailed description of the security verification method provided by this embodiment from the server side, as Figure 4 As shown, the security verification method provided in this embodiment includes the following steps:
[0053] Step S21, the server receives the service operation request sent by the mobile terminal, and judges whether the service operation requested by the mobile terminal is a sensitive operation;
[0054] Sensitive operations refer to operations performed on related businesses that may involve the user's personal privacy or property security, such as: login, password change, electronic payment, electronic transfer, etc.
[0055] In this embodiment, a verification database may be preset in the server 200, and the verification database is preset with: user accounts, type information of sensiti...
no. 3 example
[0076] see Figure 5 to Figure 9 , Figure 5 It is a flow chart of the security verification method provided by the third embodiment of the present invention. The following is a detailed description of the security verification method provided by this embodiment from the server side, as Figure 5 As shown, the security verification method provided in this embodiment includes the following steps:
[0077] Step S31, the server executes the configuration operation according to the configuration information sent by the mobile terminal and the configuration operation request, and binds the user account, the type of sensitive operation and the preset location information as the verification standard in the configuration information;
[0078] Specifically, see Figure 6 , this step can include:
[0079] Step S311, the server receives the user account, the first identity verification information and the identity verification request sent by the mobile terminal, and matches the fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com